 USBPcap
by Charit Mishra, Yoram Orzach, James H Baxter
Wireshark Revealed: Essential Skills for IT Professionals
USBPcap
by Charit Mishra, Yoram Orzach, James H Baxter
Wireshark Revealed: Essential Skills for IT Professionals
- Wireshark Revealed: Essential Skills for IT Professionals
- Table of Contents
- Wireshark Revealed: Essential Skills for IT Professionals
- Credits
- Preface
- 1. Module 1
- 1. Getting Acquainted with Wireshark
- 2. Networking for Packet Analysts
- The OSI model – why it matters
- IP networks and subnets
- Switching and routing packets
- WAN links
- Wireless networking
- Summary
- 3. Capturing All the Right Packets
- Picking the best capture point
- Test Access Ports and switch port mirroring
- Capturing interfaces, filters, and options
- Verifying a good capture
- Saving the bulk capture file
- Isolating conversations of interest
- Using the Conversations window
- Wireshark display filters
- Filter Expression Buttons
- Following TCP/UDP/SSL streams
- Marking and ignoring packets
- Saving the filtered traffic
- Summary
- 4. Configuring Wireshark
- 5. Network Protocols
- The OSI and DARPA reference models
- Transport layer protocols
- Application layer protocols
- Summary
- 6. Troubleshooting and Performance Analysis
- Troubleshooting methodology
- Troubleshooting connectivity issues
- Troubleshooting functional issues
- Performance analysis methodology
- Top five reasons for poor application performance
- Summary
- 7. Packet Analysis for Security Tasks
- 8. Command-line and Other Utilities
- 2. Module 2
- 1. Introducing Wireshark
- 2. Using Capture Filters
- 3. Using Display Filters
- 4. Using Basic Statistics Tools
- Introduction
- Using the Summary tool from the Statistics menu
- Using the Protocol Hierarchy tool from the Statistics menu
- Using the Conversations tool from the Statistics menu
- Using the Endpoints tool from the Statistics menu
- Using the HTTP tool from the Statistics menu
- Configuring Flow Graph for viewing TCP flows
- Creating IP-based statistics
- 5. Using Advanced Statistics Tools
- Introduction
- Configuring IO Graphs with filters for measuring network performance issues
- Throughput measurements with IO Graph
- Advanced IO Graph configurations with advanced Y-Axis parameters
- Getting information through TCP stream graphs – the Time-Sequence (Stevens) window
- Getting information through TCP stream graphs – the Time-Sequence (tcp-trace) window
- Getting information through TCP stream graphs – the Throughput Graph window
- Getting information through TCP stream graphs – the Round Trip Time window
- Getting information through TCP stream graphs – the Window Scaling Graph window
- 6. Using the Expert Infos Window
- 7. Ethernet, LAN Switching, and Wireless LAN
- 8. ARP and IP Analysis
- 9. UDP/TCP Analysis
- Introduction
- Configuring TCP and UDP preferences for troubleshooting
- TCP connection problems
- TCP retransmission – where do they come from and why
- Duplicate ACKs and fast retransmissions
- TCP out-of-order packet events
- TCP Zero Window, Window Full, Window Change, and other Window indicators
- TCP resets and why they happen
- 10. HTTP and DNS
- 11. Analyzing Enterprise Applications' Behavior
- Introduction
- Finding out what is running over your network
- Analyzing FTP problems
- Analyzing e-mail traffic and troubleshooting e-mail problems – POP, IMAP, and SMTP
- Analyzing MS-TS and Citrix communications problems
- Analyzing problems in the NetBIOS protocols
- Analyzing database traffic and common problems
- 12. SIP, Multimedia, and IP Telephony
- Introduction
- Using Wireshark's features for telephony and multimedia analysis
- Analyzing SIP connectivity
- Analyzing RTP/RTCP connectivity
- Troubleshooting scenarios for video and surveillance applications
- Troubleshooting scenarios for IPTV applications
- Troubleshooting scenarios for video conferencing applications
- Troubleshooting RTSP
- 13. Troubleshooting Bandwidth and Delay Problems
- 14. Understanding Network Security
- A. Links, Tools, and Reading
- 3. Module 3
- 1. Welcome to the World of Packet Analysis with Wireshark
- 2. Filtering Our Way in Wireshark
- 3. Mastering the Advanced Features of Wireshark
- 4. Inspecting Application Layer Protocols
- 5. Analyzing Transport Layer Protocols
- 6. Analyzing Traffic in Thin Air
- 7. Network Security Analysis
- 8. Troubleshooting
- 9. Introduction to Wireshark v2
- Bibliography
- Index
USBPcap has been there from a long time with Linux and Mac users, but for Windows, this is the first time that users will be able to sniff the activity over USB interfaces. So, let's quickly walk through this latest feature and try to understand how to work with it with the help of an example. Follow the given steps to replicate the scenario:
- After the successful installation of Wireshark on your Windows machine, it is highly recommended that you restart your machine because USBPcap might give you some trouble.
- After your PC has restarted, open Command Prompt and change your current directory to the USBpcap installation directory that should be located at
C:Program FilesUSBPcap. - Now, perform a directory listing using the
dircommand to check whetherUSBPcapCMD.exeis present in the directory. Refer to the following screenshot that represents this step: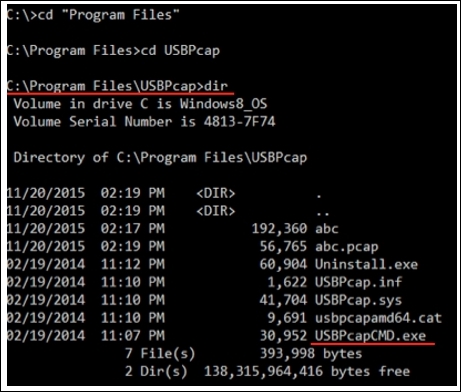
Figure 9.23: The USBPcap installation directory
- Type
USBPcapCMD.exein the Command Prompt to launch the sniffing application. - As soon as it has been launched successfully, you will be asked to choose a root hub over which you want to sniff the traffic and the name of the trace file where you want to redirect the output. Refer to following screenshot that illustrates this:
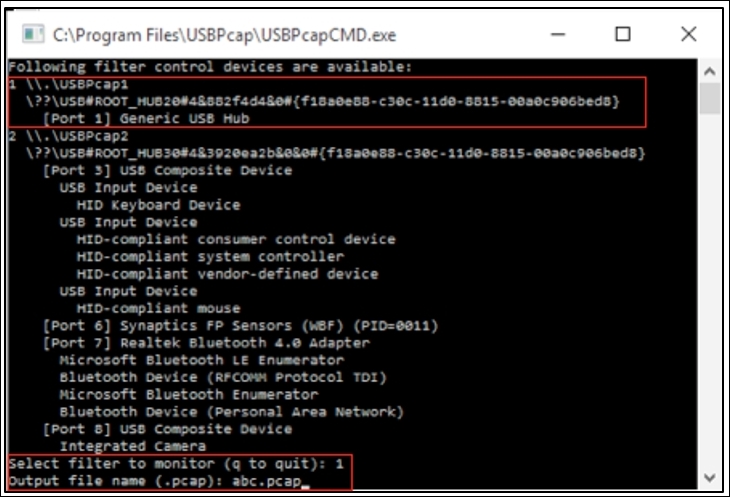
- Now, as instructed, the application will initiate the sniffing process over root hub 1 and will dump any activity captured over the USB interfaces to the
abc.pcapfile. - Now, try to copy something from your PC to the USB drive or vice versa. You probably won't be able to see any live activity over the Command Prompt, but in the background, it is actually running.
- Whenever you want to stop the sniffing process, you can press Ctrl + C.
- Now, it's time to open the abc.
pcap fileusing Wireshark to see what we have in the trace file. Refer to the following screenshot that illustrates this: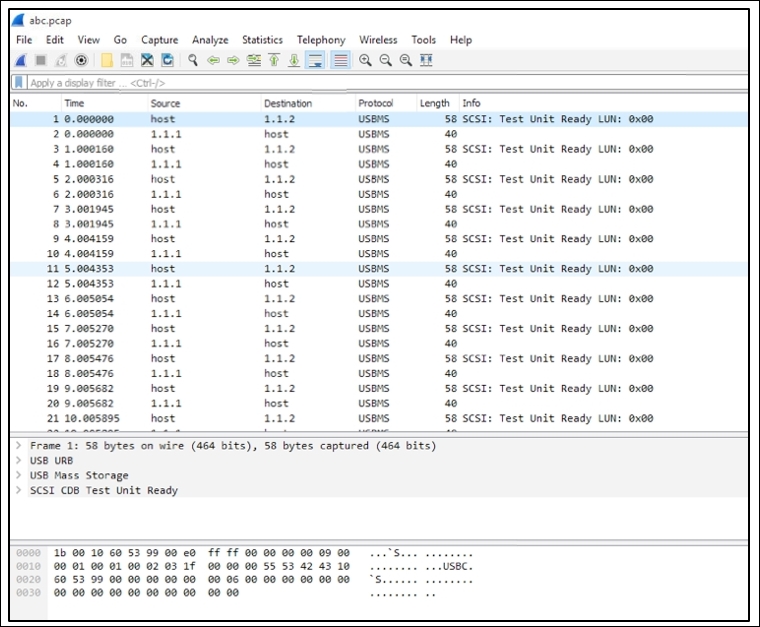
Figure 9.24: The
abc.pcaptrace file
As you can see, we have an activity, which got captured; it all looks similar to what we saw with network packets. We have all the familiar columns that list out various details such as time, source, destination, and so on. So we were able to successfully dump the activity over available USB interfaces without any technical hassle and I hope you will do some research to get a better understanding about USBPcap.
-
No Comment