 Exporting HTTP objects
by Charit Mishra, Yoram Orzach, James H Baxter
Wireshark Revealed: Essential Skills for IT Professionals
Exporting HTTP objects
by Charit Mishra, Yoram Orzach, James H Baxter
Wireshark Revealed: Essential Skills for IT Professionals
- Wireshark Revealed: Essential Skills for IT Professionals
- Table of Contents
- Wireshark Revealed: Essential Skills for IT Professionals
- Credits
- Preface
- 1. Module 1
- 1. Getting Acquainted with Wireshark
- 2. Networking for Packet Analysts
- The OSI model – why it matters
- IP networks and subnets
- Switching and routing packets
- WAN links
- Wireless networking
- Summary
- 3. Capturing All the Right Packets
- Picking the best capture point
- Test Access Ports and switch port mirroring
- Capturing interfaces, filters, and options
- Verifying a good capture
- Saving the bulk capture file
- Isolating conversations of interest
- Using the Conversations window
- Wireshark display filters
- Filter Expression Buttons
- Following TCP/UDP/SSL streams
- Marking and ignoring packets
- Saving the filtered traffic
- Summary
- 4. Configuring Wireshark
- 5. Network Protocols
- The OSI and DARPA reference models
- Transport layer protocols
- Application layer protocols
- Summary
- 6. Troubleshooting and Performance Analysis
- Troubleshooting methodology
- Troubleshooting connectivity issues
- Troubleshooting functional issues
- Performance analysis methodology
- Top five reasons for poor application performance
- Summary
- 7. Packet Analysis for Security Tasks
- 8. Command-line and Other Utilities
- 2. Module 2
- 1. Introducing Wireshark
- 2. Using Capture Filters
- 3. Using Display Filters
- 4. Using Basic Statistics Tools
- Introduction
- Using the Summary tool from the Statistics menu
- Using the Protocol Hierarchy tool from the Statistics menu
- Using the Conversations tool from the Statistics menu
- Using the Endpoints tool from the Statistics menu
- Using the HTTP tool from the Statistics menu
- Configuring Flow Graph for viewing TCP flows
- Creating IP-based statistics
- 5. Using Advanced Statistics Tools
- Introduction
- Configuring IO Graphs with filters for measuring network performance issues
- Throughput measurements with IO Graph
- Advanced IO Graph configurations with advanced Y-Axis parameters
- Getting information through TCP stream graphs – the Time-Sequence (Stevens) window
- Getting information through TCP stream graphs – the Time-Sequence (tcp-trace) window
- Getting information through TCP stream graphs – the Throughput Graph window
- Getting information through TCP stream graphs – the Round Trip Time window
- Getting information through TCP stream graphs – the Window Scaling Graph window
- 6. Using the Expert Infos Window
- 7. Ethernet, LAN Switching, and Wireless LAN
- 8. ARP and IP Analysis
- 9. UDP/TCP Analysis
- Introduction
- Configuring TCP and UDP preferences for troubleshooting
- TCP connection problems
- TCP retransmission – where do they come from and why
- Duplicate ACKs and fast retransmissions
- TCP out-of-order packet events
- TCP Zero Window, Window Full, Window Change, and other Window indicators
- TCP resets and why they happen
- 10. HTTP and DNS
- 11. Analyzing Enterprise Applications' Behavior
- Introduction
- Finding out what is running over your network
- Analyzing FTP problems
- Analyzing e-mail traffic and troubleshooting e-mail problems – POP, IMAP, and SMTP
- Analyzing MS-TS and Citrix communications problems
- Analyzing problems in the NetBIOS protocols
- Analyzing database traffic and common problems
- 12. SIP, Multimedia, and IP Telephony
- Introduction
- Using Wireshark's features for telephony and multimedia analysis
- Analyzing SIP connectivity
- Analyzing RTP/RTCP connectivity
- Troubleshooting scenarios for video and surveillance applications
- Troubleshooting scenarios for IPTV applications
- Troubleshooting scenarios for video conferencing applications
- Troubleshooting RTSP
- 13. Troubleshooting Bandwidth and Delay Problems
- 14. Understanding Network Security
- A. Links, Tools, and Reading
- 3. Module 3
- 1. Welcome to the World of Packet Analysis with Wireshark
- 2. Filtering Our Way in Wireshark
- 3. Mastering the Advanced Features of Wireshark
- 4. Inspecting Application Layer Protocols
- 5. Analyzing Transport Layer Protocols
- 6. Analyzing Traffic in Thin Air
- 7. Network Security Analysis
- 8. Troubleshooting
- 9. Introduction to Wireshark v2
- Bibliography
- Index
Exporting HTTP objects is a simple feature for exporting HTTP statistics—websites and files accessed by HTTP.
