The first step to understanding Google Hacking Database is that the testers must understand all the advanced Google operators, just like how machine-level programming engineers must understand computer OP codes. These Google operators are part of the Google query process, and the syntax of searching is as follows:
operator:itemthatyouwanttosearch
There is no space between operator, the colon (:), and itemthatyouwanttosearch. The following table lists all the advanced Google operators:
|
Operator |
Description |
Mixes with other operators? |
Can be used alone? |
|
intitle |
Page title keyword search |
Yes |
Yes |
|
allintitle |
All keywords search at a time in the title |
No |
Yes |
|
inurl |
Search the keyword in the URL |
Yes |
Yes |
|
site |
Filter Google search results only to the site |
Yes |
Yes |
|
ext or filetype |
Search for particular extension or file type |
Yes |
No |
|
allintext |
Keyword search for all number of occurrences |
No |
Yes |
|
link |
External link search on a page |
No |
Yes |
|
inanchor |
Search anchor link on a web page |
Yes |
Yes |
|
numrange |
Limit search on the range |
Yes |
Yes |
|
daterange |
Limit search on the date |
Yes |
Yes |
|
author |
Finding group author |
Yes |
Yes |
|
group |
Searching group names |
Yes |
Yes |
|
related |
Search related keywords |
Yes |
Yes |
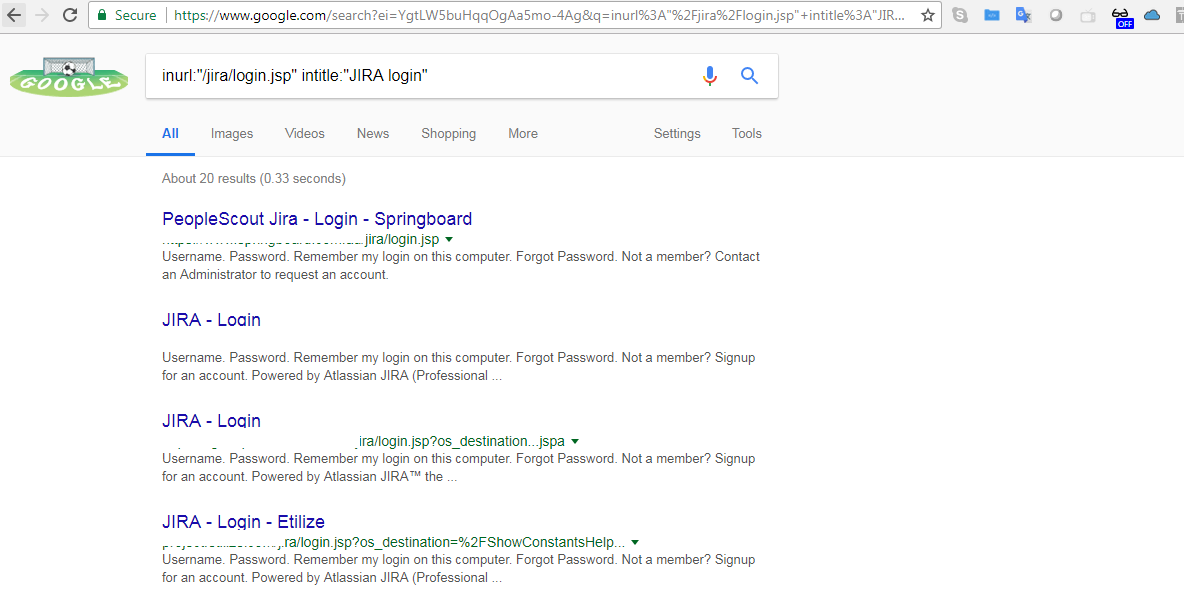
The following screenshot provides a simple Google dork to search for the username in a log file.
The dork search is inurl:"/jira/login.jsp" intitle:"JIRA login":
For more specific operators, we can refer to the guide from Google at http://www.googleguide.com/advanced_operators_reference.html, and we can utilize the Google hacking database from exploit-db, which is constantly updated by the security research community, available at https://www.exploit-db.com/google-hacking-database/.
