 Discovering brute-force and application attacks
by Charit Mishra, Yoram Orzach, James H Baxter
Wireshark Revealed: Essential Skills for IT Professionals
Discovering brute-force and application attacks
by Charit Mishra, Yoram Orzach, James H Baxter
Wireshark Revealed: Essential Skills for IT Professionals
- Wireshark Revealed: Essential Skills for IT Professionals
- Table of Contents
- Wireshark Revealed: Essential Skills for IT Professionals
- Credits
- Preface
- 1. Module 1
- 1. Getting Acquainted with Wireshark
- 2. Networking for Packet Analysts
- The OSI model – why it matters
- IP networks and subnets
- Switching and routing packets
- WAN links
- Wireless networking
- Summary
- 3. Capturing All the Right Packets
- Picking the best capture point
- Test Access Ports and switch port mirroring
- Capturing interfaces, filters, and options
- Verifying a good capture
- Saving the bulk capture file
- Isolating conversations of interest
- Using the Conversations window
- Wireshark display filters
- Filter Expression Buttons
- Following TCP/UDP/SSL streams
- Marking and ignoring packets
- Saving the filtered traffic
- Summary
- 4. Configuring Wireshark
- 5. Network Protocols
- The OSI and DARPA reference models
- Transport layer protocols
- Application layer protocols
- Summary
- 6. Troubleshooting and Performance Analysis
- Troubleshooting methodology
- Troubleshooting connectivity issues
- Troubleshooting functional issues
- Performance analysis methodology
- Top five reasons for poor application performance
- Summary
- 7. Packet Analysis for Security Tasks
- 8. Command-line and Other Utilities
- 2. Module 2
- 1. Introducing Wireshark
- 2. Using Capture Filters
- 3. Using Display Filters
- 4. Using Basic Statistics Tools
- Introduction
- Using the Summary tool from the Statistics menu
- Using the Protocol Hierarchy tool from the Statistics menu
- Using the Conversations tool from the Statistics menu
- Using the Endpoints tool from the Statistics menu
- Using the HTTP tool from the Statistics menu
- Configuring Flow Graph for viewing TCP flows
- Creating IP-based statistics
- 5. Using Advanced Statistics Tools
- Introduction
- Configuring IO Graphs with filters for measuring network performance issues
- Throughput measurements with IO Graph
- Advanced IO Graph configurations with advanced Y-Axis parameters
- Getting information through TCP stream graphs – the Time-Sequence (Stevens) window
- Getting information through TCP stream graphs – the Time-Sequence (tcp-trace) window
- Getting information through TCP stream graphs – the Throughput Graph window
- Getting information through TCP stream graphs – the Round Trip Time window
- Getting information through TCP stream graphs – the Window Scaling Graph window
- 6. Using the Expert Infos Window
- 7. Ethernet, LAN Switching, and Wireless LAN
- 8. ARP and IP Analysis
- 9. UDP/TCP Analysis
- Introduction
- Configuring TCP and UDP preferences for troubleshooting
- TCP connection problems
- TCP retransmission – where do they come from and why
- Duplicate ACKs and fast retransmissions
- TCP out-of-order packet events
- TCP Zero Window, Window Full, Window Change, and other Window indicators
- TCP resets and why they happen
- 10. HTTP and DNS
- 11. Analyzing Enterprise Applications' Behavior
- Introduction
- Finding out what is running over your network
- Analyzing FTP problems
- Analyzing e-mail traffic and troubleshooting e-mail problems – POP, IMAP, and SMTP
- Analyzing MS-TS and Citrix communications problems
- Analyzing problems in the NetBIOS protocols
- Analyzing database traffic and common problems
- 12. SIP, Multimedia, and IP Telephony
- Introduction
- Using Wireshark's features for telephony and multimedia analysis
- Analyzing SIP connectivity
- Analyzing RTP/RTCP connectivity
- Troubleshooting scenarios for video and surveillance applications
- Troubleshooting scenarios for IPTV applications
- Troubleshooting scenarios for video conferencing applications
- Troubleshooting RTSP
- 13. Troubleshooting Bandwidth and Delay Problems
- 14. Understanding Network Security
- A. Links, Tools, and Reading
- 3. Module 3
- 1. Welcome to the World of Packet Analysis with Wireshark
- 2. Filtering Our Way in Wireshark
- 3. Mastering the Advanced Features of Wireshark
- 4. Inspecting Application Layer Protocols
- 5. Analyzing Transport Layer Protocols
- 6. Analyzing Traffic in Thin Air
- 7. Network Security Analysis
- 8. Troubleshooting
- 9. Introduction to Wireshark v2
- Bibliography
- Index
The next step in network attack is to understand the various types of brute-force attacks. A brute-force attack is a trial-and-error method used to obtain information from the victim, for example, trying to find organizational servers, user directories, and crack passwords.
Brute-force attacks usually will not produce non-standard loads on the network, and the way they are discovered is usually by IDS systems or when there is a suspicion that someone is trying to hack into the network. In this recipe, we will learn how to identify typical brute-force attacks.
When you suspect a brute-force on the network, follow these steps to locate it.
- Connect Wireshark with port mirror to the port in the server that you suspect is under attack.
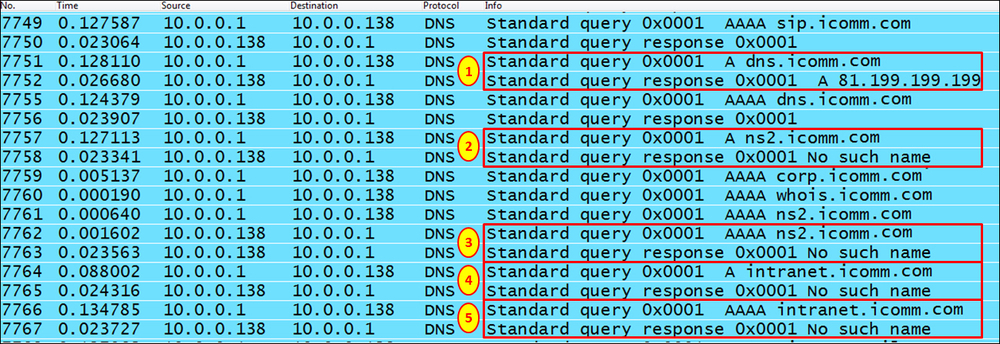
- For DNS brute-force attacks, look for DNS queries that are asking for common names under your domain. For example, in the following illustration, you can see a scan for ISP servers. We can see DNS queries to common names such as dns (1) and dns2—a record for IPv4 (2) and a record for IPv6 (3), and intranet—a record for IPv4 (4) and a record for IPv6 (5).
- In the case of dns.icomm.co (1), we got a reply; in all other cases, we did not.
- Many queries with no response can indicate a DNS brute attack, but also indicate someone who is looking for a server that does not exist. Look at the source address to see where it is coming from.
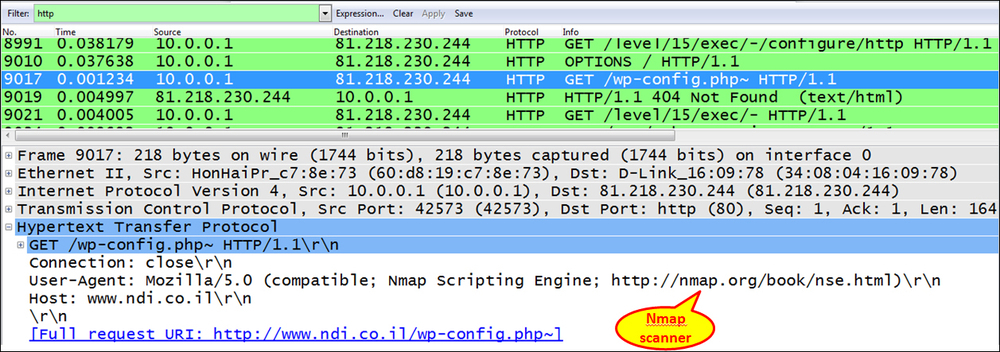
- Another brute-force attack to watch out for is HTTP trying to find resources on the server.
- To look for HTTP scanning, look for the scanner's signature in the packet details, as seen in the following screenshot.
