The Internet Protocol (IP) address, is a unique number used to identify devices that are connected to a private network or the public internet. Today, the internet is largely based on version 4, IPv4. Kali includes several tools to facilitate DNS reconnaissance, as given in the following table:
|
Application |
Description |
|
dnsenum, dnsmap, and dnsrecon |
These are comprehensive DNS scanners—DNS record enumeration (A, MX, TXT, SOA, wildcard, and so on), subdomain brute-force attacks, Google lookup, reverse lookup, zone transfer, and zone walking. dsnrecon is usually the first choice—it is highly reliable, results are well parsed, and data can be directly imported into the Metasploit framework. |
|
dnstracer |
This determines where a given DNS gets its information from, and follows the chain of DNS servers back to the servers that know the data. |
|
dnswalk |
This DNS debugger checks specified domains for internal consistency and accuracy. |
|
fierce |
This locates non-contiguous IP space and hostnames against specified domains by attempting zone transfers and then attempting brute-force attacks to gain DNS information. |
During testing, most investigators run fierce to confirm that all possible targets have been identified, and then run at least two comprehensive tools (for example, dnsenum and dnsrecon) to generate the maximum amount of data and provide a degree of cross-validation.
In the following screenshot, dnsrecon is used to generate a standard DNS record search and a search that is specific for SRV records. An excerpt of the results is shown for each case:
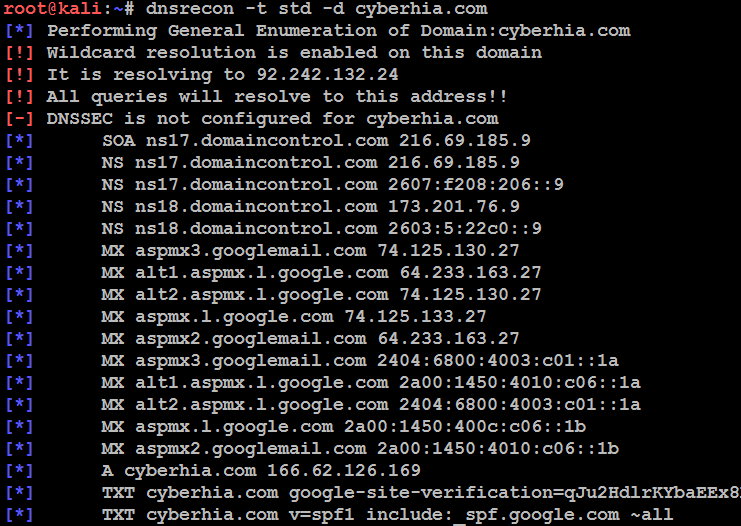
dnsrecon allows the penetration tester to obtain the SOA record, Name Servers (NS), mail exchanger (MX) hosts, servers sending emails using Sender Policy Framework (SPF), and the IP address ranges in use.
