When the BeEF control panel is launched, it will present the Getting Started screen, featuring links to the online site as well as the demonstration pages that can be used to validate the various attacks. The BeEF control panel is shown in the following screenshot:
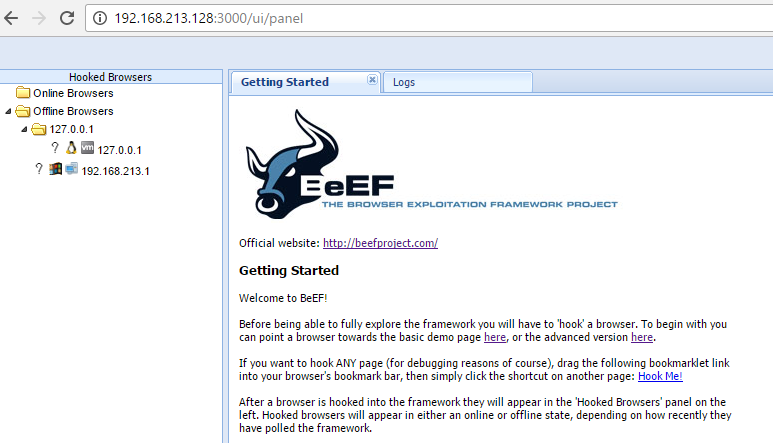
If you have hooked a victim, the interface will be divided into two panels:
- On the left-hand side of the panel, we have Hooked Browsers; the tester can see every connected browser listed with information about its host operating system, browser type, IP address, and installed plugins. Because BeEF sets a cookie to identify victims, it can refer back to this information and maintain a consistent list of victims.
- The right-hand side of the panel is where all of the actions are initiated and the results are obtained. In the Commands tab, we see a categorized repository of the different attack vectors that can be used against hooked browsers. This view will differ based on the type and version of each browser.
BeEF uses a color-coding scheme to characterize the commands on the basis of their usability against a particular target. The colors used are as follows:
- Green: This indicates that the command module works against the target and should be invisible to the victim.
- Orange: This indicates that the command module works against the target, but it may be detected by the victim.
- Gray: This indicates that the command module is not yet verified against the target.
- Red: This indicates that the command module does not work against the target. It can be used, but its success is not guaranteed, and its use may be detected by the target.
Take these indicators with a grain of salt, since variations in the client environment can make some commands ineffective, or may cause other unintended results.
To start an attack or hook a victim, we need to get the user to click on the hook URL, which takes the form of <IP ADDRESS>:<PORT>/hook.js. This can be achieved using a variety of means, including:
- The original XSS vulnerabilities
- Man-in-the-middle attacks (especially the ones using BeEF Shank, an ARP spoofing tool that specifically targets intranet sites on internal networks)
- Social engineering attacks, including the BeEF web cloner and mass emailer, custom hook point with iFrame impersonation, or the QR code generator
Once the browser has been hooked, it is referred to as a zombie. Select the IP address of the zombie from the Hooked Browsers panel on the left-hand side of the command interface and then refer to the available commands.
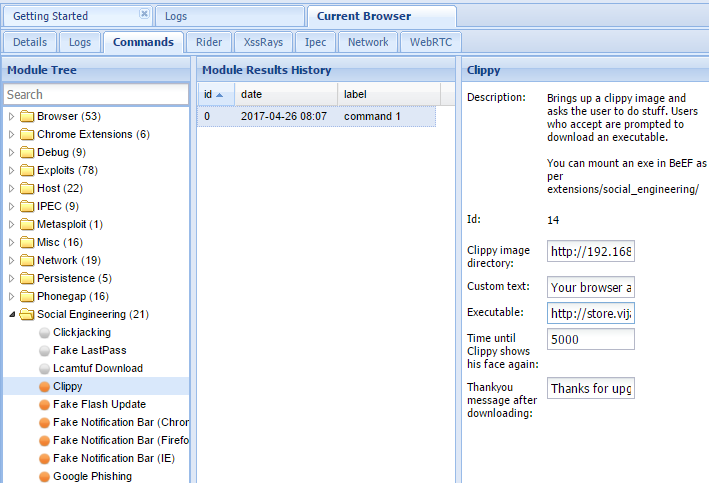
In the example shown in the following screenshot, there are several different attacks and management options available for the hooked browser. One of the easiest attack options to use is the social engineering Clippy attack.
When Clippy is selected from Module Tree under Commands, a specific Clippy panel is launched on the far right, as shown in the following screenshot. It allows you to adjust the image, the text delivered, and the executable that will be launched locally if the victim clicks on the supplied link. By default, the custom text informs the victim that their browser is out of date, offers to update it for them, downloads an executable (nonmalicious), and then thanks the user for performing the upgrade. All of these options can be changed by the tester:
When Clippy is executed, the victim will see a message, as shown in the following screenshot, on their browser:
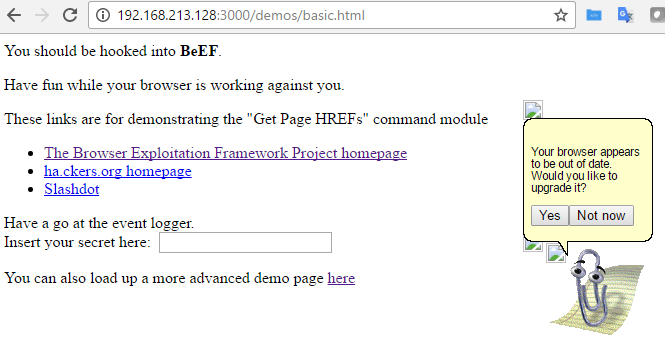
This can be a very effective social engineering attack. When testing with clients, we have had success rates (the client downloaded a nonmalicious indicator file) of approximately 70 percent.
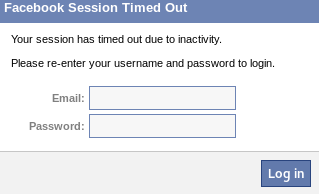
One of the more interesting attacks is Pretty Theft, which asks users for their username and password for popular sites. For example, the Pretty Theft option for Facebook can be configured by the tester, as shown in the following screenshot:

When the attack is executed, the victim is presented with a pop up that appears to be legitimate, as shown in the following screenshot:
In BeEF, the tester reviews the history log for the attack and can derive the username and password from the data field in the Command results column, as shown in the following screenshot:

Another attack that can be quickly launched is old-fashioned phishing; once the browser is hooked to BeEF, it's fairly simple to redirect the users to an attacker-controlled website.
