You can utilize the existing SSH connection and port forwarding techniques to bypass any restrictions set by the security policy or device in place.
When we try and access the following example, it showcases that there is a URL filtering device in place that prevents us from accessing certain websites, as shown in the following screenshot:

This can be bypassed using one of the tunneling tools; in this case, we will utilize portable software called PuTTY:
- Open the PuTTY menu.
- Click on Tunnels from the Connection tab
- Enter the local port as 8090 and add the remote port as any, as shown in the following screenshot:
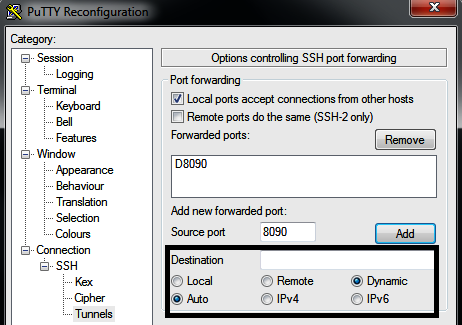
This has now enabled internet access to your internal to external system, which means all the traffic on port 8090 can now be forwarded through the external system at 61.x.x.142:
- The next step is to go to Internet Options | LAN connections | Advanced | SOCKs and enter 127.0.0.1 in Proxy address to use and 8090 in Port, as shown in the following screenshot:
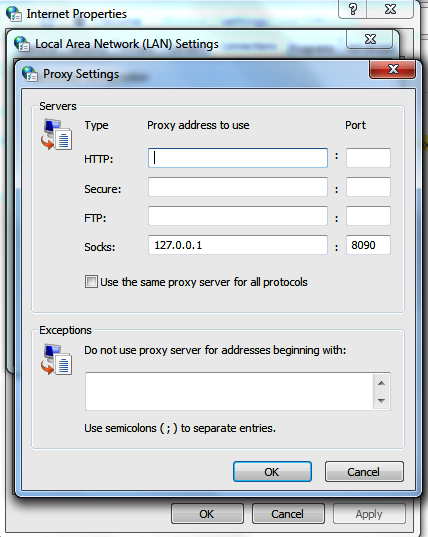
Now that the proxy is pointed to the remote machine, you will be able to access the website without being blocked by the proxy or any URL filtering device, as shown in the following screenshot. This way, penetration testers can bypass the URL filtering in place and also exfiltrate the data to the public cloud, the hacker's hosted computer, or blocked websites: