Administrator privileges allow an attacker to create and manage accounts and access most data available on a system. However, some complex functionality mandates that the requester have system-level access privileges. There are several ways to continue this escalation to the system level. The most common is to use the at command, which is now deprecated due to security reasons and used by Windows to schedule tasks for a particular time. The at command always runs with privileges at the system level; however, these now run in non-interactive mode only:

Using an interactive shell (enter shell at the Meterpreter prompt), open a Command Prompt and determine the compromised system's local time. If the time is 12:50 (the at function uses the 24-hour notation), schedule an interactive command shell for a later time, as shown in the following screenshot:

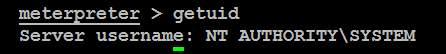
After the at task is scheduled to run, reconfirm your access privileges at the Meterpreter prompt, as shown in the following screenshot:
By default, Windows 7 and Windows 2008 don't allow remote access to administrative shares—such as ADMIN$, C$, and so on—from untrusted systems. These shares may be required for Meterpreter scripts, such as Incognito, or to support attacks over Server Message Block (SMB). To address this issue, add HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionPoliciesSystem to the registry, and add a new DWORD (32-bit) key named LocalAccountTokenFilterPolicy and set the value to 1.
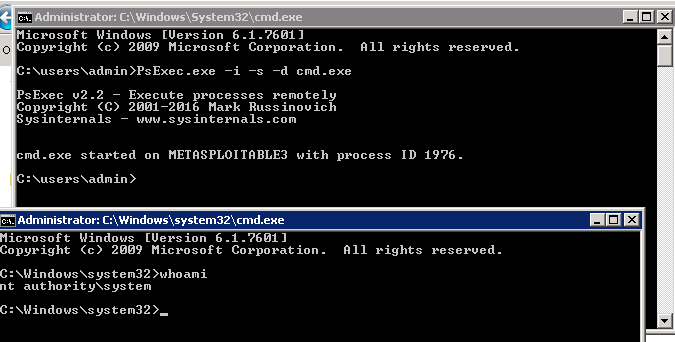
An alternative is to run PsExec to get system-level access by uploading PsExec to the desired folder and run the following command as local administrator:
PsExec -s -i -d cmd.exe
This command should open up another Command Prompt as system user, as shown in the following screenshot: