When talking about host and network filters, we refer to Layer 3 filters that are IP address-based filters. In this recipe we will refer to these filters and what we can do with them.
The basic Layer 3 filters are:
iporip6: To capture IP or IPv6 packets.host <host>: To get host name or address.dst host <host>: To get destination host name or address.src host <host>: To get source host name or address.Tip
Host can be an IP address or a host name related with this number. You can type, for example, a filter host www.packtpub.com that will show you all packets to/from the IP address related to the Packt website.
gateway <Host name or address>: It captures traffic to or from the hardware address but not to the IP address of the host. This filter captures traffic going through the specified router. This filter requires a host name that is used and can be found by the local system's name resolution process (for example, DNS).net <net>: All packets to or from the specified IPv4/IPv6 network.dst net <net>: All packets to the specified IPv4/IPv6 destination network.src net <net>: All packets to the specified IPv4/IPv6 destination network.net <net> mask <netmask>: All packets to/from the specific network and mask. This syntax is not valid for the IPv6 network.dst net <net> mask <netmask>: All packets to/from the specific network and mask. This syntax is not valid for the IPv6 network.src net <net> mask <netmask>: All packets to/from the specific network and mask. This syntax is not valid for the IPv6 network.net <net>/<len>: All packets to/from the<net>network with<len>length in bits.dst net <net>/<len>: All packets to/from the<net>network with<len>length in bits.dst net <net>/<len>: All packets to/from the<net>network with<len>length in bits.broadcast: All broadcast packets.multicast: All multicast packets.ip proto <protocol code>: It captures packets while the IP protocol field equals to the<protocol>identifier. There can be various protocols, such as, TCP (Code 6), UDP (Code 17), ICMP (Code 1), and so on.ip6 proto <protocol>: It captures IPv6 packets with protocol as indicated in the type field. Note that this primitive does not follow the IPv6 extension headers chain.icmp[icmptype]==<identifier>: It captures ICMP packets, while the identifier is ICMP codes, such asicmp-echoandicmp-request.
Follow the instructions mentioned in the Configure capture filters recipe, and configure filters as follows:
- For capturing packets to/from host
10.10.10.1, configurehost 10.10.10.1. - For capturing packets to/from host at www.cnn.com, configure
host www.cnn.com. - For capturing packets to host
10.10.10.1, configuredst host 10.10.10.1. - For capturing packets from host
10.10.10.1, configuresrc host 10.10.10.1. - For capturing packets to/from network
192.168.1.0/24, configurenet 192.168.1ornet 192.168.1.0 mask 255.255.255.0ornet 192.168.1.0/24. - For capturing all data without broadcasts or without multicasts, configure
not broadcastornot multicast. - For capturing packets to/from the IPv6 network 2001::/16, configure
net 2001::/16. - For capturing packets to IPv6 host 2001::1, configure
host 2001::1. - For capturing only ICMP packets, configure
ip proto 1. - For filtering only ICMP Echo's pings, you can use ICMP messages or message codes. configure
icmp[icmptype]==icmp-echooricmp[icmptype]==8.
For host filtering, when you type a host name, Wireshark will translate the name to an IP address, and capture packets that refer to this address. For example, if you configure a filter host www.cnn.com, it will be translated by a name resolution service (mostly DNS) to an IP address, and will show you all packets going to and from this address. Note that in this case, if CNN website will forward you to other websites on other addresses, only packets to the first address will be captured.
Some more useful filters:
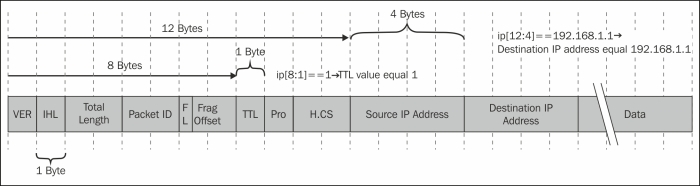
ip multicast: IP multicast packetsip broadcast: IP broadcast packetsip[2:2] == <number>: IP packet sizeip[8] == <number>: TTL (Time To Live) valueip[9] == <number>: Protocol value(ip[12:4] = ip[16:4]): IP source equal to IP destination addressip[2:2]==<number>: Total length or IP packetip[9] == <number>: Protocol identifier
These filters are further explained in the Configuring byte offset and payload matching filters recipe at the end of this chapter. The principle, as illustrated in the following diagram, is that the first number in the brackets defines how many bytes are from the beginning of the protocol header, and the second number indicates how many bytes to watch.
For more filters, refer to the tcpdump manual pages at http://www.tcpdump.org/tcpdump_man.html.
