12.4 OSP Implemented with Partial Knowledge
In Sections 12.2 and 12.3, OSP assumes the complete knowledge of target signatures, ![]() . In many practical applications, obtaining such full knowledge is generally very difficult if not impossible, specifically, when the image background is not known. In this section, we investigate an issue of how to implement OSP when there is no full knowledge available, particularly, for the case that we are only interested in specific targets, but not image background or other natural signatures.
. In many practical applications, obtaining such full knowledge is generally very difficult if not impossible, specifically, when the image background is not known. In this section, we investigate an issue of how to implement OSP when there is no full knowledge available, particularly, for the case that we are only interested in specific targets, but not image background or other natural signatures.
In his dissertation (Harsanyi, 1993), Harsanyi relaxed the requirement of complete knowledge for OSP by developing an approach called CEM to circumvent this dilemma. The idea is to constrain the desired target signature, d with a specific gain while minimizing interfering effects caused by unknown signal sources. Since the undesired target signatures in U used by OSP are assumed to be unknown, the undesired target signatures in U are suppressed by minimizing their energies instead of being annihilated by a specific operator such as ![]() used in OSP. Despite the fact that the relationship between OSP and CEM was reported in Chang 2003a, 2003b) and Du et al. (2003), this section takes an alternative approach to show that with the same assumptions made for OSP, CEM actually performs exactly as does the least squares OSP,
used in OSP. Despite the fact that the relationship between OSP and CEM was reported in Chang 2003a, 2003b) and Du et al. (2003), this section takes an alternative approach to show that with the same assumptions made for OSP, CEM actually performs exactly as does the least squares OSP, ![]() .
.
12.4.1 CEM
Despite that CEM has been discussed in Section 2.2.3 it is a good idea for our subsequent treatment to recap its approach again as follows.
Let a remotely sensed image be a collection of image pixel vectors, denoted by ![]() where
where ![]() for
for ![]() is an L-dimensional pixel vector, N is the total number of pixels in the image, and L is the total number of spectral channels. The goal is to design a finite impulse response (FIR) linear filter with L filter coefficients
is an L-dimensional pixel vector, N is the total number of pixels in the image, and L is the total number of spectral channels. The goal is to design a finite impulse response (FIR) linear filter with L filter coefficients ![]() , denoted by an L-dimensional weighting vector
, denoted by an L-dimensional weighting vector ![]() that minimizes the filter output energy subject to the constraint
that minimizes the filter output energy subject to the constraint ![]() .
.
More specifically, let yi denote the output of the designed FIR filter resulting from the input ri. Then yi can be expressed by
and the average energy of the filter output is given by
where ![]() is the autocorrelation sample matrix of the image. CEM is developed to solve the following linearly constrained optimization problem:
is the autocorrelation sample matrix of the image. CEM is developed to solve the following linearly constrained optimization problem:
The optimal solution to (12.50) can be derived in Harsanyi (1993) and Chang (2002) by
With the optimal weighting vector wCEM specified by (12.51) a CEM filter, δCEM(r) was derived in Harsanyi (1993) and given by
Four special cases are of interest and described as follows.
12.4.1.1 d Is Orthogonal to U (i.e.,  ) and R = I (i.e., Spectral Correlation is Whitened)
) and R = I (i.e., Spectral Correlation is Whitened)
In this case, the noise in the image data to be processed is whitened and assumed to be zero-mean and de-correlated. So, the sample spectral correlation matrix R is reduced to the identity matrix I and ![]() . As a result, CEM becomes a normalized spectral matched filter, that is, R = I. On the other hand, if the desired target signature d is further assumed to be orthogonal to U, that is,
. As a result, CEM becomes a normalized spectral matched filter, that is, R = I. On the other hand, if the desired target signature d is further assumed to be orthogonal to U, that is, ![]() , then
, then ![]() . This implies that CEM is identical to OSP subject to a normalization constant
. This implies that CEM is identical to OSP subject to a normalization constant ![]() . Thus, both OSP and CEM can be considered as the same detector and reduced to a commonly used matched filter with the designated matched signature specified by d.
. Thus, both OSP and CEM can be considered as the same detector and reduced to a commonly used matched filter with the designated matched signature specified by d.
12.4.1.2 An Alternative Approach to Implementing CEM
Comparing δCEM(r) in (12.52) to δOSPD(r) in (12.9), δOSP(r) in (12.17) and ![]() in (12.22), we will discover that there is a very close relationship between
in (12.22), we will discover that there is a very close relationship between ![]() and
and ![]() . Since the knowledge of the undesired target signature matrix U assumed to be known in
. Since the knowledge of the undesired target signature matrix U assumed to be known in ![]() in δOSPD(r), δOSP(r), and
in δOSPD(r), δOSP(r), and ![]() is not available in δCEM(r), δCEM(r) must estimate
is not available in δCEM(r), δCEM(r) must estimate ![]() directly from the image data. One way of doing so is to approximate the “
directly from the image data. One way of doing so is to approximate the “![]() ” in the sense of minimum LSE by the inverse of the sample spectral information,
” in the sense of minimum LSE by the inverse of the sample spectral information, ![]() that can be obtained directly from the image data. More specifically, δCEM(r) makes use of the a posteriori information,
that can be obtained directly from the image data. More specifically, δCEM(r) makes use of the a posteriori information, ![]() to approximate the a priori information
to approximate the a priori information ![]() to accomplish what δOSPD(r), δOSP(r) and
to accomplish what δOSPD(r), δOSP(r) and ![]() do. The only difference is the scaling constant κ. Since both δOSPD(r) and δOSP(r) are used only for abundance detection, κ is set to 1. To the contrary,
do. The only difference is the scaling constant κ. Since both δOSPD(r) and δOSP(r) are used only for abundance detection, κ is set to 1. To the contrary, ![]() is an abundance estimator and the scaling constant
is an abundance estimator and the scaling constant ![]() is included to account for estimation error (Settle, 1996; Chang et al., 1998; Chang, 2003a). In this case, if we replace
is included to account for estimation error (Settle, 1996; Chang et al., 1998; Chang, 2003a). In this case, if we replace ![]() in (12.22) with R−1,
in (12.22) with R−1, ![]() becomes δCEM(r). This suggests that δCEM(r) can be considered as
becomes δCEM(r). This suggests that δCEM(r) can be considered as ![]() with the partial knowledge specified by the desired target signature d and the sample spectral information provided by
with the partial knowledge specified by the desired target signature d and the sample spectral information provided by ![]() used to replace the unknown signature matrix
used to replace the unknown signature matrix ![]() .
.
As noted above, the a posteriori information ![]() used in δCEM(r) is intended to approximate the a priori information
used in δCEM(r) is intended to approximate the a priori information ![]() used in δOSP(r). However, the
used in δOSP(r). However, the ![]() excludes the information provided by the desired target signature d, which is included in
excludes the information provided by the desired target signature d, which is included in ![]() . This observation suggests that a more accurate data sample correlation matrix used by δCEM(r) should be the one that removes all the pixel vectors specified by d from R. We let
. This observation suggests that a more accurate data sample correlation matrix used by δCEM(r) should be the one that removes all the pixel vectors specified by d from R. We let ![]() be such a matrix that excludes all target pixel vectors specified by d and be defined by
be such a matrix that excludes all target pixel vectors specified by d and be defined by
where the superscript “i” runs through all target pixel vectors whose signatures are specified by d and ![]() indicates their respective abundance fractions contained in pixel vector
indicates their respective abundance fractions contained in pixel vector ![]() . Equation (12.53) allows us to rewrite
. Equation (12.53) allows us to rewrite ![]() in (12.49) as
in (12.49) as
Because of the constraint ![]() ,
, ![]() . In addition, the second term in the right-hand side of (12.54),
. In addition, the second term in the right-hand side of (12.54), ![]() , is independent of w. Solving (12.50) is equivalent to solving the following optimization problem:
, is independent of w. Solving (12.50) is equivalent to solving the following optimization problem:
(12.55) ![]()
with the optimal solution given by
where the w∗ can be obtained by wCEM in (12.51) by simply replacing ![]() with
with ![]() . Therefore, technically speaking, (12.56) should be a more appropriate form for CEM, which is also demonstrated in Chang (2003a, pp. 63–67). Nevertheless, the CEM solution outlined by (12.50), (12.50)–(12.52) is still desirable in two aspects. One is that if the number of target pixel vectors specified by the desired signature d is small, the impact of without removing these pixel vectors will be little and not be significant. Another is that in many practical applications, finding all pixel vectors that are specified by the desired signature d may not be realistic, particularly, if the d is a mixed pixel vector.
. Therefore, technically speaking, (12.56) should be a more appropriate form for CEM, which is also demonstrated in Chang (2003a, pp. 63–67). Nevertheless, the CEM solution outlined by (12.50), (12.50)–(12.52) is still desirable in two aspects. One is that if the number of target pixel vectors specified by the desired signature d is small, the impact of without removing these pixel vectors will be little and not be significant. Another is that in many practical applications, finding all pixel vectors that are specified by the desired signature d may not be realistic, particularly, if the d is a mixed pixel vector.
12.4.1.3 CEM Implemented in Conjunction with 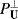
More interestingly, when the U is actually known, CEM should be able to take advantage of this knowledge to annihilate the undesired signatures via ![]() instead of suppressing these signatures. In this case, the resulting r in (12.48) becomes
instead of suppressing these signatures. In this case, the resulting r in (12.48) becomes ![]() and the desired target signature d is also projected to
and the desired target signature d is also projected to ![]() . Consequently, the constraint
. Consequently, the constraint ![]() and the object function
and the object function ![]() in (12.50) must be replaced with
in (12.50) must be replaced with ![]() and
and ![]() , respectively, which results in
, respectively, which results in
(12.57) 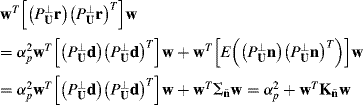
where ![]() the cross-term
the cross-term ![]() vanishes if n is zero-mean. As a consequence, (12.50) is reduced to
vanishes if n is zero-mean. As a consequence, (12.50) is reduced to
In order to see the relationship between OSP and CEM, we use (12.5) to obtain the filter output SNR as follows:
(12.59) 
So, solving (12.58) is equivalent to finding the solution to the following constrained optimization problem:
Now, we use the Largrangian multiplier method by differentiating the following Largrangian:
(12.61) ![]()
with respective to w and setting it to 0, and obtain
(12.62) ![]()
and
with
derived by the constraint ![]() . Substituting (12.64) for λ into (12.63) yields
. Substituting (12.64) for λ into (12.63) yields
CEM specified by (12.65) is called CEM implemented in conjunction with ![]() and denoted by
and denoted by ![]() .
.
12.4.1.4 CEM Implemented in Conjunction with 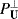 in White Noise
in White Noise
If we further assume that the noise in (12.60) is white and given by ![]() , (12.60) is reduced to finding a weighting vector w with the minimum vector length subject to the constraint
, (12.60) is reduced to finding a weighting vector w with the minimum vector length subject to the constraint ![]() , namely,
, namely,
(12.66) ![]()
and (12.65) becomes
Let the filter specified by (12.67) be denoted by ![]() in which case, CEM assumes that noise is white and the knowledge of the U is provided a priori. Implementing in conjunction with the undesired signature projector
in which case, CEM assumes that noise is white and the knowledge of the U is provided a priori. Implementing in conjunction with the undesired signature projector ![]() ,
, ![]() becomes the LS estimator
becomes the LS estimator ![]() given by (12.22) as well as the Gaussian maximum likelihood estimator
given by (12.22) as well as the Gaussian maximum likelihood estimator ![]() given by (12.46), respectively. This implies that if the noise is zero mean and white, and the undesired target signatures are annihilated by
given by (12.46), respectively. This implies that if the noise is zero mean and white, and the undesired target signatures are annihilated by ![]() , then
, then ![]() performs as if it is an abundance fraction estimator.
performs as if it is an abundance fraction estimator.
12.4.2 TCIMF
CEM is originally designed to detect a single target signature. If there are multiple targets to be detected, the detection must be carried out one target at a time. In order to extend CEM to a multiple-target detection technique, a TCIMF was recently developed by Ren and Chang (2001) that can be viewed as a generalization of OSP and CEM.
Let ![]() denote the desired target signature matrix and
denote the desired target signature matrix and ![]() be the undesired target signature matrix where nD and nU are the number of the desired target signatures and the number of the undesired target signatures, respectively. Now, we can develop an FIR filter that passes the desired target signatures in D using an
be the undesired target signature matrix where nD and nU are the number of the desired target signatures and the number of the undesired target signatures, respectively. Now, we can develop an FIR filter that passes the desired target signatures in D using an ![]() unity constraint vector
unity constraint vector ![]() while annihilating the undesired target signatures in U using an
while annihilating the undesired target signatures in U using an ![]() zero constraint vector
zero constraint vector ![]() . In doing so, the constraint in (12.50) is replaced by
. In doing so, the constraint in (12.50) is replaced by
(12.68) ![]()
and the optimization problem in (12.50) becomes the following linearly constrained optimization problem:
The filter solving (12.69) is called target-constrained interference-minimized filter (TCIMF) (Ren and Chang, 2001) and given by
(12.70) ![]()
with the optimal weighting vector, wTCIMF given by
A discussion on the relationship between OSP and CEM via TCIMF can be found in Chang 2002, 2003a). In what follows, we describe more details about this relationship by considering three special cases of δTCIMF(r).
12.4.2.1  with
with 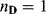 and
and 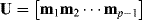 with
with 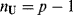
In this case, δTCIMF(r) performs like ![]() . However, there is a difference in the sense of algorithm implementation. The former performs extraction of the desired signature mp and annihilation of the undesired signatures
. However, there is a difference in the sense of algorithm implementation. The former performs extraction of the desired signature mp and annihilation of the undesired signatures ![]() simultaneously, whereas the latter performs the undesired signature annihilation using
simultaneously, whereas the latter performs the undesired signature annihilation using ![]() followed by CEM, δCEM(r) in sequence. Therefore, despite the fact that both filters may produce the same results, they should be considered as separate filters. In particular, δTCIMF(r) can be carried out in real time as noted in Chang (2003a) and Chang et al. (2001).
followed by CEM, δCEM(r) in sequence. Therefore, despite the fact that both filters may produce the same results, they should be considered as separate filters. In particular, δTCIMF(r) can be carried out in real time as noted in Chang (2003a) and Chang et al. (2001).
12.4.2.2  with
with  and
and 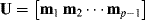 with
with 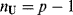 and
and 
In this case, δTCIMF(r) performs like δOSP(r), but in the mean time, it also suppresses all signatures other than desired and undesired target signatures, an operation that OSP does not do. Let the resulting weighting vector be denoted by ![]() and its corresponding TCIMF be denoted by
and its corresponding TCIMF be denoted by ![]() . As derived in Chang (2002) and Chang (2003a), the
. As derived in Chang (2002) and Chang (2003a), the ![]() can be shown to be equivalent to
can be shown to be equivalent to ![]() or δOSP(r) as follows:
or δOSP(r) as follows:
where ![]() , and
, and
It should be noted that the extra constant κ in (12.73) is a result of interference/noise suppression from TCIMF that OSP does not have.
