Once a system has been exploited, the attacker must cover their tracks to avoid detection, or at least make reconstruction of the event more difficult for the defender.
An attacker may completely delete the Windows event logs (if they are being actively retained on the compromised server). This can be done via a command shell to the system, using the following command:
C:> del %WINDIR%*.log /a/s/q/f
The command directs for all of the logs to be deleted (/a), including all files from subfolders (/s). The /q option disables all of the queries, asking for a yes or no response, and the /f option forcibly removes the files, making recovery more difficult.
To wipe out specific recorded files, attackers must keep track of all the activities that have been performed on the compromised system.
This can also be done from the Meterpreter prompt by using clearev. As shown in the following screenshot, this will clear the application, system, and security logs from the target (there are no options or arguments for this command):
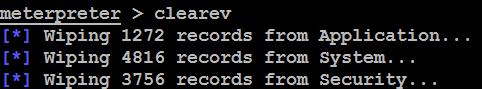
Ordinarily, deleting a system log does not trigger any alerts to the user. In fact, most organizations configure logging so haphazardly that missing system logs are treated as a possible occurrence, and their loss is not investigated thoroughly.
Apart from the traditional logs, attackers might also consider removing the PowerShell Operational log from the victim systems.
Metasploit has an additional trick up its sleeve: the timestomp option allows an attacker to make changes to the MACE parameters of a file (the last modified, accessed, created, and MFT entry modified times of a file). Once a system has been compromised and a Meterpreter shell established, timestomp can be invoked, as shown in the following screenshot:
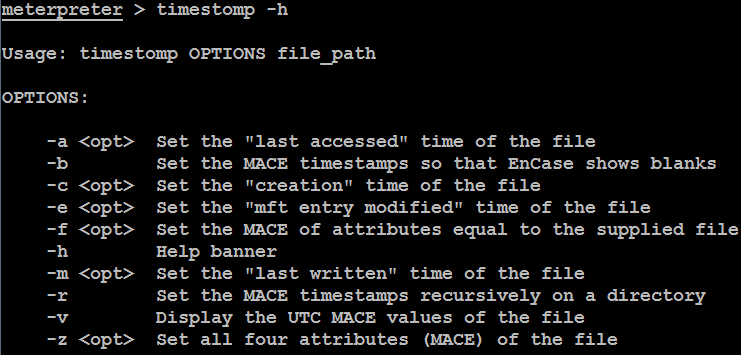
For example, C: of the compromised system contains a file named README.txt. The MACE values for this file indicate that it was created recently, as shown in the following screenshot:
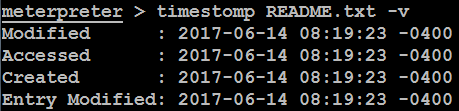
If we wanted to hide this file, we could move it to a cluttered directory, such as WindowsSystem32. However, the file would be obvious to anyone who sorted the contents of that directory on the basis of the creation dates or another MAC-based variable.
Instead, you can change the timestamps of the file by running the following command:
meterpreter > timestomp -z "01/01/2001 10:10:10" README.txt
This changes the timestamps of the README.txt, as shown in the following screenshot:

In order to completely foul up an investigation, an attacker may recursively change all of the set times in a directory or on a particular drive using the following command:
meterpreter> timestomp C:\ -r
The solution is not perfect. It is very obvious that an attack has occurred. Furthermore, it is possible for timestamps to be retained in other locations on a hard drive and be accessible for investigation. If the target system is actively monitoring changes to system integrity using an intrusion detection system such as Tripwire, alerts of the timestomp activity will be generated. Therefore, destroying timestamps is of limited value when a truly stealthy approach is required.