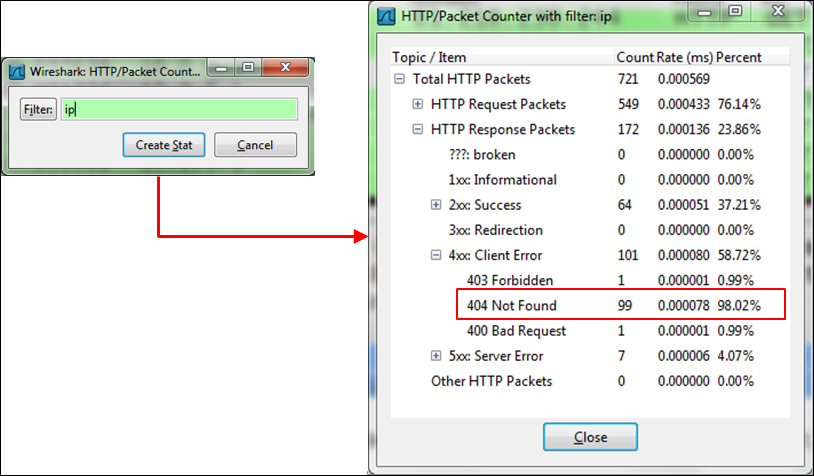
- Also, look for too many HTTP error messages. Some examples are illustrated in the following screenshot. Choose Statistics | HTTP | Packet Counter | PC. If you get too many error messages, check for their source.
- To look for HTTP scanning, look for the scanner's signature in the packet details, as seen in the following screenshot.
Brute-force attacks are trial and error attacks that send requests to the destination, hoping that some of them will be answered. Since most of these requests will be denied (if you've configured your servers properly), a large amount of Not Found messages, forbidden messages, and other error codes can be some of the syndromes for such an attack.
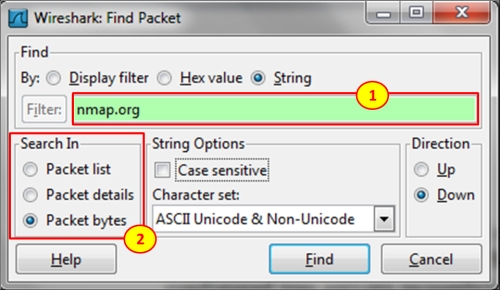
For discovering HTTP error codes, configure the display filter http.response.code >= 400. The same applies to SIP and any protocol that uses HTTP-like codes. To find known scanners, you can simply use the Edit | Find packet feature and look for common scanner names. In the following screenshot, you can see an example for Nmap, which is one of the common ones. We chose the string nmap.org (1) in Packet bytes (2).
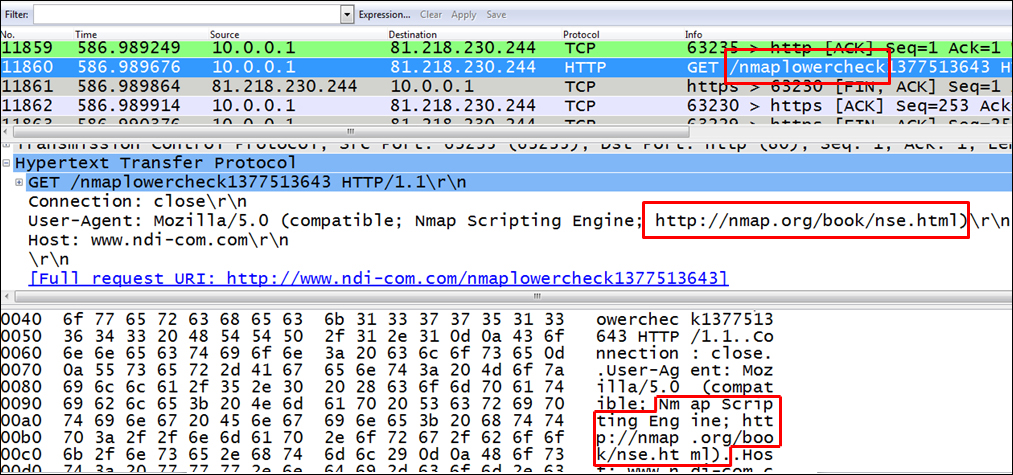
Another important issue is brute force attack, that is, when the attacker tries to guess the password in order to break into a server.
