Macro Security
Macros can save time and energy, but an ill-conceived macro can (intentionally or unintentionally) destroy data and otherwise wreak havoc on your system or network. For example, a macro that automates file management tasks by deleting old files could inadvertently wipe out a whole folder full of files if you don't define its parameters carefully.
You can have a high degree of confidence in macros you write yourself, but you should never trust a macro you receive from someone you've never met. Thousands of macro viruses exist, and you run the risk of encountering one of them every time you open a document, workbook, presentation, or Access database.
What is a macro virus, and how likely are you to encounter one? Here are some simple facts every Office user should know:
A computer "virus" is just a program that propagates. A macro virus uses a macro language (such as VBA or VBScript) as the means of propagating. A large percentage of macro viruses aren't harmful in any way.
Some viruses corrupt data in subtle ways by rearranging words and phrases in documents, or adding the word "not" in random locations. These are the most insidious viruses because, without full and detailed backups, it's nearly impossible to restore documents to their original state.
Other serious macro viruses erase selected files or groups of files from your hard drive. You can often recover from these destructive viruses by using the Windows Recycle bin, well-maintained backups, or third-party software such as Norton's Unerase.
Some nasty macro viruses prevent you from using Office, or Windows itself, by deleting key files or rearranging the Windows Registry. Sometimes the cure is as simple as reinstalling the software, but a well-written virus can make even this cure impossible.
The most sophisticated virus-writing techniques often appear in Office macro viruses before they show up anywhere else. Some use "stealth" technology (for example, the virus might take over the Office components that let you see macros, thereby hiding themselves), or "polymorphism" (where the virus mutates each time it replicates, making it much harder to identify and catch).
Viruses can propagate from application to application. For example, you might introduce a virus to your system by opening an infected Word document, and then the infection can spread to Excel workbooks. Because Outlook and other clients support scripting languages, it is theoretically possible to spread viruses through e-mail messages, even without file attachments.
You're far more likely to receive an infected file from a coworker, a friend, or a network server than by downloading documents from the Internet. Similarly, you are far more likely to lose data due to a dumb mistake or a hardware problem than to a macro virus.
Almost all virus scares are precisely that—scares—with little or no foundation in reality.
The vast majority of macro viruses rank as amateurish and poorly written, and can hardly survive in the wild. Some, however, have proven themselves robust—and destructive.
Tip from 
For the latest unbiased information on macro viruses, threats, and solutions, subscribe to the free weekly e-mail newsletter called Woody's Office Watch by sending a message to [email protected].
Using Digital Signatures to Verify a Macro's Source
Office XP includes a number of innovative methods to help protect you from macro viruses. Digital signatures lie at the heart of the approach most frequently encountered by Office users.
A digital signature identifies the source of a macro. Developers must apply for digital signatures from certifying authorities, which verify the identity of developers before issuing them a signature. Certifying authorities can revoke a certificate after issuing it, if they discover evidence that a developer is distributing viruses or unsafe software.
A digital signature identifies the company (or person) that claims to have written a macro. It does not tell you anything about the author. A macro signed "A-Z Developers Inc." could have originated with a terrorist in Timbuktu. Similarly, certificates can be generated with any name, so if you find a macro signed "Bill Gates" on the Web site http://www.virusheaven.com, you should doubt its veracity. It's up to you to decide whether you trust the company (or person) that signed the macro.
When you open a digitally signed macro in Word, Excel, PowerPoint, Outlook, or FrontPage, you'll see a dialog box that contains information about the signature and asks whether you want to run the program (see Figure 38.6).
Figure 38.6. A digital signature verifies only the source of the macro—not its safety.
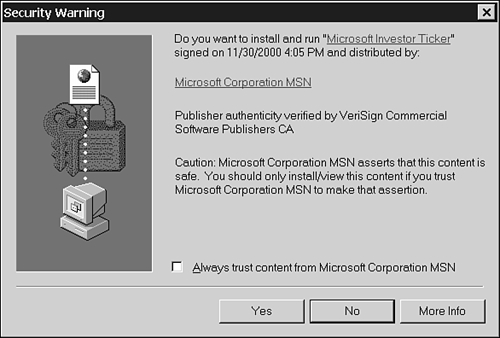
If you click the box marked Always Trust Content from Source, Office will add that digital signature to its "trusted sites" list. From that point on, you will be able to open signed macros from that source without having to click through a dialog box.
Configuring Office Security Levels
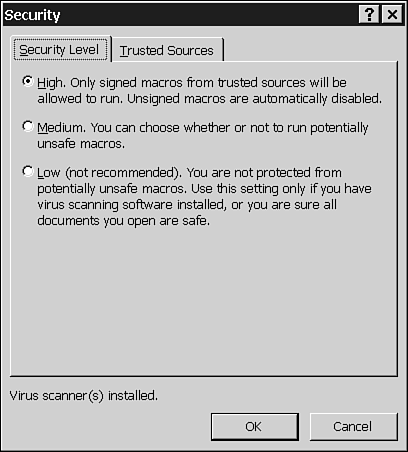
Digital signatures work in conjunction with each application's security level to determine which macros will or will not run. Word, Excel, PowerPoint, Outlook, and Publisher (but, surprisingly, not FrontPage) enable you to set three different security levels (see Table 38.2). For example, you might want to run any macro on your company's intranet, because you know your company's information technology specialists have tested it carefully before putting it there. On the other hand, you probably never want to run a macro you receive from a completely unknown source on the Internet. To open the Security dialog box (see Figure 38.7), choose Tools, Macro, Security.
Figure 38.7. If you understand the implications of digital code signing and the possible threat from macro viruses, the Medium setting will generally suffice.
| Security Level | Macro Restrictions |
|---|---|
| High | Only valid digitally signed macros from a previously identified "trusted source" will run automatically. If the macro is signed, but the source isn't listed as a "trusted source," you will be given the opportunity to accept or reject the certificate (refer to Figure 38.7) and add the source to the trusted list. In all other cases, macros are disabled. |
| Medium | Much like the High setting, except that users have the option to enable or disable macros if there's a problem with the signature (for example, it was incorrectly applied), or if there's no signature at all. |
| Low | All macros are enabled, without regard to the presence of a digital signature. |
The default security setting in Word, Excel, PowerPoint, Outlook, and Publisher is High.
Tip from 
Consider setting Word and Excel security to Medium. If you leave it on High, Word and Excel discards unsigned macros, and you'll never know they existed.
When you receive HTML messages, Outlook 2002 uses the same zone-based security model as Internet Explorer. In fact, the security options you specify in Outlook apply to Internet Explorer and Outlook Express, and vice versa. From Outlook, choose Tools, Options, click the Security tab, and click the Zone Settings button; you'll see the dialog box shown in Figure 38.8.
Figure 38.8. Outlook 2002 uses the same security settings as those you'll find in Internet Explorer.
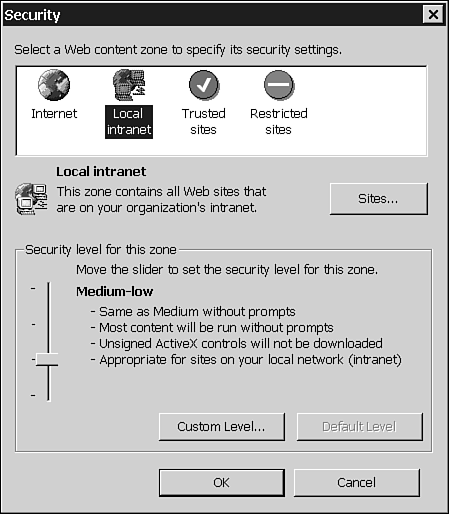
Internet Explorer and Outlook define four zones:
The Local Intranet zone, which covers Web sites maintained on your company's internal intranet. Default security setting is Medium-Low.
The Trusted Sites zone, which includes only those URLs you have specifically designated as "trusted." Use this setting if you're certain that a site's security substantially exceeds Web norms; by default, Internet Explorer allows you to add only sites that require server verification (https) to this zone. To add a URL to this list, click Add Sites. Default security setting is Low.
The Internet zone, an "all other" category that includes any site not designated Local, Trusted, or Restricted. Default security setting is Medium.
The Restricted Sites zone, where you should definitely place any "hacker" or "cracker" sites you visit. To add a URL to this list, select Restricted Sites zone from the list, and then click Add/Remove Sites. Default security setting is High.
You can customize individual security settings—dozens of them—by choosing the zone you want to restrict, and then clicking Custom Level (see Figure 38.9).
