15.1 Networking
A computer network is a collection of computing devices that are connected in various ways to communicate and share resources. Email, instant messaging, and web pages all rely on communication that occurs across an underlying computer network. We use networks to share both intangible resources, such as files, and tangible resources, such as printers.
Usually, the connections between computers in a network are made using physical wires or cables. However, some connections are wireless, using radio waves or infrared signals to convey data. Networks are not defined only by physical connections; they are defined by the ability to communicate.
Computer networks contain devices other than computers. Printers, for instance, can be connected directly to a network so that anyone on the network can print to them. Networks also contain a variety of devices for handling network traffic. We use the generic terms node or host to refer to any device on a network.
A key issue related to computer networks is the data transfer rate, the speed with which data is moved from one place on a network to another. We are constantly increasing our demand on networks as we rely on them to transfer more data in general, as well as data that is inherently more complex (and therefore larger). Multimedia components such as audio and video are large contributors to this increased traffic. Sometimes the data transfer rate is referred to as the bandwidth of a network. (Recall that we discussed bandwidth in Chapter 3 in the discussion of data compression.)
Another key issue in computer networks is the protocols they use. As we’ve mentioned at other points in this book, a protocol is a set of rules describing how two things interact. In networking, we use well-defined protocols to describe how transferred data is formatted and processed.
Computer networks have opened up an entire frontier in the world of computing called the client/server model. No longer do you have to think of computers solely in terms of the capabilities of the machine sitting in front of you. Instead, software systems are often distributed across a network, in which a client sends a request to a server for information or action, and the server responds, as shown in FIGURE 15.1.

FIGURE 15.1 Client/server interaction
For example, a file server is a computer that stores and manages files for multiple users on a network. That way every user doesn’t need to have his or her own copy of the files. A web server is a computer dedicated to responding to requests (from the browser client) for web pages. Client/server relationships have become more complex as we rely heavily on networks in our everyday lives. Therefore, the client/server model has become increasingly important in the world of computing.
The client/server model has also grown beyond the basic request/ response approach. Increasingly, it is being used to support parallel processing, in which multiple computers are used to solve a problem by breaking it into pieces, as discussed in Chapter 5. Using networks and the client/server model, parallel processing can be accomplished by the client requesting that multiple machines perform specific, separate parts of the same problem. The client then gathers their responses to form a complete solution to the problem.
Another approach for computer interaction across networks is the P2P model, or peer-to-peer model. Instead of having a central server from which clients obtain information, a peer-to-peer network is decentralized, with nodes that share both resources and the responsibility for making these resources available to other peers. Depending on the request, a peer may act as a client or a server.
In a P2P network, a request for a file may go to several other peers in the network. If a peer does not have the file, it forwards the request to other peers, and so on, until the file is found. Then (usually) a connection is made directly between the requesting peer and the peer that has the resource to transfer the file.
The P2P model eliminates the need for a single server to hold all resources because it distributes the communication among many computers. However, these advantages also bring drawbacks: A P2P network is more difficult to administer and prone to security problems.
Types of Networks
Computer networks can be classified in various ways. A local-area network (LAN) connects a relatively small number of machines in a relatively close geographical area. LANs are usually confined to a single room or building. They may sometimes span a few close buildings.
Historically, various configurations, called topologies, have been used to administer LANs. A ring topology connects all nodes in a closed loop on which messages travel in one direction. The nodes of a ring network pass along messages until they reach their destination. A star topology centers on one node to which all others are connected and through which all messages are sent. A star network puts a huge burden on the central node; if it is not working, communication on the network is not possible. In a bus topology, all nodes are connected to a single communication line that carries messages in both directions. The nodes on the bus check any message sent on the bus but ignore any that are not addressed to them. These topologies are pictured in FIGURE 15.2.

FIGURE 15.2 Network topologies
A wide-area network (WAN) connects two or more local-area networks over a potentially large geographic distance. A WAN permits communication among smaller networks. Often one particular node on a LAN is set up to serve as a gateway to handle all communication going between that LAN and other networks. See FIGURE 15.3.