12.4.2.3 D = d and  (i.e., Only the Desired Signature d is Available)
(i.e., Only the Desired Signature d is Available)
In this case, TCIMF is further reduced to CEM given by
So, on one end, OSP and CEM can be considered as special cases of TCIMF by virtue of (12.71). On the other end, OSP can be also interpreted as a noise-whitened version of TCIMF with interference/noise suppression in (12.72). In addition, CEM can be also considered as an undesired target signature-suppressed version of TCIMF in (12.74). Nevertheless, there is a subtle and substantiate distinction between TCIMF and other filters such as OSP and CEM. TCIMF can be implemented to detect and classify multiple targets, annihilate undesired targets, and suppress unknown signal sources in one-shot operation in real time (Chang et al. 2001), whereas δCEM(r) and ![]() must be carried out for detection of a single target at a time.
must be carried out for detection of a single target at a time.
12.4.3 Examples
In this subsection, we conduct a comparative analysis between OSP and CEM with the undesired signatures annihilated by OSP.
Example 12.3
(Comparative Study Between (d,U)-Model and OSP-Model)
This example assumed that the complete knowledge of target signatures was available. We study how the undesired signatures in U affect the performance of ![]() . The same 401 simulated pixels used in Example 12.1 were also used in this example with added SNR 30:1 white Gaussian noise so that the results of δOSP(r) and
. The same 401 simulated pixels used in Example 12.1 were also used in this example with added SNR 30:1 white Gaussian noise so that the results of δOSP(r) and ![]() derived in Example 12.1 can be used for comparison. Two scenarios were studied. One was the U made up of dry grass and red soil. Figure 12.7 shows the detection results of δCEM(r) and
derived in Example 12.1 can be used for comparison. Two scenarios were studied. One was the U made up of dry grass and red soil. Figure 12.7 shows the detection results of δCEM(r) and ![]() with dry grass and red soil annihilated by
with dry grass and red soil annihilated by ![]() . Table 12.3 tabulates their respective LSEs.
. Table 12.3 tabulates their respective LSEs.
As we can see from Table 12.3, ![]() with the dry grass and red soil annihilated performed slightly better than δCEM(r) that only suppressed the dry grass and red soil. However, if we further considered another scenario which included the sagebrush in the U as another undesired signature even if it was absent in the 401 simulated pixel vectors to repeat the same experiment.
with the dry grass and red soil annihilated performed slightly better than δCEM(r) that only suppressed the dry grass and red soil. However, if we further considered another scenario which included the sagebrush in the U as another undesired signature even if it was absent in the 401 simulated pixel vectors to repeat the same experiment.
Figure 12.8 shows the detection results of δCEM(r) and ![]() with dry grass, red soil, and sagebrush annihilated.
with dry grass, red soil, and sagebrush annihilated.
As we can see clearly from Figure 12.8, ![]() with the annihilation of U performed poorly compared to its counterpart δCEM(r). This was because the signature of the sagebrush was so close to that of creosote leaves as shown in Chang (2000) and Chang (2003a) that the annihilation of sagebrush also eliminated most part of the signature of the creosote leaves, which resulted in significant deterioration of signal detectability of
with the annihilation of U performed poorly compared to its counterpart δCEM(r). This was because the signature of the sagebrush was so close to that of creosote leaves as shown in Chang (2000) and Chang (2003a) that the annihilation of sagebrush also eliminated most part of the signature of the creosote leaves, which resulted in significant deterioration of signal detectability of ![]() . This example demonstrated a significant difference between annihilation of undesired signatures and suppression of undesired signatures.
. This example demonstrated a significant difference between annihilation of undesired signatures and suppression of undesired signatures.