In the following screenshot, you'll see what happens when an attacker tries to break into a well-protected FTP server.
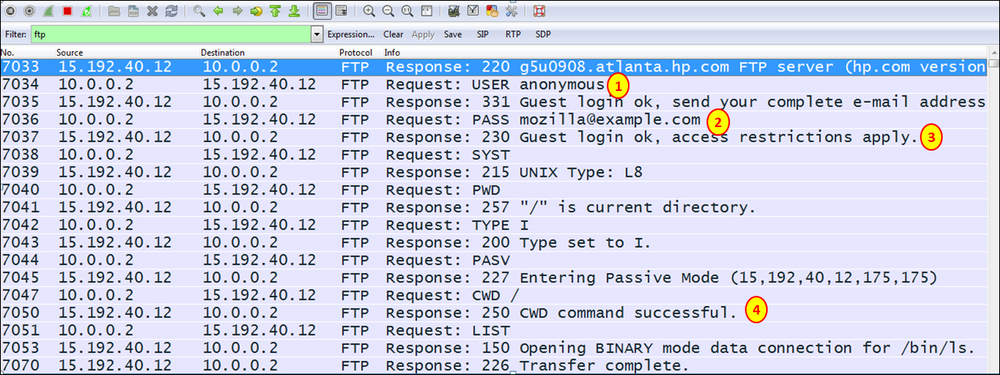
- Since it is FTP, the first trial is with username
anonymous(1), a password chosen by the attacker (2), login is, of course, approved (3), and the attacker gets in (4). - In the following screenshot, you see what happens when the attacker tries other usernames that are not authorized.
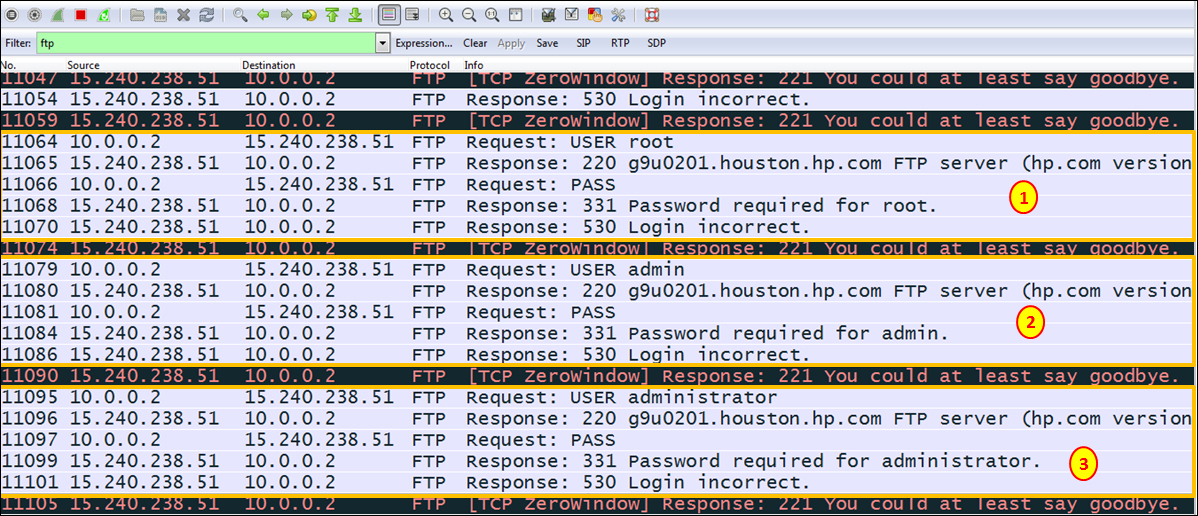
- Here, you can see that the attacker is trying to login with the usernames root (1), admin (2) and administrator (3).
- The attacker is blocked, and the server sends a TCP Zero-Window message and even answers by saying you could at least say goodbye.
-
No Comment