To export HTTP objects, follow these steps:
- You can use this feature when capture is running, or you can save the captured file. You will get the following window:
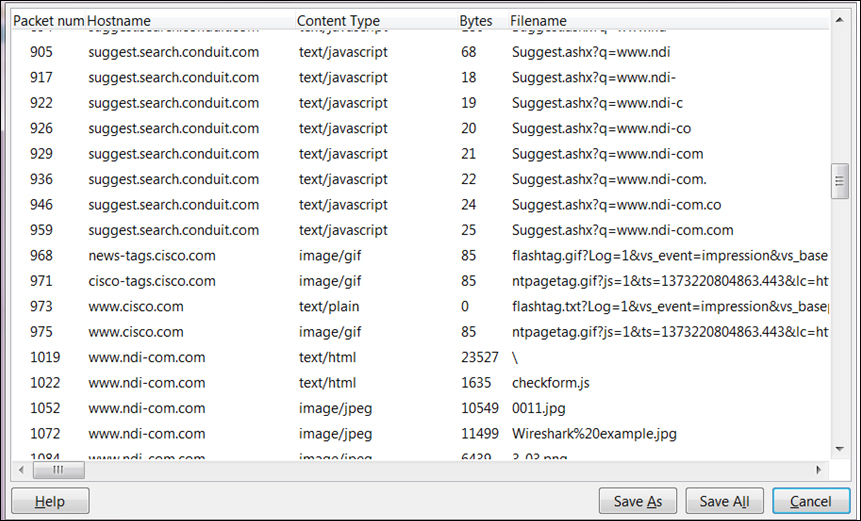
- From here you can get a list of the websites that were accessed, including the files that were accessed in each one of them. You can see the website, file types, size, and names.
- You can use the Save As or Save All buttons for saving the data in a file.
- In the Content Type column, you will see the following contents:
- Text: text/plain, text/html, text/javascript—if it's a JavaScript, check what it is, it might be a security risk
- Images: image/jpeg, image/gif, and other types of images—you can open it with a viewer
- Applications: application/json, application/javascript, and other types of applications
- Any other text file discovered by Wireshark
You will get a directory with all the objects captured in the capture file. Objects can be pictures (for example, packet 1052 and 1057 in the preceding screenshot), text (packets 1019, 1022, and others in the preceding screenshot), and others.
This feature scans HTTP streams in the currently opened capture file or the running capture, takes reassembled objects such as HTML documents, image files, executable files, and other readable formats, and lets you save them to a disk. The saved objects can then be opened with the proper viewer, or they can be executed in the case of executable files just by clicking on them. This feature can be helpful for various purposes, including eavesdropping and saving objects for backup (for example, files that were sent through e-mails).
You have several pieces of software that perform the same things graphically, some of them are as follows:
- Xplico (http://www.xplico.org/)
- NetworkMiner (http://www.netresec.com/?page=NetworkMiner)
Tip
When you see an unknown website with an application that you don't know, and a filename that looks suspicious—Google it; it might be a risk (we will get back to this in Chapter 14, Understanding Network Security).
-
No Comment