 Using the Protocol Hierarchy tool from the Statistics menu
by Charit Mishra, Yoram Orzach, James H Baxter
Wireshark Revealed: Essential Skills for IT Professionals
Using the Protocol Hierarchy tool from the Statistics menu
by Charit Mishra, Yoram Orzach, James H Baxter
Wireshark Revealed: Essential Skills for IT Professionals
- Wireshark Revealed: Essential Skills for IT Professionals
- Table of Contents
- Wireshark Revealed: Essential Skills for IT Professionals
- Credits
- Preface
- 1. Module 1
- 1. Getting Acquainted with Wireshark
- 2. Networking for Packet Analysts
- The OSI model – why it matters
- IP networks and subnets
- Switching and routing packets
- WAN links
- Wireless networking
- Summary
- 3. Capturing All the Right Packets
- Picking the best capture point
- Test Access Ports and switch port mirroring
- Capturing interfaces, filters, and options
- Verifying a good capture
- Saving the bulk capture file
- Isolating conversations of interest
- Using the Conversations window
- Wireshark display filters
- Filter Expression Buttons
- Following TCP/UDP/SSL streams
- Marking and ignoring packets
- Saving the filtered traffic
- Summary
- 4. Configuring Wireshark
- 5. Network Protocols
- The OSI and DARPA reference models
- Transport layer protocols
- Application layer protocols
- Summary
- 6. Troubleshooting and Performance Analysis
- Troubleshooting methodology
- Troubleshooting connectivity issues
- Troubleshooting functional issues
- Performance analysis methodology
- Top five reasons for poor application performance
- Summary
- 7. Packet Analysis for Security Tasks
- 8. Command-line and Other Utilities
- 2. Module 2
- 1. Introducing Wireshark
- 2. Using Capture Filters
- 3. Using Display Filters
- 4. Using Basic Statistics Tools
- Introduction
- Using the Summary tool from the Statistics menu
- Using the Protocol Hierarchy tool from the Statistics menu
- Using the Conversations tool from the Statistics menu
- Using the Endpoints tool from the Statistics menu
- Using the HTTP tool from the Statistics menu
- Configuring Flow Graph for viewing TCP flows
- Creating IP-based statistics
- 5. Using Advanced Statistics Tools
- Introduction
- Configuring IO Graphs with filters for measuring network performance issues
- Throughput measurements with IO Graph
- Advanced IO Graph configurations with advanced Y-Axis parameters
- Getting information through TCP stream graphs – the Time-Sequence (Stevens) window
- Getting information through TCP stream graphs – the Time-Sequence (tcp-trace) window
- Getting information through TCP stream graphs – the Throughput Graph window
- Getting information through TCP stream graphs – the Round Trip Time window
- Getting information through TCP stream graphs – the Window Scaling Graph window
- 6. Using the Expert Infos Window
- 7. Ethernet, LAN Switching, and Wireless LAN
- 8. ARP and IP Analysis
- 9. UDP/TCP Analysis
- Introduction
- Configuring TCP and UDP preferences for troubleshooting
- TCP connection problems
- TCP retransmission – where do they come from and why
- Duplicate ACKs and fast retransmissions
- TCP out-of-order packet events
- TCP Zero Window, Window Full, Window Change, and other Window indicators
- TCP resets and why they happen
- 10. HTTP and DNS
- 11. Analyzing Enterprise Applications' Behavior
- Introduction
- Finding out what is running over your network
- Analyzing FTP problems
- Analyzing e-mail traffic and troubleshooting e-mail problems – POP, IMAP, and SMTP
- Analyzing MS-TS and Citrix communications problems
- Analyzing problems in the NetBIOS protocols
- Analyzing database traffic and common problems
- 12. SIP, Multimedia, and IP Telephony
- Introduction
- Using Wireshark's features for telephony and multimedia analysis
- Analyzing SIP connectivity
- Analyzing RTP/RTCP connectivity
- Troubleshooting scenarios for video and surveillance applications
- Troubleshooting scenarios for IPTV applications
- Troubleshooting scenarios for video conferencing applications
- Troubleshooting RTSP
- 13. Troubleshooting Bandwidth and Delay Problems
- 14. Understanding Network Security
- A. Links, Tools, and Reading
- 3. Module 3
- 1. Welcome to the World of Packet Analysis with Wireshark
- 2. Filtering Our Way in Wireshark
- 3. Mastering the Advanced Features of Wireshark
- 4. Inspecting Application Layer Protocols
- 5. Analyzing Transport Layer Protocols
- 6. Analyzing Traffic in Thin Air
- 7. Network Security Analysis
- 8. Troubleshooting
- 9. Introduction to Wireshark v2
- Bibliography
- Index
In this recipe, we will learn how to get protocol hierarchy information of the data that runs over the network.
To use the Protocol Hierarchy tool from the statistics menu, go through the following steps:
- From the statistics menu, choose Protocol Hierarchy.

- What you will get here is data about the protocol distribution in the captured file. You will get the protocol distribution of the captured data, as shown in the following screenshot:
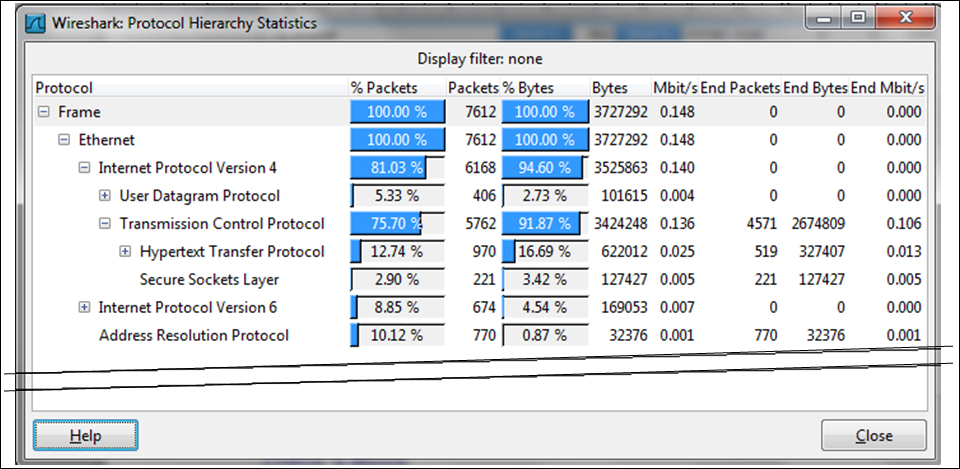
- You will get the following fields in the Protocol Hierarchy window:
- Protocol: This field specifies the protocol name
- % Packets: This field specifies the percentage of protocol packets from the total captured packets
- Packets: This field specifies the number of protocol packets from the total captured packets
- % Bytes: This field specifies the percentage of protocol bytes from the total captured packets
- Bytes: This field specifies the number of protocol bytes from the total captured packets
- Mbit/s: This field specifies the bandwidth of this protocol in relation to the capture time
- End Packets: This field specifies the total number of packets in this protocol (for the highest protocol in the decode file)
- End Bytes: This field specifies the absolute number of bytes of this protocol (for the highest protocol in the decode file)
- End Mbit/s: This field specifies the bandwidth of this protocol relative to the capture packets and time (for the highest protocol in the decode file)
Tip
The End Packets, End Bytes, and End Mbits/s columns are those in which the protocol in this line is the last protocol in the packet (that is, when the protocol comes at the end of the packet, and there is no higher layer information). These can be, for example, TCP packets with no payload (for example, SYN packets), which do not carry any upper layer information. That is why you see a 0 count for Ethernet and IPv4 and UDP end packets because there are no frames where these protocols are the last protocol in the frame.
In simple terms, it calculates statistics over the captured data. Some important things to notice are:
- The percentage always refers to the same layer protocols. For example, we see in the previous example that IPv4 has 81.03 percent of the packets, IPv6 has 8.85 percent of the packets, and ARP has 10.12 percent of the packets; a total of 100 percent of the protocols over layer-2.
- On the other hand, we see that TCP has 75.70 percent of the data, and within TCP, only 12.74 percent of the packets are HTTP, and there is nearly nothing more. This is because Wireshark counts only the packets with the HTTP headers. It doesn't count for example, the acknowledge packets or data packets that doesn't have HTTP header.
In order to ensure that Wireshark will also count the data packets, for example, the data packets of HTTP within the TCP packet, disable the Allow sub-dissector option to reassemble the TCP streams. You can do this from the Preferences menu or by right-clicking on the TCP in the Packet Details pane.
-
No Comment