From Nikto version 2.1.1, the community allowed developers to debug and call specific plugins. The same can be customized accordingly from version 2.1.2. The listing can be done for all the plugins, and then you specify a specific plugin to perform any scan. There are currently around 35 plugins that can be utilized by penetration testers; the following screenshot provides the list of plugins that are currently available in the latest version of Nikto:

For example, if attackers found a banner information as Apache server 2.2.0, Nikto can be customized to run specific plugins only for Apache user enumeration by running the following command:
nikto.pl -host target.com -Plugins "apacheusers(enumerate,dictionary:users.txt);report_xml" -output apacheusers.xml
Attackers can also point Nikto scans to burp or any proxy tool by nikto.pl -host <hostaddress> -port <hostport> -useragentnikto -useproxy http://127.0.0.1:8080.
Penetration testers should be able to see the following information:

When the Nikto plugin is run successfully, the apacheusers.xml output file should include the active users on the target host.
Similar to Nikto, Vega also allows us to customize the scanner by navigating to the window and selecting Preferences, where one can set up general proxy configuration or even point the traffic to a third-party proxy tool. However, Vega has its own proxy tool that can be utilized. The following screenshot provides the scanner options that can be set before beginning any web application scan:
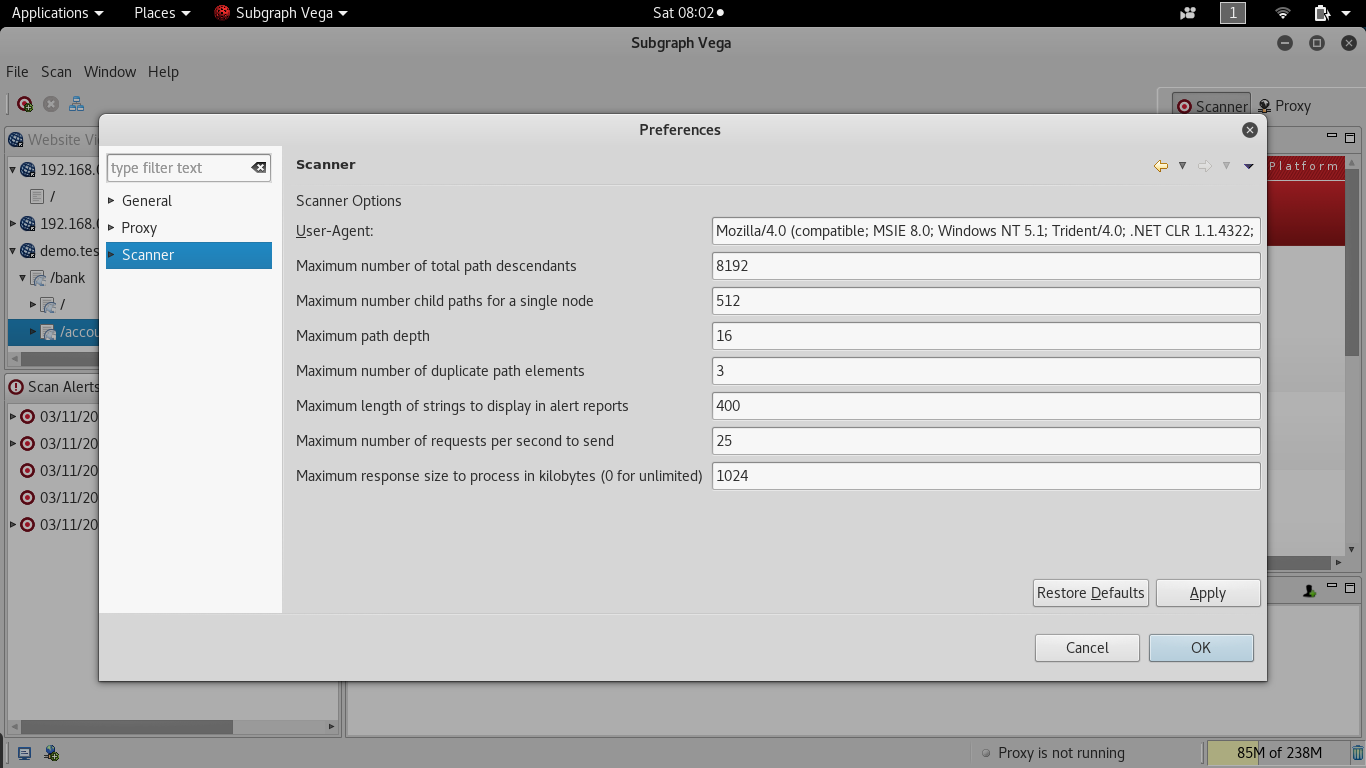
Attackers can define their own User-Agent or mimic any well-known User-Agent headers, such as IRC bot or Google bot, and also configure the maximum number of total descendants and sub processes, and the number of paths that can be traversed; for example, if the spider reveals www.target.com/admin/, there is a dictionary to add to the URL as www.target.com/admin/secret/ and the maximum by default is set to 16, but attackers would be able to drill down by utilizing other tools to maximize the effectiveness of Vega and would select precisely the right number of paths and, also, in case of any protection mechanisms in place such as WAF or Network level IPS, pentesters can select to scan the target with a slow rate of connections per second to send to the target. One can also set the maximum number of the response size; by default, it is set to 1 MB (1,024 KB).