Example 12.4
(Partial Knowledge)
The same 401 simulated pixel vectors used in Example 12.1 were once again used for the following experiments except that the blackbrush and sagebrush were added to pixel vector numbers 98–102 and pixel numbers 298–302, respectively, at abundance fractions 10% while reducing the abundance of red soil and dry grass by multiplying their abundance fractions by 90%. In this case, there were three target signatures of interest, blackbrush, creosote leaves, and sagebrush with two background signatures, red soil, and dry grass. In this example, the complete knowledge of targets of interest, blackbrush, creosote leaves, and sagebrush was also assumed to be available and the background signatures, soil and dry grass were unknown and considered to be interferers as interference. We also let d be the desired target signature and U consists of the other two known target signatures. Like Example 12.3, CEM was implemented in conjunction with/without ![]() ,
, ![]() and δCEM(r), respectively. Figure 12.9 shows the detection results of δOSP(r),
and δCEM(r), respectively. Figure 12.9 shows the detection results of δOSP(r), ![]() , δCEM(r), and
, δCEM(r), and ![]() where figures labeled by (a), (b), and (c) are detection results of blackbrush, creosote leaves and sagebrush, respectively, with the U formed by the other two signatures that serve as undesired signatures.
where figures labeled by (a), (b), and (c) are detection results of blackbrush, creosote leaves and sagebrush, respectively, with the U formed by the other two signatures that serve as undesired signatures.
As shown in Chang (2000, 2003a), the three target signatures, blackbrush, creosote leaves, and sagebrush, were very similar. As a consequence, annihilating any two of these three signatures would certainly have tremendous impacts on the detection performance of the third signature. The results of Figures 12.9 confirmed what we expected. That is, detecting one signature also detected the other two signatures. Additionally, it also significantly deteriorated the ability of ![]() in estimating abundance fractions as shown in Figure 12.9 where the estimated abundance fractions of each of the three signatures were far more being accurate as tabulated in Table 12.4.
in estimating abundance fractions as shown in Figure 12.9 where the estimated abundance fractions of each of the three signatures were far more being accurate as tabulated in Table 12.4.
Surprisingly, the detection of creosote leaves was quite different from that of blackbrush and sagebrush, as δOSP(r) and ![]() were implemented. The detection of creosote leaves also detected significant amounts of blackbrush and sagebrush signatures by suppressing the background signatures even if it was not supposed to do so. The detection of blackbrush and sagebrush showed very similar results and also detected visible amounts of the three signatures except that different amounts of abundance fractions of the background signatures, drygrass, and redsoil were detected. Similar phenomena were also observed from the detection results of δCEM(r) and
were implemented. The detection of creosote leaves also detected significant amounts of blackbrush and sagebrush signatures by suppressing the background signatures even if it was not supposed to do so. The detection of blackbrush and sagebrush showed very similar results and also detected visible amounts of the three signatures except that different amounts of abundance fractions of the background signatures, drygrass, and redsoil were detected. Similar phenomena were also observed from the detection results of δCEM(r) and ![]() where detection of one signature also picked up the other signatures. Because the spectra of these three signatures were very similar,
where detection of one signature also picked up the other signatures. Because the spectra of these three signatures were very similar, ![]() used in
used in ![]() also annihilated part of the desired signature before the detection of the desired signature. Consequently,
also annihilated part of the desired signature before the detection of the desired signature. Consequently, ![]() performed poorly compared to δCEM(r).
performed poorly compared to δCEM(r).
Since the soil and dry grass were used as interference, TCIMF was implemented in two scenarios. One was with d = a single desired target signature and U = [drygrass redsoil], and the other was with D = [blackbrush, creosote leaves, sagebrush] and U = [drygrass redsoil]. Figure 12.10 shows their detection results of δTCIMF(r) where Figure 12.10(a)–(c) was detection results of blackbrush, creosote leaves, and sagebrush, respectively, and Figure 12.10(d) was the simultaneous detection result of the three signatures blackbrush, creosote leaves and sagebrush with D = [blackbrush (B), creosote leaves (C), sagebrush (S)].
As indicated previously, when TCIMF was implemented with a single target signature designated as the desired signature D = d, it would perform as it were ![]() . This was verified by comparing the results of
. This was verified by comparing the results of ![]() in Figure 12.9 to δTCIMF(r) in Figure 12.10(a)–(c). Interestingly, it was not true as shown in Figure 12.10(d) when δTCIMF(r) was implemented with D = [blackbrush, creosote leaves, sagebrush] and U = [dry grass, red soil] where it performed significantly better than
in Figure 12.9 to δTCIMF(r) in Figure 12.10(a)–(c). Interestingly, it was not true as shown in Figure 12.10(d) when δTCIMF(r) was implemented with D = [blackbrush, creosote leaves, sagebrush] and U = [dry grass, red soil] where it performed significantly better than ![]() .
.
Figure 12.7 Detection results of δCEM(r) and ![]() with dry grass and red soil annihilated by
with dry grass and red soil annihilated by ![]() .
.

Table 12.3 Comparison of detected abundance fractions between δCEM(r) and ![]() with dry grass and red soil annihilated by
with dry grass and red soil annihilated by ![]()

Figure 12.8 Detection results of δCEM(r) and ![]() with drygrass, redsoil, and sagebrush annihilated by
with drygrass, redsoil, and sagebrush annihilated by ![]() .
.
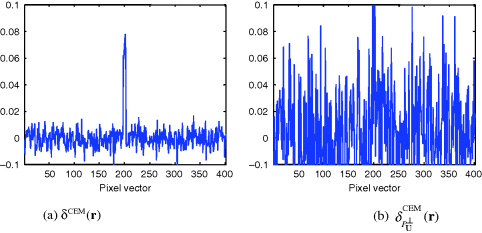
Figure 12.9 Detection results of δOSP(r), ![]() , δCEM(r), and
, δCEM(r), and ![]() with dry grass, red soil, and sagebrush annihilated by
with dry grass, red soil, and sagebrush annihilated by ![]() .
.
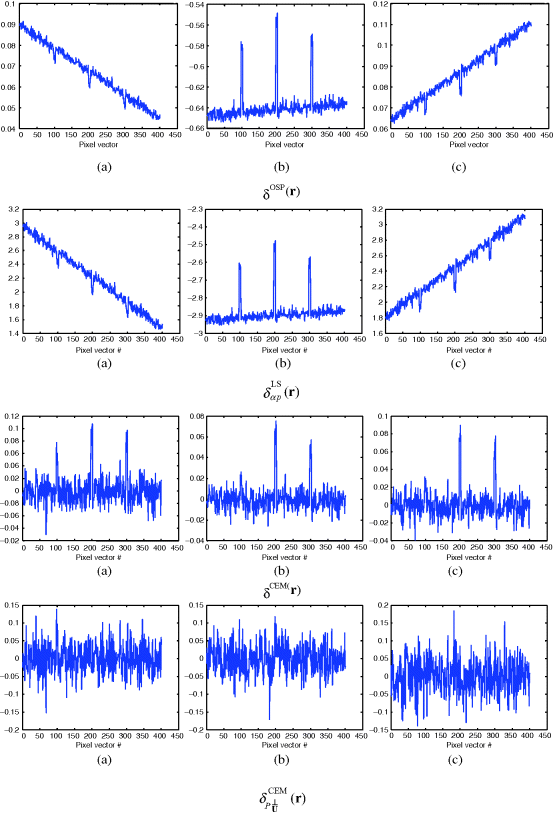
Table 12.4 Comparison of detected abundance fractions by δOSP(r), ![]() , δCEM(r), and
, δCEM(r), and ![]() with
with ![]() -annihilation.
-annihilation.
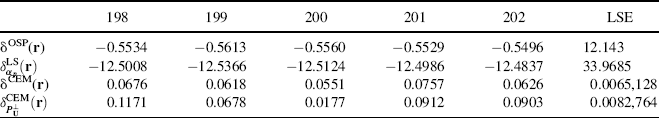
Figure 12.10 Detection results of δTCIMF(r) with D = [blackbrush (B), creosote leaves (C), sagebrush (S)].



