
© Artur Debat/Getty Images; © Alan Dyer/Stocktrek Images/Getty Images
PREFACE
Choice of Topics
In putting together the outline of topics for this CS0 text, we used many sources. We looked at course catalogue descriptions and book outlines, and we administered a questionnaire designed to find out what you, our colleagues, thought should be included in such a course. We asked you and ourselves to do the following:
Please list four topics that you feel students should master in a CS0 course if this is the only computer science course they will take during their college experience.
Please list four topics that you would like students entering your CS1 course to have mastered.
Please list four additional topics that you would like your CS1 students to be familiar with.
The strong consensus that emerged from the intersections of these sources formed the working outline for this book. It serves as a core CS0 text, providing a breadth-first introduction to computing. It is appropriate for use for a course embracing the AP Computer Science Principles curriculum, and alternatively as a companion or lead-in to a programming intensive course.
Rationale for Organization
This book begins with the history of hardware and software, showing how a computer system is like an onion. The processor and its machine language form the heart of the onion, and layers of software and more sophisticated hardware have been added around this heart, layer by layer. At the next layer, higher-level languages such as FORTRAN, Lisp, Pascal, C, C++, and Java were introduced parallel to the ever-increasing exploration of the programming process, using such tools as top-down design and object-oriented design. Over time, our understanding of the role of abstract data types and their implementations matured. The operating system, with its resource-management techniques—including files on ever-larger, faster secondary storage media—developed to surround and manage these programs.
The next layer of the computer system “onion” is composed of sophisticated general-purpose and special-purpose software systems that overlay the operating system. Development of these powerful programs was stimulated by theoretical work in computer science, which makes such programs possible. The final layer comprises networks and network software—that is, the tools needed for computers to communicate with one another. The Internet and the World Wide Web put the finishing touches to this layer, and this text culminates with a discussion of security issues affecting our interaction online.
As these layers have grown over the years, the user has become increasingly insulated from the computer system’s hardware. Each of these layers provides an abstraction of the computing system beneath it. As each layer has evolved, users of the new layer have joined with users of inner layers to create a very large workforce in the high-tech sector of the global economy. This book is designed to provide an overview of the layers, introducing the underlying hardware and software technologies, in order to give students an appreciation and understanding of all aspects of computing systems.
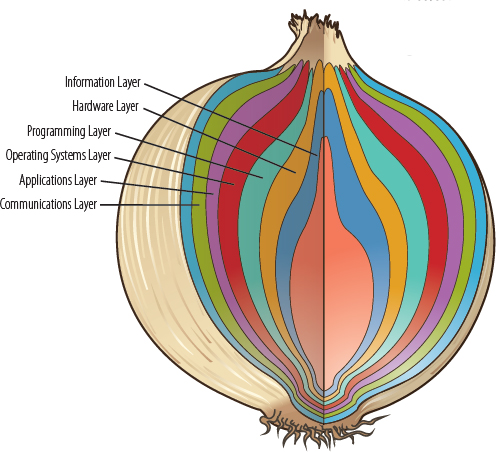
Having used history to describe the formation of the onion from the inside out, we were faced with a design choice: We could look at each layer in depth from the inside out or the outside in. The outside-in approach was very tempting. We could peel the layers off one at a time, moving from the most abstract layer to the concrete machine. However, research has shown that students understand concrete examples more easily than abstract ones, even when the students themselves are abstract thinkers. Thus, we have chosen to begin with the concrete machine and examine the layers in the order in which they were created, trusting that a thorough understanding of one layer makes the transition to the next abstraction easier for the students.
Changes in the Seventh Edition
As always when planning a revision, we asked our colleagues, including many current users of the text, to give us feedback. We appreciate the many thoughtful and insightful responses we received.
A variety of changes have been made throughout the book with the Seventh Edition. One includes a conscious effort to improve our coverage of the specific topics described in the AP Computer Science Principles curriculum. This book was already a good match for that approach, but the curriculum provided a wealth of ideas for updated content, both large and small. An overview of the Big Ideas in computing that form the high-level framework of the Principles curriculum is now included in Chapter 1.
Among the other larger changes with this edition are a stronger introduction to cloud computing, an updated example computer specification described in Chapter 5, a discussion of spreadsheet visualization and an introduction to big data in Chapter 12, a discussion of smart speakers such as Amazon Echo and Google Home in Chapter 13, a discussion of blockchain in Chapter 15, and updated security discussions in Chapter 17.
Another big change in the Seventh Edition is a complete overhaul of Chapter 6 to update the text and examples to use the Pep/9 machine. Several improvements were made to the underlying system in the upgrade from Pep/8 that help the explanations of programming at the machine language and assembly levels.
In addition, the special features throughout the book have been completely revised and augmented. The “Ethical Issues” sections at the end of each chapter have been brought up to date, addressing the ever-changing state of those issues. Several additional “Did You Know?” sidebars have been added, and many others updated. Finally, the biographical sketches throughout the book have been updated.
As with each edition, the entire text has been reviewed for opportunities to improve the coverage, presentation, and examples used. Updated (and sometimes streamlined) text throughout the book helps to clarify the topics presented.
Synopsis
Chapter 1 lays the groundwork, as described in the “Rationale for This Book’s Organization” section above. Chapters 2 and 3 step back and examine a layer that is embodied in the physical hardware. We call this the “information layer” because it reflects how data is represented in the computer. Chapter 2 covers the binary number system and its relationship to other number systems such as decimal (the one we humans use on a daily basis). Chapter 3 investigates how we take the myriad types of data we manage—numbers, text, images, audio, and video—and represent them in a computer in binary format.
Chapters 4 and 5 discuss the hardware layer. Computer hardware includes devices such as transistors, gates, and circuits, all of which control the flow of electricity in fundamental ways. This core electronic circuitry gives rise to specialized hardware components such as the computer’s central processing unit (CPU) and memory. Chapter 4 covers gates and electronic circuits; Chapter 5 focuses on the hardware components of a computer and how they interact within a von Neumann architecture.
Chapters 6 through 9 examine aspects of the programming layer. Chapter 6 explores the concepts of both machine-language and assembly- language programming using Pep/9, a simulated computer. We discuss the functionality of pseudocode as a way to write algorithms. The concepts of looping and selection are introduced here, expressed in pseudocode, and implemented in Pep/9.
Chapter 7 examines the problem-solving process as it relates to both humans and computers. George Polya’s human problem-solving strategies guide the discussion. Top-down design is presented as a way to design simple algorithms. We choose classic searching and sorting algorithms as the context for the discussion of algorithms. Because algorithms operate on data, we examine ways to structure data so that it can be more efficiently processed. We also introduce subalgorithm (subprogram) statements.
Chapter 8 explores abstract data types and containers: composite structures for which we know only properties or behaviors. Lists, sorted lists, stacks, queues, binary search trees, and graphs are discussed. The section on subalgorithms is expanded to include reference and value parameters and parameter passing.
Chapter 9 covers the concepts of high-level programming languages. Because many prominent high-level languages include functionality associated with object-oriented programming, we detour and first present this design process. Language paradigms and the compilation process are discussed. Pseudocode concepts are illustrated in brief examples from four programming languages: Python, Visual Basic .NET, C++, and Java.
Chapters 10 and 11 cover the operating system layer. Chapter 10 discusses the resource management responsibilities of the operating system and presents some of the basic algorithms used to implement these tasks. Chapter 11 focuses on file systems, including what they are and how they are managed by the operating system.
Chapters 12 through 14 cover the application layer. This layer is made up of the general-purpose and specialized application programs that are available to the public for solving programs. We divide this layer into the sub-disciplines of computer science upon which these programs are based. Chapter 12 examines information systems, Chapter 13 examines artificial intelligence, and Chapter 14 examines simulation, graphics, gaming, and other applications.
Chapters 15 through 17 cover the communication layer. Chapter 15 presents the theoretical and practical aspects of computers communicating with each other. Chapter 16 discusses the World Wide Web and the various technologies involved. Chapter 17 examines computer security and keeping information protected in the modern information age.
Chapters 2 through 17 are about what a computer can do and how. Chapter 18 concludes the text with a discussion of the inherent limitations of computer hardware and software, including the problems that can and cannot be solved using a computer. We present Big-O notation as a way to talk about the efficiency of algorithms so that the categories of algorithms can be discussed, and we use the halting problem to show that some problems are unsolvable.
The first and last chapters form bookends: Chapter 1 describes what a computing system is and Chapter 18 cautions about what a computing system is not. The chapters between take an in-depth look at the layers that make up a computing system.
Why Not a Language?
Instead of championing a specific programming language such as Java, C++, or something else, we decided to leave the choice to the user. Introductory chapters, formatted in a manner consistent with the design of this book, are available for Java, C++, JavaScript, Visual Basic. NET, Python, SQL, Ruby, Perl, Alice, and Pascal on the book’s website.
If the students have enough knowledge and experience to master the introductory syntax and semantics of a language in addition to the background material in this book, simply have the students download the appropriate chapter. As an alternative, one or all of these chapters can be used to enrich the studies of those who have stronger backgrounds.
Special Features
We have included three special features in this text in order to emphasize the history and breadth of computing as well as the moral obligations that come with new technology.

10.4 CPU Scheduling
Biographies
Each chapter includes a short biography of someone who has made a significant contribution to computing as we know it. The people honored in these sections range from those who contributed to the data layer, such as George Boole and Ada Lovelace, to those who have contributed to the communication layer, such as Doug Engelbart and Tim Berners-Lee. These biographies give students a taste of history and introduce them to the men and women who are pioneers in the world of computing.
Did You Know
Our second feature (the “Did You Know?” sections indicated by a question mark) comprises sidebars that include interesting tidbits of information from the past, present, and future. They are garnered from history, current events, and the authors’ personal experiences. These little vignettes are designed to amuse, inspire, intrigue, and, of course, educate.

Ethical Issues
Our third feature is an “Ethical Issues” section that is included in each chapter. These sections illustrate the fact that along with the advantages of computing come responsibilities for and consequences of its use. Privacy, hacking, viruses, and free speech are among the topics discussed. Following the exercises in each chapter, a “Thought Questions” section asks stimulating questions about these ethical issues as well as chapter content.

Color and Typography Are Signposts
The layers into which the book is divided are color coded within the text. The opening spread for each chapter shows an image of the onion in which the outermost color corresponds to the current layer. This color is repeated in header bars and section numbers throughout the layer. Each opening spread also visually indicates where the chapter is within the layer and the book.
We have said that the first and last chapters form bookends. Although they are not part of the layers of the computing onion, these chapters are color coded like the others. Open the book anywhere and you can immediately tell where you are within the layers of computing.
To visually separate the abstract from the concrete in the programming layer, we use different fonts for algorithms, including identifiers in running text, and program code. You know at a glance whether the discussion is at the logical (algorithmic) level or at the programming-language level. In order to distinguish visually between an address and the contents of an address, we color addresses in orange.
Color is especially useful in Chapter 6, “Low-Level Programming Languages and Pseudocode.” Instructions are color coded to differentiate the parts of an instruction. The operation code is blue, the register designation is clear, and the addressing mode specifier is green. Operands are shaded gray. As in other chapters, addresses are in orange.
Instructor Resources
For the instructor, slides in PowerPoint format, a test bank, and answers to the book’s end-of-chapter exercises are available for free download at http://go.jblearning.com/CSI7e.