Once the preferences are set, the scan can be further customized while adding a new scan. When penetration testers click on New Scan, enter the base URL to scan, and click Next, the following screen should allow the testers to customize the scan:
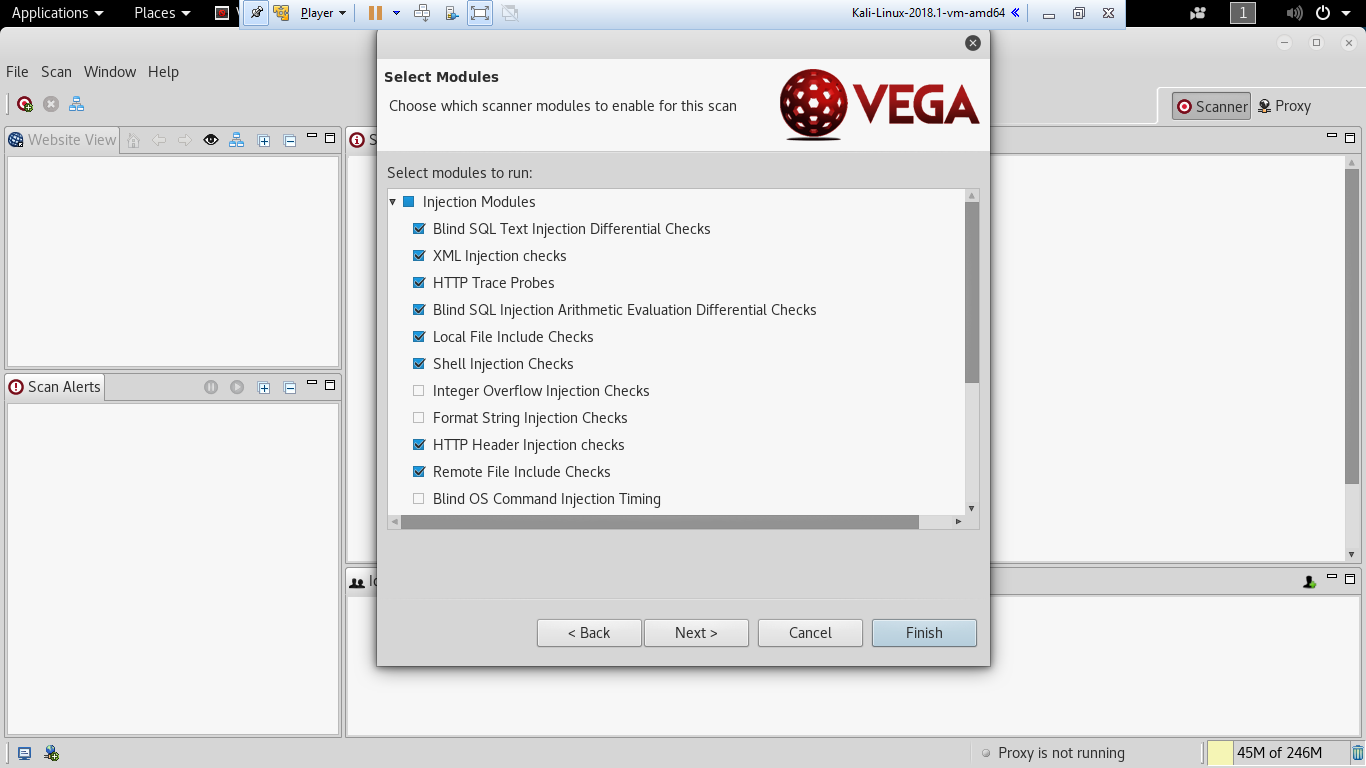
Vega provides two sections to customize: one is Injection Modules and the other is Response Processing Modules:
- Injection Modules: This includes a list of exploit modules that are available as part of built-in Vega web vulnerability databases and it queries in-built to test the target for those vulnerabilities such as Blind SQL injection, XSS, Remote file inclusion, local file inclusion, and header injections.
- Response Processing Modules: These include a list of security misconfigurations that can be picked up as part of the HTTP response such as directory listing, error pages, cross-domain policies, and version control strings. Vega also supports testers adding their own plugin modules (https://github.com/subgraph/Vega/).
