Gophish is an integrated phishing framework with open source and also commercial support. The framework makes it easy for any type of user to quickly create a phishing campaign and deploy a sophisticated phishing simulation, or perform a real attack within a few minutes. Unlike SET, Gophish is not preinstalled in Kali Linux. In this section, we will explore how to set up the environment:
- Download the right release, according to your system configuration, by visiting https://github.com/gophish/gophish/releases. In this book, we will utilize the gophish-v0.7.1 64-bit Linux version.
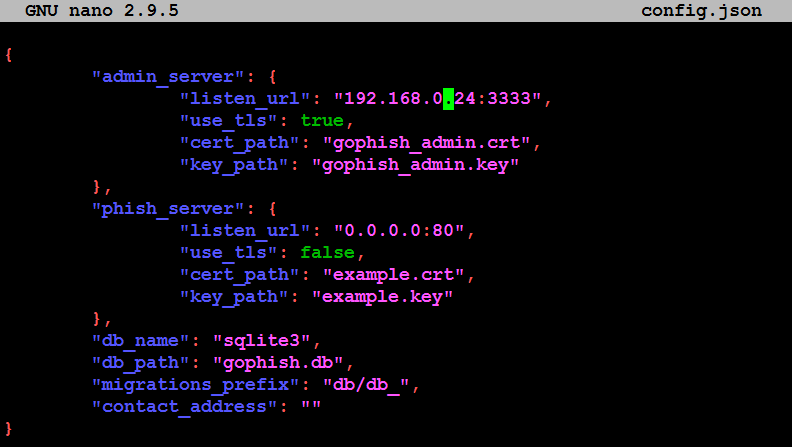
- Once the app is download to Kali Linux, we will unzip the folder and configure the config.json file with the right information; attackers can choose to utilize any custom database, such as MySQL, MSSQL, and so on. We will use sqlite3 and an explicit IP address must be declared in listen_url if testers prefer to share the same resource over the LAN, as shown in the following screenshot. By default, it will be exposed only to localhost:
- The next step is run the application in the Terminal using ./gophish; this should bring up BeEF web application portal on default port 3333 with a self-signed SSL certificate.
- You should now be able to access the application by visiting https://yourIP:3333, as shown in the following screenshot, and you should now be able to log in with the user as admin and the password as gophish; it is recommended once you log in, you change the default password: