Here, we will discuss two types of Wired Equivalent Privacy (WEP) authentication procedures: open and shared keys. As a matter of fact, discussing WEP is really unnecessary, but we should be aware of how it works because you never know when you might be asked to troubleshoot an old router whose firmware is still not upgraded and just supports WEP as an authentication mechanism.
WEP-open is way better than WEP-shared because even when the password that you provide turns out to be wrong, you will get connected to the network; here, it reduces the chance of getting the router brute forced. If you are using WEP-shared communication, then an experienced hacker won't take more than 2 minutes to crack your strongest key, and because of the small pool of keys that WEP supports, your password won't last long.
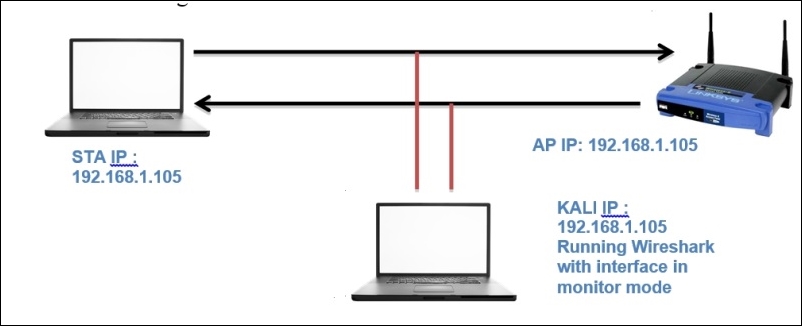
So, to begin with, we need the infrastructure to capture packets that are required for WEP-open. A key point to note here is that the infrastructure I am using consists of three different machines: the access point on the 192.168.1.1 IP, the station on the 192.168.1.105 IP, and Kali Linux running Wireshark on the 192.168.1.104 IP. Refer to the following illustration to understand this:
- First, let's activate the monitor mode over my interface:
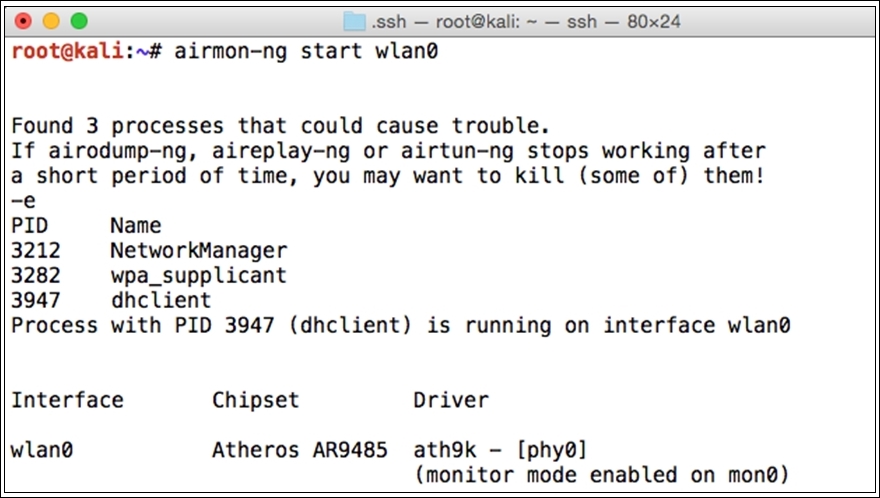
In the bottom-right corner of the preceding screenshot, you can see the message that the monitor mode is enabled over the
mon0interface. This is the same interface that we will use to capture802.11packets from our AP and STA. - Next, to confirm the channel over which my channel is working, I used the
airodump-ng mon0command.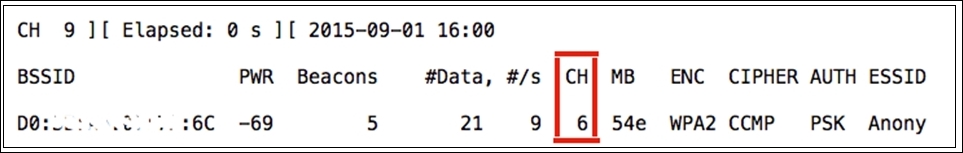
- Now, once we have figured out that the channel is
6, we can go ahead and make our interface listen specifically to this channel, thus avoiding any noise from other channels. To do so, I used theiwconfig mon0 channel 6command.
Figure 1: Configuring mon0 interface to channel 6
- Once you have completed all these steps, go ahead and launch Wireshark. If the output of the commands you issued gives any error, then please rectify it before you proceed.
Once the interface starts working fine and you are able to see the beacon frames broadcasted from your access point and probe request or response to and from your station, then you can simply launch a WEP-open authentication session. When asked for a password, just give any random password which will let you get connected to the network, but it might be possible that you won't be able to access the Internet connection shared by the AP with other STAs. Refer to the following screenshot depicting a WEP-open authentication session.
To capture the normal traffic pattern, I will use a Linux distribution (Kali) running on an independent machine that has a feature to activate the monitor mode (without the monitor mode, you can not capture 802.11 packets.) First, activate the monitor mode on our WLAN adapter using a basic set of commands, and we will also configure the same adapter to listen to a specific channel.
After launching Wireshark, make sure that you choose the mon0 interface only; then, you will be able to capture relevant traffic (keep the promiscuous mode on as well).
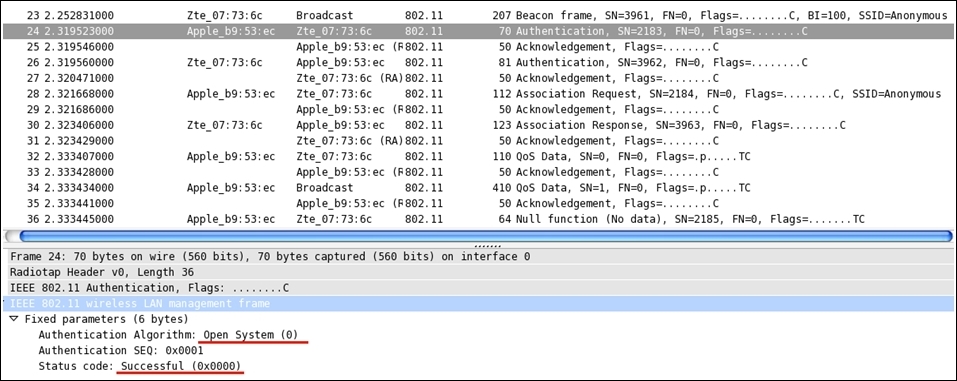
As clearly visible in the details pane of the first authentication frame selected in the list pane, the authentication system is Open-System (numeric code 0) and the connection attempt is successful as well. Following this, we can see an association request/response and then some QOS and Null function data frames.
An association request/response is sent and received by the STA/AP to associate a dropped connection, which the client was already a part of before, and to allocate the resources STA might require for communication over the channel.
A QOS data packet is a subtype of the control frame types, which depicts the quality of service and the over all performance.
Null Function packets are used to inform AP that the STA is going in the power-save mode. This packet does not carry any data, just some flag information.
And for every kind of information being shared between hosts, there are ACK packets that are sent across to determine the delivery of every packet in the communication.
Before we start configuring, I want you to understand the process of WEP-shared key authentication, that is, the steps involved in the whole session. Refer to the following illustration to understand this:
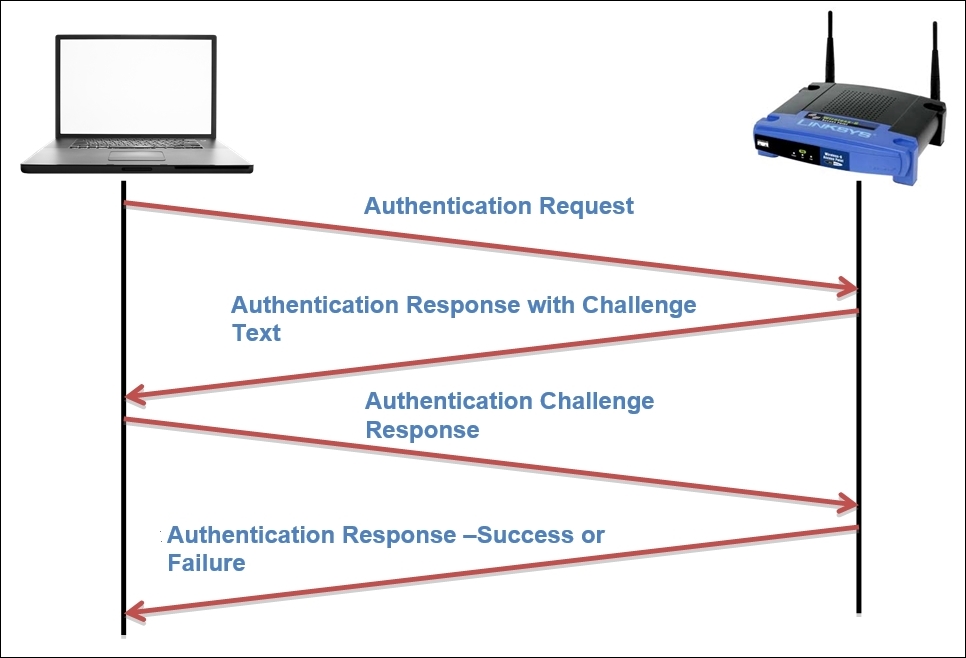
In short, the STA tries to connect to the AP by sending an authentication request, which the AP acknowledges by sending a text challenge that the STA is supposed to complete and before sending an encrypt using the key algorithm AP knows about. Once STA has completed the challenge process over his end, STA sends the challenge response which is being evaluated by the AP and determines the success or failure of the connection and the same is acknowledged to the STA in another authentication frame.
So, for a normal WEP authentication session, you will observe at least four authentication frames. If the authentication is successful, then the authentication frames will be followed by an association request/response along with some data transfer. And if the authentication is not successful, then after four authentication frames, the session between the STA and the AP will end. Follow the next steps to capture WEP management, control and data frames from your WLAN.
As discussed, you will note that the same pattern of packets is captured. Refer to the following screenshot depicting a successful WEP authentication session that was captured by Wireshark:
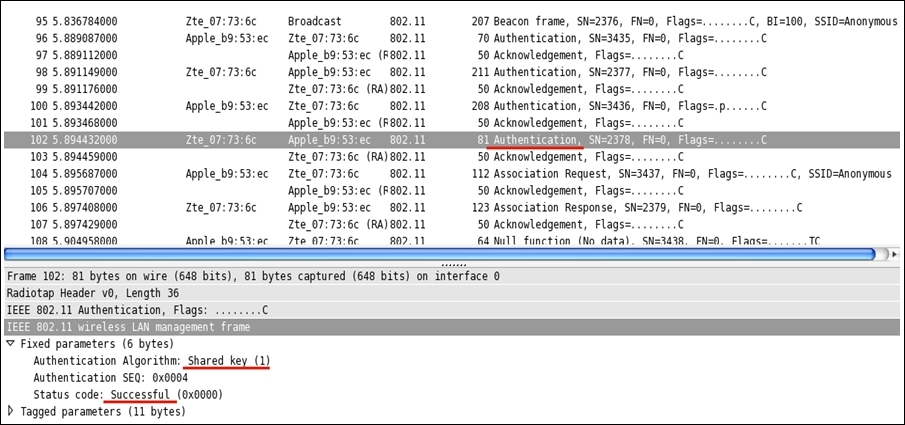
- For the fourth authentication frame, I have expanded the details section to confirm whether the connection attempt was successful or not. And from the preceding screenshot, we can verify that it was successful. The authentication type used for the communication can also be seen here.
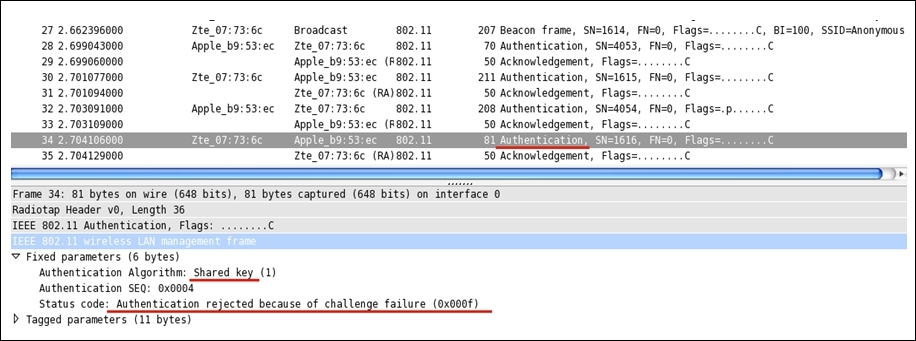
- As we know, now if the connection attempt between the STA and AP fails, the whole session will be terminated after the fourth authentication frame and we will see a failure message. To verify the same, I tried duplicating the scenario while Wireshark was listening through an interface in the monitor mode on an individual system.
- Refer to the following figure that illustrates a failed WEP connection attempt. In the list pane, we can see the same authentication frame pattern (just four authentication frames), but the last frame that the STA received from the AP acknowledges the connection status. As is clearly visible in the details pane, the connection attempt failed due to an incorrect challenge response text sent by the STA.
We witnessed two types of authentication procedures that WEP supports, but what is really important to know is that WEP is now obsolete, so I would never recommend to any of you to use this as an authentication protocol. If you have any old devices that only support WEP, then kindly upgrade to the latest hardware.
We talked about a crappy authentication algorithm that has been used since the birth of wireless networking, but when we have a better option, why not use it. I am talking about the Wi-Fi Protected Access (WPA) security algorithm that is stronger than WEP when we add the corrective measures required. In 2003 when WPA was launched by Wi-Fi Alliance as a measure to make WLAN communication stronger than the previous protocol, WEP. Nowadays, almost every WNIC supports WPA authentication mechanism, thus enabling you to take advantage of using a better security protocol. The Temporal Key Integrity Protocol (TKIP) lets the existing legacy hardware upgrade easily to implement WPA. The key size used by WEP was 40/104 bits, whereas WPA uses a key size of 256 bits, and the interesting thing to know is that every packet transmitted between the AP and STA is encrypted using the 256-bit key, which makes the situation quite tight for malicious users. One more advance was done in WPA that let the devices communicate with more assurance about the integrity of the message.
In WEP, the traditional CRC was implemented, but here, the popular Michael 64-bit Message Integrity Check (MIC) was introduced to address the issue. WPA also uses the RC4 algorithm to build a session based on dynamic encryption keys (you would never end up using the same key pair between two hosts). If compared to WEP, it has a larger IV size of 48 bits. Refer to the following illustration of how the cipher text is formed that is transmitted over the medium:
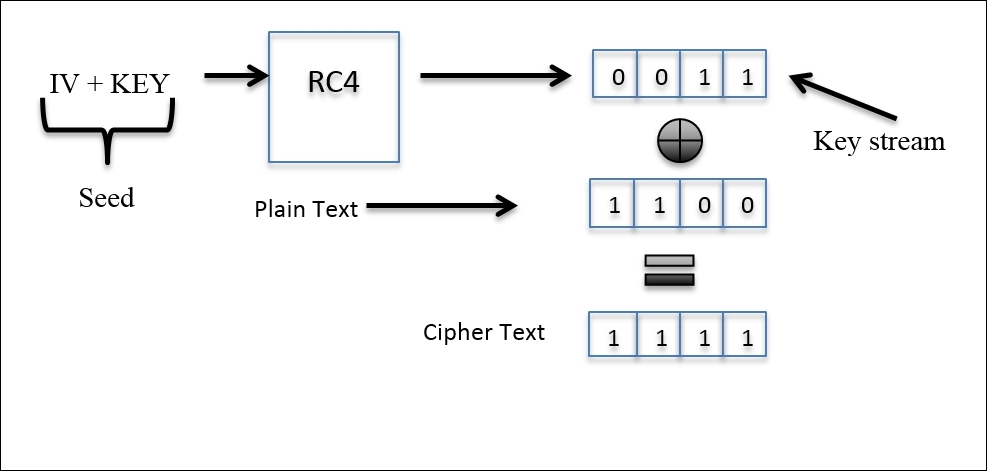
The preceding illustration depicts how the whole process starts by appending the IV and the dynamically generated 256-bit key. Then, is passed on to the RC4 algorithm, which encrypts the packets with keys, and then the resulting encrypted key stream is appended with the data and voila! We have the cipher text. Now, I will introduce you to the normal authentication session between an AP and an STA. Refer to the following figure for the same:
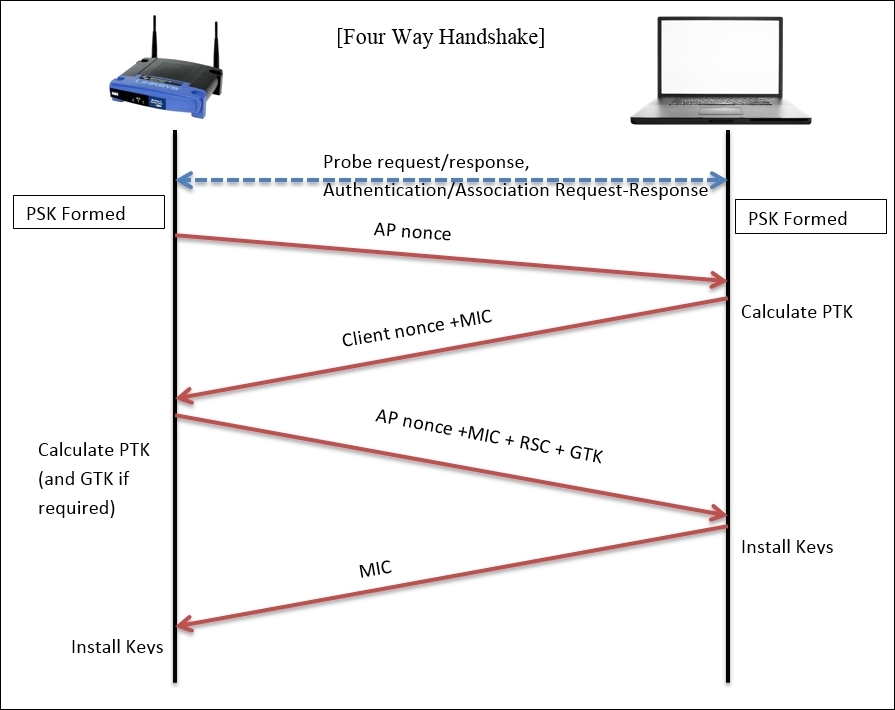
In the case of the Enterprise WPA configuration, first, the Master Key Exchange takes place. I will later give you a brief about it. As of now, we have an AP that sends its nonce (random value) to the STA (initiation of connection) that will use the AP's nonce value and its own nonce to calculate the Pairwise Transient Key (PTK) along with the Pre Shared Key (PSK), which was established during the initial connection process. The resulting value will be sent to the AP. Then, the AP will calculate the PTK over its end and append the MIC with the receive sequence counter (RSC) that helps in identifying the replayed messages. The resulting value will be passed on to the STA. Now, the STA will first verify the MIC in the message to ensure the integrity and install the keys. Then, a response will be sent to the AP regarding the status. If the status shows success, the AP then installs the same keys (dynamic keys) that will be used in further communication between the hosts.
After configuring WPA-Personal on my AP, I had sent an authentication request from my client and the corresponding communication was captured by Wireshark, which is shown in the following screenshot:
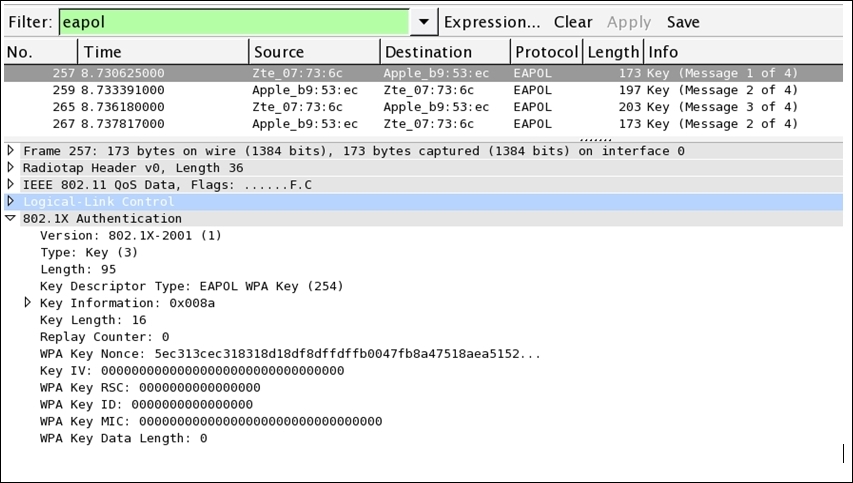
This is what a normal WPA successful handshake (authentication) process looks like, that is, four EAPOL packets. To analyze the session specifically between the AP and STA, I applied a display filter to see only EAPOL packets (authentication frames). Before the authentication frames, AP's beacon frame, and STA's probe, we looked at authentication and association request/response packets that led to the authentication session, following which PSK was used to generate the dynamic keys. Because of a software package error that I installed on my machine, the fourth packet says Message 2 of 4, whereas it should be Message 4 of 4.
Getting into more detail, I would like to show you the flags marked in all of these four authentication packets that will definitely clear your thoughts regarding the WPA handshake process. Refer to the following screenshot that illustrates this:
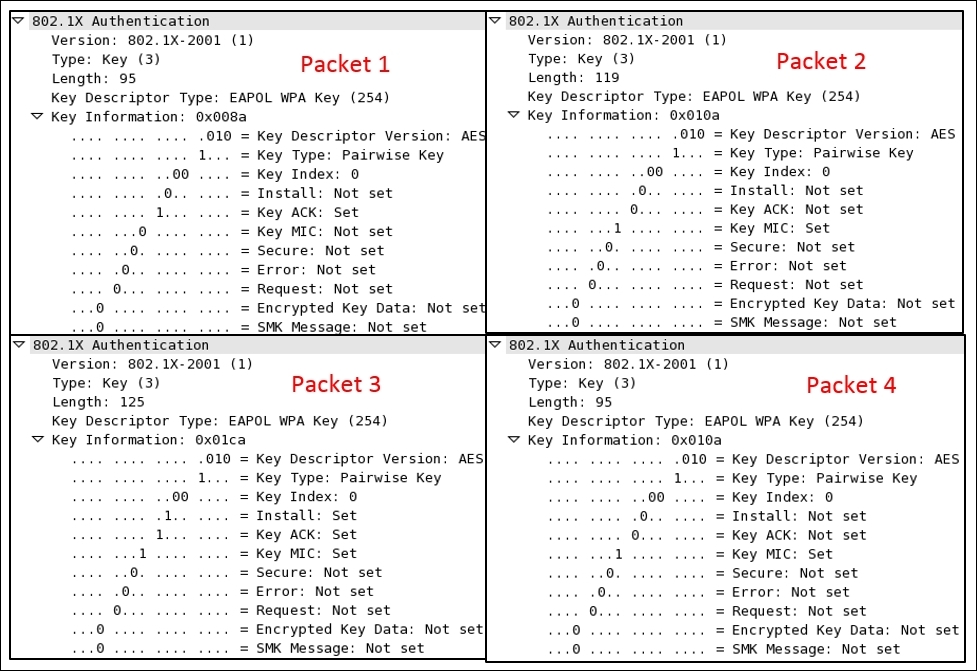
Here is the description of the preceding authentication packets:
- Packet 1: The pairwise master key (pre-shared key) and the
ACKbit are set (probably because of the association request/response exchanged earlier ), which was sent by the AP to STA to initiate the connection along with the nonce value that was chosen randomly. - Packet 2: The pairwise master key and the MIC flag is set, which STA sent to the AP to for acknowledging the request received, along with its own nonce value appended to the AP's nonce and the MIC for integrity check.
- Packet 3: The pairwise master key,
install, key ACK, and MIC flags are set, which the AP tries to send to the STA. The STA will fulfill the challenge text values received and will confirm to the AP along with the encrypted challenge text which AP is going to be crosschecked. - Packet 4: Here, the pairwise master key and the MIC flag are set, which the STA sends to the AP to make the connection complete. Now, the AP is mutually ready to perform data transfer with the STA.
I hope these flags help you understand the four-way handshake process in an easy and realistic manner.
Next, we are going to see what happens when the AP receives an incorrect challenge text from the STA, what the packets look like in the list pane, and whether there would there be any difference in the pattern of packets that are captured.
The STA will try to connect to the AP and the AP will request the challenge text. The STA this time is not aware of the secret keys used by other clients in the network, so ending with an incorrect pass key which won't be accepted by the AP, or please check acknowledged by the STA. The STA will try again to send the challenge text and the same process goes on. After this, you will notice a couple of similar packets in the list pane. Refer to the following figure for the same:
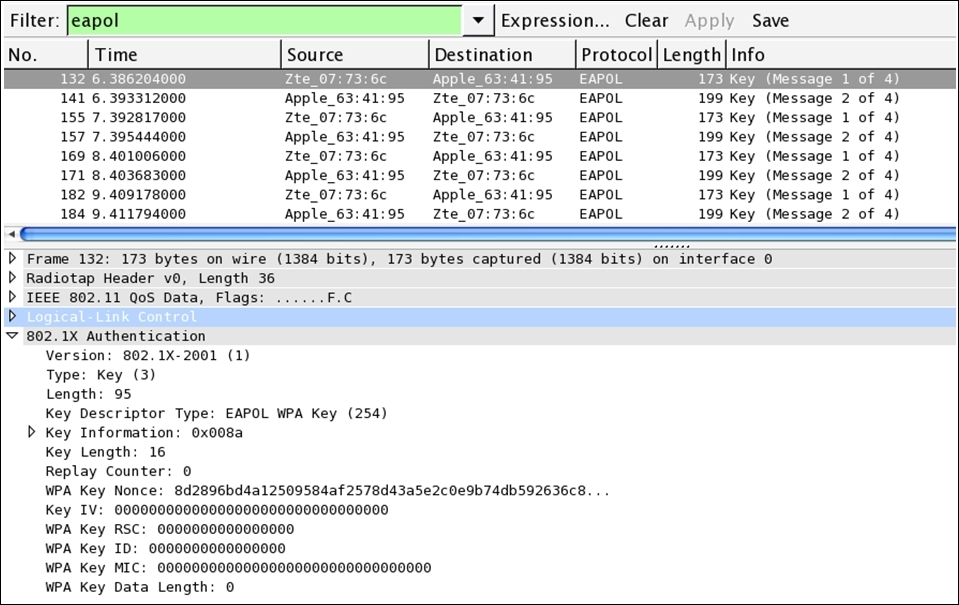
Figure 2: WPA Failed authentication
As you can see in the preceding screenshot, EAPOL Message 1 and 2 can only be seen because when the STA provides the challenge text response, the AP rejects it and again the process starts from beginning. The same thing will continue for a couple of times, but a packets pattern of such kind denotes unsuccessful connection attempts (may be a brute force attack). The packets listed can be associated with each other using the replay counter listed that we saw earlier in the key nonce in details section.
I promised we would be discussing the enterprise mode in brief, so here it is. In the corporate infrastructure, the key and passwords are not kept with the AP, and even the AP is not responsible for authentication with the STA. There is an extra entity, the RADIUS server, that takes care of authentication here. Before the four-way handshake takes place, the RADIUS server and the access point are supposed to go through a Master Key Exchange, which gives an assurance to both the communicating devices that the other part is legitimate. Let's have a look at the following figure:
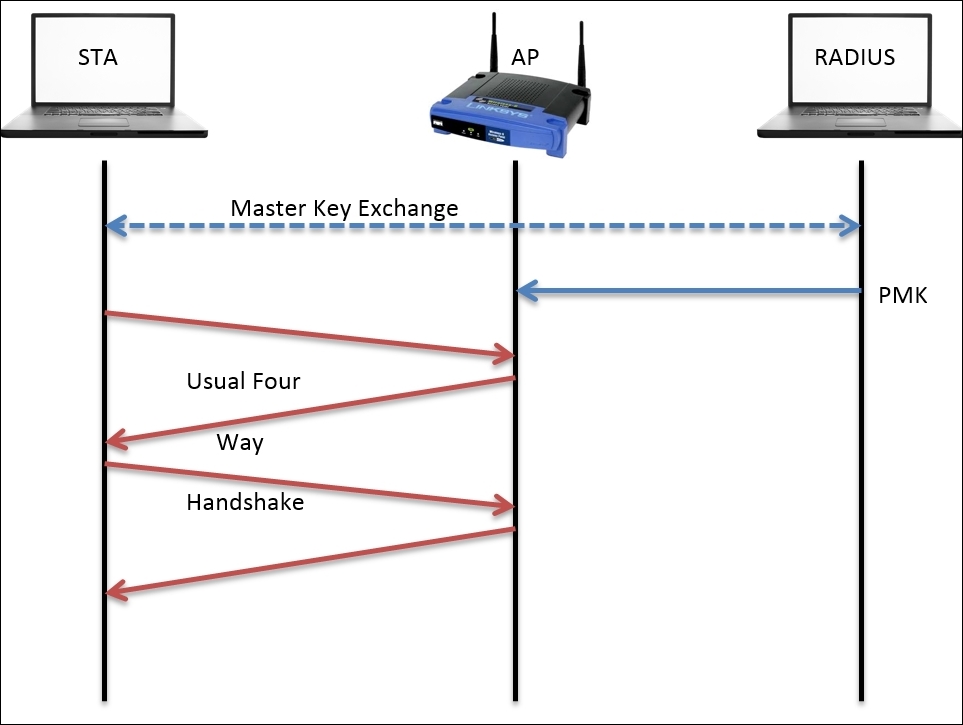
Afterwards, the pairwise master key is created and passed on to the AP, which will lead on and complete the four-way handshake process and complete the authentication session.
I've scrolled down the packet list and look what I found for you: Disassociation and Deauthentication packets in action captured by our sniffer. So, before we wrap up, you should take a look at them.
The wireless stations/access points use disassociation packets in order to notify the access point that the client is now going offline and the resources that have been allocated by the AP to wireless clients can now be released. Refer to the following figure that illustrates the same:
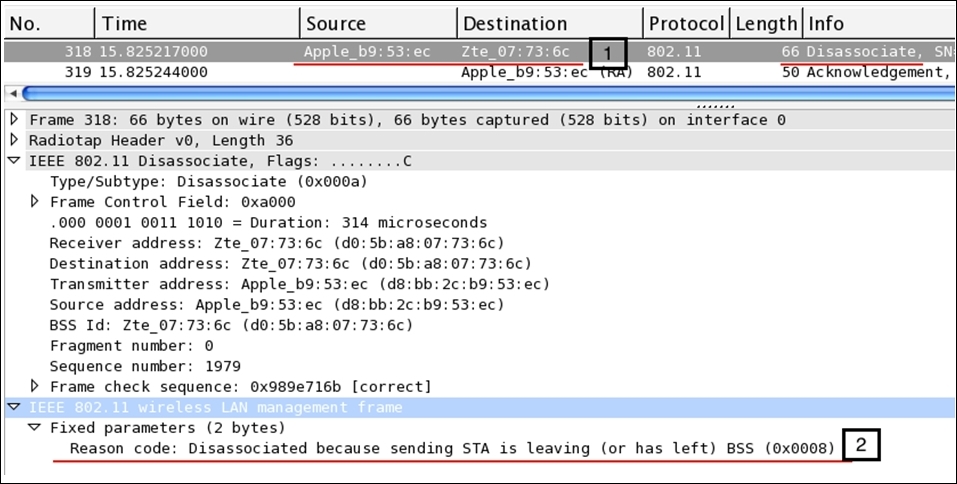
Figure 3: The disassociation packet
As you can observe, at first, the STA sends a disassociation frame and receives ACK (318,319) for the same. Now, for better understanding of the packets, we can take a look at the details pane (select the disassociation packet first), where the Reason Code parameter states that the STA is leaving or has already left. This gives us a feature through which we can view and understand packet behavior efficiently.
The wireless stations or the access points use the deauthentication frames to notify the other side of the communication that the other device is leaving. There can be several reasons for it. Refer to the following figure to understand this:
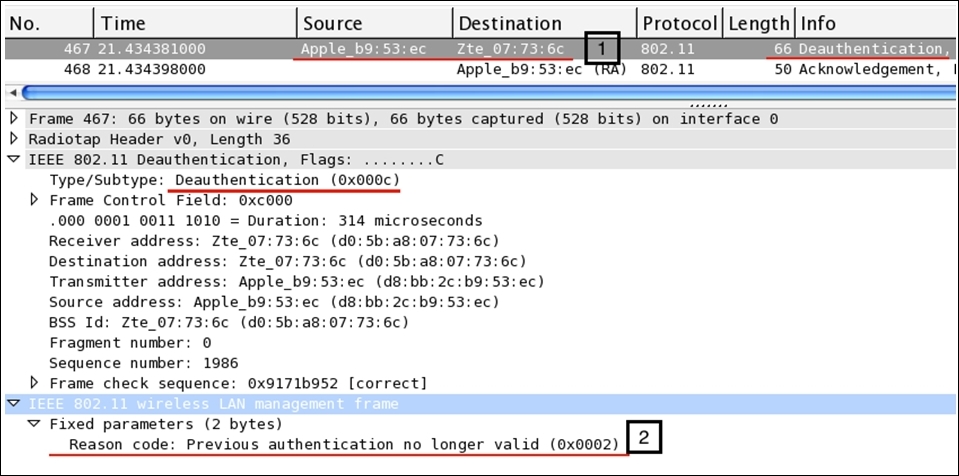
Figure 4: The deauthentication packet
First, the STA sends a deauthentication frame to the access point, which gets acknowledged in the next packets (467,468). After expanding the details section for the deauthentication packet, we can easily note that the Type/Subtype field is verifying the same. And at the bottom, we get to understand why the deauthentication packet was generated. In our case, it is Previous authentication no longer valid, which the STA tried to notify the AP about, and if they wish to communicate again in the future, then the process of authentication has to start over, from the probe and association frame, following the four-way handshake.