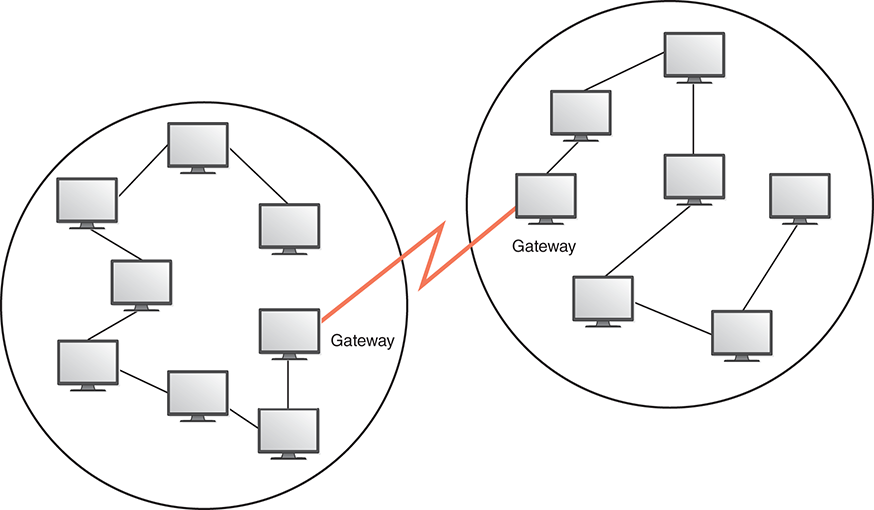
FIGURE 15.3 Local-area networks connected across a distance to create a wide-area network
Communication between networks is called internetworking. The Internet, as we know it today, is essentially the ultimate wide-area network, spanning the entire globe. The Internet is a vast collection of smaller networks that have all agreed to communicate using the same protocols and to pass along messages so that they can reach their final destination.
The term metropolitan-area network (MAN) is sometimes used to refer to a large network that covers a campus or a city. Compared to a general wide-area network, a MAN is more narrowly focused on a particular organization or geographic area. A MAN that services a college or business campus typically interconnects the local-area networks used by various buildings and departments. Some cities have formed a MAN in their geographical area to service the general populace. Metropolitan-area networks are often implemented using wireless or optical fiber connections.
Wireless and Mobile Computing
Today we are often computing on the go, using wireless devices such as smartphones, tablets, and laptops. A wireless network is one in which at least one node serves as a wireless access point, allowing appropriate devices to interact with other network resources without being physically connected. That access point is usually wired to other network nodes in conventional ways.
You may, for instance, have a wireless access point set up in your home or business that allows your tablet to connect to the Internet. Using radio waves, your tablet exchanges information with the wireless access point, which in turn communicates with other network resources, including the node that is connected to the Internet.
Wireless networks give the user tremendous freedom and flexibility. They greatly reduce installation costs by eliminating the need to run wires. However, they are more prone to electromagnetic interference than wired networks, and they must cope with access control challenges that a wired connection does not.
On a smaller scale, Bluetooth technology allows wireless communication between devices over a short distance. A Bluetooth device uses radio waves in a particular bandwidth and is significantly limited in range compared to other wireless technology. However, it solves many short-range problems, such as communication between your cell phone and a hands-free headset, between your media device and a car stereo system, and between a computer and a wireless keyboard, mouse, or trackpad.
Internet Connections
Who owns the Internet? Well, no one. No single person or company owns the Internet or even controls it entirely. As a wide-area network, the Internet is made up of many smaller networks. These smaller networks are often owned and managed by a person or organization. The Internet, then, is defined by how connections can be made among these networks.
The speed of these interconnected networks determines how fast you get your results. The latency of a network system is the time that elapses between the transmission of a request and its receipt. The general goal, then, is to minimize latency on a network, which ultimately defines its speed.
The Internet backbone refers to a set of high-capacity data routes that carry Internet traffic. These routes are provided by various companies such as AT&T, Verizon, and British Telecom, as well as by several government and academic sources. The backbone networks all operate using connections that have high data transfer rates, ranging from 40 gigabits (Gb) per second to more than 100 Gb per second. Newer technologies will likely increase these speeds further in the near future. Keep in mind, though, that Internet routes, including the backbone networks, employ a large amount of redundancy, so there is really no central network.
Organizations that provide companies or individuals with access to the Internet are called Internet service providers (ISPs). TV cable and satellite companies often provide ISP services as well, which makes sense given the communication infrastructure they already have in place. An ISP is not always a commercial organization, though—some are set up as community or nonprofit organizations. An ISP connects directly to the Internet backbone or to a larger ISP that has a connection to the backbone.
One of the earliest technologies for connecting a home computer to the Internet was the phone modem. Today, the two most popular techniques are digital subscriber lines and cable modems. Let’s examine each in turn.
