The final attack against wireless networks that we'll evaluate is DoS attacks, where an attacker deprives a legitimate user of access to a wireless network or makes the network unavailable by causing it to crash. Wireless networks are extremely susceptible to DoS attacks, and it is difficult to localize the attacker on a distributed wireless network. Examples of DoS attacks include the following:
- Injecting crafted network commands, such as reconfiguration commands, on to a wireless network can cause the failure of routers, switches, and other network devices.
- Some devices and applications can recognize that an attack is taking place and will automatically respond by disabling the network. A malicious attacker can launch an obvious attack and then let the target create the DoS itself!
- Bombarding the wireless network with a flood of data packets can make it unavailable for use; for example, an HTTP flood attack making thousands of page requests to a web server can exhaust its processing ability. In the same way, flooding the network with authentication and association packets blocks users from connecting to the access points.
- Attackers can craft specific deauthentication and disassociation commands, which are used in wireless networks to close an authorized connection and flood the network, thereby stopping legitimate users from maintaining their connection to a wireless access point.
To demonstrate this last point, we will create a DoS attack by flooding a network with de-authentication packets. Because the wireless 802.11 protocol is built to support de-authentication upon the receipt of a defined packet (so that a user can break a connection when it is no longer required), this can be a devastating attack—it complies with the standard, and there is no way to stop it from happening.
The easiest way to bump a legitimate user off a network is to target them with a stream of de-authentication packets. This can be done with the help of the aircrack-ng tool suite:
root@kali:~# aireplay-ng -0 0 -a (bssid) -c wlan0
This command identifies the attack type as -0, indicating that it is for a de-authentication attack. The second 0 (zero) launches a continuous stream of de-authentication packets, making the network unavailable to its users.
The Websploit framework is an open source tool that's used to scan and analyze remote systems. It contains several tools, including tools that are specific to wireless attacks. To launch it, open a command shell and simply type websploit. It can be installed by running apt-get install websploit in the Terminal.
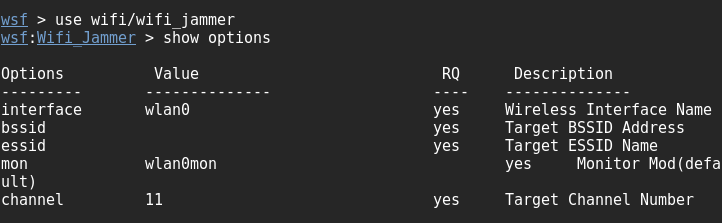
The Websploit interface is similar to that of recon-ng and the Metasploit framework, and it presents the user with a modular interface.
Once launched, use the show modules command to see the attack modules that are present in the existing version. Select the Wi-Fi jammer (a stream of de-authentication packets) using the use wifi/wifi_jammer command. As shown in the following screenshot, the attacker just has to use the set commands to set the various options and then select run to launch the attack: