RFID stands for Radio Frequency Identification, which utilizes radio waves to identify items. At a minimum, the RFID system contains a tag, a reader, and an antenna. There are active and passive RFID tags. Active RFID tags contain their own power source, giving them the ability to broadcast with a read range of up to 100 meters. Passive RFID tags do not have their own power source. Instead, they are powered by the electromagnetic energy transmitted from the RFID reader.
NFC stands for near field communications, which is a subset of RFID but with high-frequency. Both NFC/RFID operate at 13.56 MHz. NFC is also designed to run as an NFC reader and also NFC tag, which is the unique feature of NFC devices to communicate with peers. In this section, we will explore one of the devices that comes in handy during a physical penetration testing/social engineering or a red team exercise to achieve a set objective. For example, if you are signed up to showcase the real threats of an organization that includes gaining access to an organization's office premises or data centers or boardrooms, Chameleon Mini comes in handy to store six different UIDs in a credit card-sized portable device:

The Chameleon Mini is a device created by Kasper & Oswald, designed to analyze the security issues around NFC to emulate and clone contactless cards, read RFID tags, and also sniff RF data. For developers, it is freely programmable. This device can be purchased online at: https://shop.kasper.it/. In this example, we have used Chameleon Mini RevG color to demonstrate cloning a UID.
In Kali Linux, we can validate the device by directly connecting with the USB. The lsusb command should display the Chameleon Mini as MCS and every serial device connected Kali Linux will be listed in /dev/, in this case our device is visible as a serial port named ttyACM0, as shown in the following screenshot:
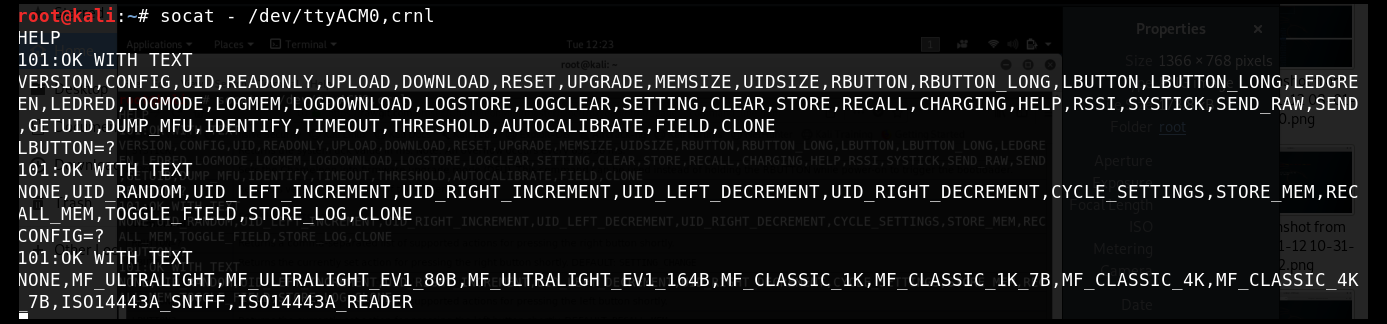
We can communicate to the serial port directly using socat by running socat - /dev/ttyACM0, crnl as shown in the following screenshot:
You will require the card that you want to clone. One-step action can also be performed straight by placing the card to be cloned on the Chameleon Mini. Tester's straight can type CLONE and the job is done as shown in the following screenshot:
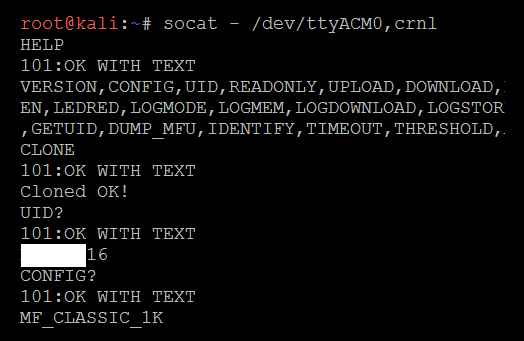
The following details provide the manual way of doing it:
- Command line
- Once the serial port communication is established between Kali and the device, type the HELP command to display all the available commands for Chameleon Mini.
- Chameleon Mini comes with eight slots, each of which can act as an individual NFC card. The slots can be set by using the SETTINGS= command. For example, we can set the slot to 2 by typing the settings=2 command; it should return as 100:OK.
- Run CONFIG? to see the current configuration. The new device should return the following:
101:OK WITH TEXT
NONE
- The next step is to enable the card reader into 'reader' mode. This can be achieved by typing CONFIG=ISO14443A_READER.
- Now we can place the card that needs to be cloned on the card reader and type the Identify command.
- Once you identify the type of the card, you can now set the configuration using the CONFIG command: in our case, it is MIFARE Classic 1K, so we will run CONFIG= MF_CLASSIC_1K.
- Now we have set the configuration, we can steal the UID from the card and then add to our Chameleon Mini by running UID=CARD NUMBER, as shown in the following screenshot:
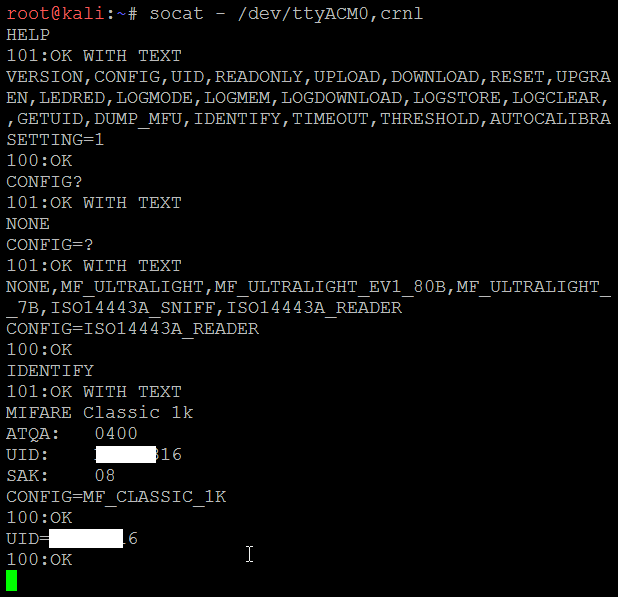
- We are now all set to use the Chameleon Mini as a card.
- Pentesters can also pre-program this to perform the cloning tasks with the use of two buttons that come along with the device whilst on the move. For example, during social engineering, while the testers talk to the victim-company's staff, they click the button and clone their ID cards (NFC). This can be performed by the following commands:
- LBUTTON=CLONE: This will set a click on the left-hand button to clone the card.
- RBUTTON=CYCLE_SETTINGS: This will set a click of the right button to rotate the slots. For example, if CARD A is cloned to slot 1 and you wanted to clone another card, this can be performed by clicking the right-hand button that will move the slots, for instance, to slot 2. Then, you can go ahead and press the left-hand button to clone another CARD B.
