The most common application layer protocols include DHCP used to obtain client IP addresses and configuration information, DNS for hostname resolution, HTTP, SMB, POP/SMTP, and FTP for the most common network services and SIP, RTP, and RTCP for VoIP and video conferencing.
Extensive coverage of all the upper layer protocols is beyond the scope of this book. A brief overview of DHCP and DNS will be provided, as these protocols universally support network operations and HTTP as an example of one of the most common application layer protocols. The reader is encouraged to research any or all of these protocols further depending on their scope of interest and need to meet the analysis tasks being addressed.
Dynamic Host Configuration Protocol (DHCP) allows a client to lease an IP address from a pool managed by a DHCP server. The client can receive other configuration options such as the default gateway, subnet mask, and one or more DNS server addresses as well. DHCP is derived from an older BOOTP protocol; Wireshark uses bootp in display filter syntax. DHCP works by the client sending a broadcast packet using UDP source port 67 to UDP destination port 68. A DHCP server will respond to the requestor's IP address and using UDP source port 68 to UDP destination port 67.
DHCP servers don't necessarily have to reside on the same local network segment as clients. A relay agent such as a router can forward DHCP requests and respond to/from a different network where a DHCP server resides.
Dynamic Host Configuration Protocol Version 6 (DHCPv6) is the IPv6 version of DHCP. Since IPv6 doesn't use broadcasts, DHCPv6 clients use the multicast address for All_DHCP_Relay_Agents_and_Servers (ff02::1:2) to locate DHCPv6 servers or relay agents.
Domain Name Service (DNS) is used to convert host names, such as www.wireshark.org to IP addresses. DNS can also be used to identify the hostname associated with an IP address (an inverse or pointer (PTR) query) and several other network information services. This is a good protocol to become familiar with as it is used extensively to locate nodes both within an enterprise and on the Internet using hostnames.
Hypertext Transfer Protocol (HTTP) is the application protocol used when someone browses (unsecured) websites on the Internet, along with the secure version (HTTPS). HTTP/1.1 is the current version—although HTTP/2.0 is starting to appear in some environments. Be aware that some network devices such as proxy servers and gateways may not support HTTP/2.0 yet.
An example of a HTTP packet delivering a GET request to a web server is depicted in the following screenshot:
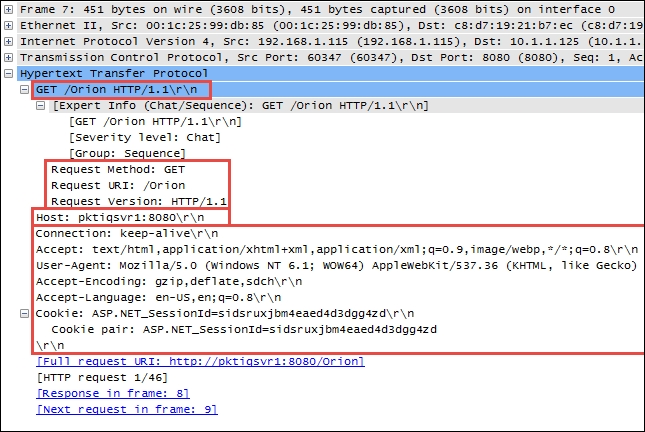
The most common features and fields of the HTTP protocol include HTTP Methods, Host, and Request Modifiers.
In the preceding screenshot, the HTTP header includes:
- Request Method: GET
- Request URI: /Orion (a home page on the web server)
- Request Version: HTTP/1.1
Some of the more common HTTP Methods are listed and described in the following table:
The
Host field identifies the target host and port number of the resource being requested. In the preceding screenshot, Host is pktiqsvr1 on port 8080.
HTTP requests and responses use Request Modifiers to provide details for the request. In the preceding screenshot, Request Modifiers includes:
- Connection: This indicates the preference for a persistent connection (keep-alive).
- Accept: This is a list of data formats (
text/htmlandapplication/xhtmlplusxml) accepted. - User-agent: This is a list of browser and operating system parameters (Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit) for the requesting device.
- Accept-encoding: This is a list of the acceptable HTTP compression schemes (
gzip,deflate, andsdch). - Accept-language: The acceptable languages (en-US and en; q=0.8) where q=0.8 is a relative quality factor that specifies the language the user would prefer on a scale of 0 to 1.
- Cookie: This is a session ID cookie (
ASP.NET_SessionId=sidsruxjbm4eaed4d3dgg4zd) that was previously stored on the user's browser in a cookie and is being provided to the website.
The following table lists some of the more commonly used modifiers:
Covering all the most common upper layer protocols or covering them to any great depth is obviously more than what can be included in a book of this size. I encourage you to spend some time studying those protocols that are of interest to you for personal or job-related reasons. The return on your investment in time will be well worth the effort.
Additional information for any of the protocols discussed in this chapter as well as all those not covered can be found online.
If you are inspecting a protocol within the Wireshark's Packet Details pane, you can right-click on a protocol header or field within a header and select the Wiki Protocol Page from the menu to go to the specific page on the Wireshark wiki that contains information on that protocol. More information can be found at http://wiki.wireshark.org/ProtocolReference.
You can also get a complete list of Wireshark display filters on specific protocols by selecting a protocol header or a field within a header, right-clicking, and selecting Filter Field Reference.
You can find general information on various protocols on Wikipedia. Start with the Internet protocol. Additional links to the entire Internet protocol suite are also provided at http://en.wikipedia.org/wiki/Internet_Protocol.
The Requests for Comment (RFC) documents contain detailed information for all the Internet protocols. These documents are maintained by the Internet Engineering Task Force (IETF) and are the final word on how the protocols should be implemented and function (http://www.ietf.org/rfc.html). If you want to search for a specific RFC by title or keyword, use the link http://www.rfc-editor.org/search/rfc_search.php.