The telephone system had already connected homes throughout the world long before the desire for Internet connections came along. Therefore, it makes sense that the first technique for home-based network communication was a phone modem. The word modem stands for modulator/demodulator. A phone modem converts computer data into an analog audio signal for transfer over a telephone line, and then a modem at the destination converts it back into data again. One audio frequency is used to represent binary 0 and another to represent binary 1.
To use a phone modem, you had to first establish a telephone connection between your home computer and a computer that was permanently connected to the Internet. That’s where your Internet service provider came in. You paid your ISP a monthly fee for the right to call one of several (preferably local) computers that it had set up for this purpose. Once that connection was made, you could transfer data via your phone lines to your ISP, which then sent it on its way through the Internet backbone. Incoming traffic was routed through your ISP to your home computer.
This approach was fairly simple to implement because it did not require any special effort on the part of the telephone company. Because the data was treated as if it were a voice conversation, no special translation was needed except at either end. But that convenience came at a price. The data transfer rate available with this approach was limited to that of analog voice communication, usually 64 kilobits per second at most.
A phone line can provide a much higher transfer rate if the data is treated as digital rather than analog. A digital subscriber line (DSL) uses regular copper phone lines to transfer digital data to and from the phone company’s central office. Because DSL and voice communication use different frequencies, it is even possible to use the same phone line for both purposes.
To set up a DSL connection, your phone company may become your Internet service provider, or it may sell the use of its lines to a third-party ISP. To offer DSL service, the phone company must set up special computers to handle the data traffic.
With DSL, there is no need to “dial in” to create the network connection, as with a phone modem. The DSL line maintains an active connection between your home and a computer at the ISP. However, to take advantage of DSL technology, your home must be within a certain distance from the central office; otherwise, the digital signal degrades too much while traveling between those two points.
The most popular option for home connections is a cable modem. In this approach, data is transferred on the same line that your cable TV signals come in on. Several leading cable TV companies in North America have pooled their resources to create Internet service providers for cable modem service.
Both DSL connections and cable modems fall into the category of broadband connections. Depending on the location and whether access is by satellite, phone wire, video cable, or fiber optics, it is generally defined as being at least 25 megabits per second (Mbps) for downloads. Households have moved away from the use of phone modems to a broadband solution for their computing network needs. Debate between the DSL and cable modem communities continues to rage to see who can claim the dominant market share. Both generally provide data transfer speeds in the range of 1.5 to 3 megabits per second.
For both DSL and cable modems, the speed for downloads (getting data from the Internet to a local computer) is not the same as the speed for uploads (sending data from a local computer to the Internet). Most traffic for home Internet users consists of downloads: receiving web pages to view and retrieving data (such as programs and audio and video) stored somewhere else on the network. You perform an upload when you send an email message, submit a web-based form, or request a new web page. Because download traffic dominates upload traffic, many DSL and cable modem suppliers use technology that devotes more speed to downloads.
Packet Switching
To improve the efficiency of transferring data over a shared communication line, messages are divided into fixed-size, numbered packets. These packets are sent over the network individually to their destination, where they are collected and reassembled into the original message. This approach is referred to as packet switching.
The packets of a message may take different routes on their way to the final destination. Therefore, they may arrive in a different order than the way they were sent. The packets must be put into the proper order once again and then combined to form the original message. FIGURE 15.4 illustrates this process.
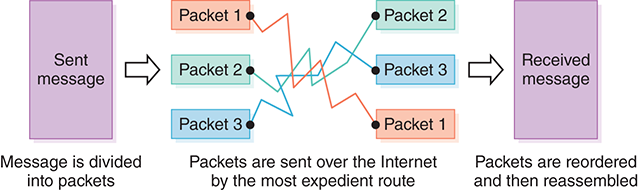
FIGURE 15.4 Messages sent by packet switching
A packet may make several intermediate hops between computers on various networks before it reaches its final destination. Network devices called routers direct the packets as they move between networks. Intermediate routers don’t plan out the packet’s entire course; each router merely knows the best next step to get it closer to its destination. Eventually a message reaches a router that knows where the destination machine is. If a path is blocked due to a down machine, or if a path currently has a lot of network traffic, a router might send a packet along an alternative route.
If a communication line spans a long distance, such as across an ocean, devices called repeaters are installed periodically along the line to strengthen and propagate the signal. Recall from Chapter 3 that a digital signal loses information only if it is allowed to degrade too much. A repeater keeps that from happening.
