The transport layer protocols include TCP and UDP used to transport application protocols.
The User Datagram Protocol (UDP) is considered an unreliable transport. In this, there's no guarantee of packet delivery or ordering, but it has a lower overhead and is used by time-sensitive applications such as voice and video traffic.
The following screenshot shows the fields contained in an UDP header:
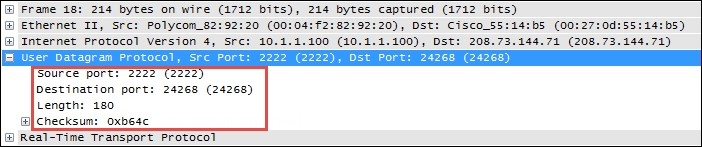
The UDP header is only 8-bytes long, consisting of:
- Source and Destination port number: This is 2 bytes each.
- Length: This is the length of the UDP header plus the payload. This is a 2-byte field.
- Checksum: This is a 2-byte field used to check for errors in the UDP header and data. If no checksum was generated by the transmitter, this will be all zeroes.
The Transmission Control Protocol (TCP) provides a reliable delivery of data by detecting lost, duplicated, or out-of-order packets, requesting retransmission of lost data, or rearranging packets in the right order before delivering them to the application. TCP can also accept a large chunk of data from an application and handle getting the data transported to the other end reliably using multiple packets and reassembling them at the other end.
The following screenshot highlights the significant fields of a basic TCP header:
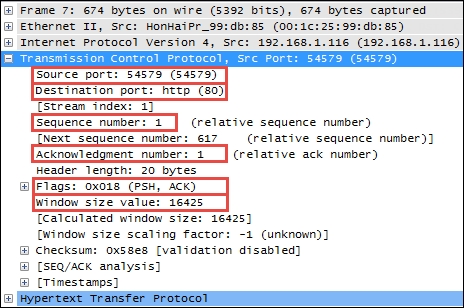
The TCP header contents and length can vary depending on options that may be in use, but in its simplest implementation it consists of:
- Source port and Destination port: These are well-known and registered ports are used (on servers) to access standard application services such as HTTP, FTP, SMTP, databases, and so on. Port numbers assigned to client/user sessions are usually in a higher number range and assigned sequentially.
- Sequence number: This is a number that represents the first octet in any given segment. Sequence numbers are initialized at the beginning of new sessions as a random number, and then incremented as data bytes are sent.
- Acknowledgment number: When the ACK flag bit is set, this field contains the next sequence number expected from the sender, which in turn acknowledges receipt of all the bytes received up to that point.
Note
The use of sequence and acknowledgment numbers is how TCP ensures reliable delivery of data by tracking the number and order of received bytes.
Sequence and acknowledgment numbers are large and difficult for humans to follow. Wireshark can convert and display these as relative values that start with 0 at the beginning of a session to make it easier to inspect them and relate the values to the number of bytes transmitted and received.
- Flags: These bits are used to control connection setups, terminations, and flow control mechanisms.
- Window size: This field indicates the current size of the buffer on this host used to store received data until it can be handed off to the receiving application. This information enables the sending host to adjust data flow rates in case of network or host congestion.
The following table lists the flags that are most commonly used in a TCP header:
|
Flag field name |
Description |
|---|---|
|
URG (urgent) |
This indicates the Urgent Pointer field (after the TCP header checksum) that should be examined. This flag is normally 0; the Urgent Pointer field is only examined if this bit is set. |
|
ACK (acknowledgment) |
This is the acknowledgment packet. |
|
PSH (push) |
This indicates whether the sending node's TCP stack should bypass any buffering and pass the data directly to the network and on to the receiving application. |
|
RST (reset) |
This is used to close the connection explicitly. |
|
SYN (synchronize) |
This is used to synchronize sequence numbers and used in a three-way TCP session initiation handshake process. |
|
FIN (finish) |
This is used when the transaction is finished. This does not mean that the connection is to be closed explicitly, but is commonly seen at the end of sessions. |
The TCP also supports a number of additional options, several of which are in common use in modern networks that you should be aware of. The snippet of a TCP header illustrated in the following screenshot depicts several of the most popular options:
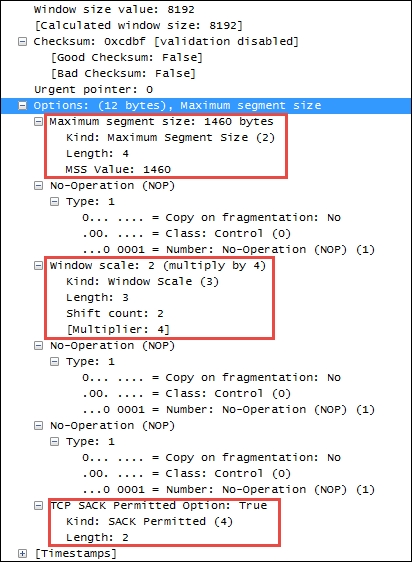
The TCP options highlighted in the preceding screenshot include:
- Maximum Segment Size: This option allows you to specify of the number of bytes that can follow the TCP header. This option exists to allow adjustment to accommodate VLAN tagging or Multiprotocol Label Switching (MPLS).
- Window Scale: This option overcomes the inability of the Window Size field in a standard TCP header to specify a window size greater than 65,535 bytes. Window scaling allows you to specify a factor to multiply the advertised window size to achieve a larger window size. Both sides of a session must be able to support this option for it to apply; this is determined during the session setup.
- TCP SACK Permitted Option: This option indicates that this node supports selective acknowledgments, which allows a node to acknowledge ongoing and incoming data packets while still asking for a specific missing packet. The recovery process only requires retransmission of the missing packet(s), instead of the missing packet and all the packets that followed. Both sides of a session must be able to support this option for it to apply, as determined during session setup.