Figure 38.9. Internet Explorer offers dozens of custom security choices.
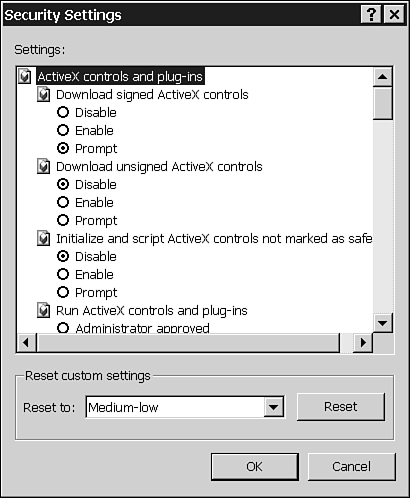
Many of these custom settings are complex, with consequences not at all apparent based strictly on the descriptions in the dialog box.
Note
To learn more about customizing the Windows security settings, see Special Edition Using Microsoft Windows XP, Home Edition, or Special Edition Using Windows 98.
Blocking Access to the Visual Basic Project
Most macro viruses propagate by creating copies of themselves: They build macros attached to documents, which, in turn, infect other Office users. To create a copy, the virus has to be able to get at the part of VBA that's used to write new programs. The virus then proceeds in a manner that's similar to what you would use to write or record a macro, except the virus does it all by using programs.
The part of VBA that's used to build new macros (and modify old ones) is called the Visual Basic Project.
Office automatically prevents programs from getting into the Visual Basic Project unless you specifically, deliberately allow macros to get in. You can only allow macros access to the Visual Basic Project if you choose Tools, Macro, Security, click the Trusted Sources tab, and check the box marked Trust Access to Visual Basic Project (see Figure 38.10).
Figure 38.10. Unless you have a specific reason to allow macros to create and modify other macros, leave the box marked Trust Access to Visual Basic Project unchecked.
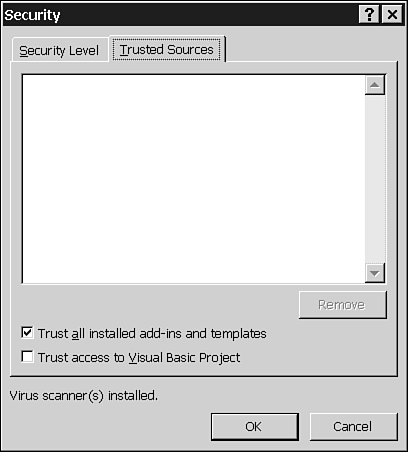
It's rare that anyone—even professional macro programmers—will grant programmatic access to the Visual Basic Project. Although leaving this box unchecked won't protect you from all macro viruses, it effectively neutralizes a large percentage of all the viruses created before December, 2000.
Protecting Your PC and Network from Viruses
Office 2002 incorporates virus-detection technology that allows antivirus programs to "hook into" Office; an up-to-date antivirus program that includes this hook can examine a file for viruses before allowing an Office program to open the file. (That's why you'll frequently see the message "Requesting a virus scan" at the bottom of an application's window whenever you open a file.) This antivirus scan operates independently of digital signatures, and it has been proven effective in reducing the impact of Office macro viruses.
It's impossible to stop every macro virus, but you can dramatically reduce the risks to your system and network by following these procedures:
For Word, Excel, PowerPoint, Outlook, and Publisher, keep the digital security setting on Medium for users who understand the implications of macro viruses, and High for all others.
Purchase, install, and regularly update one of the major antivirus software packages. Make sure the program you select is compatible with Office 2002.
Stay informed of the latest virus (and antivirus) developments. All the major antivirus software vendors maintain Web sites with up-to-the-minute news: The Symantec Anti-Virus Research Center (Norton AntiVirus) is at http://www.symantec.com/avcenter; Network Associates'(McAfee VirusScan) site is at http://www.nai.com/vinfo.
Tip from 
How many times this week have you received a breathless e-mail warning you about a deadly new virus? Is the latest warning real, or the figment of someone's grossly overactive imagination? For the definitive answer, head directly to Rob Rosenberger's Virus Myths Home Page at http://www.vmyths.com. Rob's voice of reason stands in stark contrast to much of the mindless virus-clamoring you'll hear on the Net. And, he knows his stuff.
