Denial of Service (DoS) and Distributed Denial of Service (DDoS) are attacks that intend to deny users from accessing network services. Services that can be denied to users can be:
DoS/DDoS attacks can be a result of scanning that we talked about in the previous recipe. The difference is that DoS/DDoS is a scan that slows down a server or a network in a way that denies user access.
In this recipe, we will see some common DoS/DDoS patterns, and learn how to identify and block them.
DoS/DDoS are usually discovered when one of the network resources, that is, communications lines or servers becomes very slow and is also not functioning.
When you identify such a resource, connect Wireshark with port mirror to this device and start packet capture. In this recipe, we will go through some common DoS/DDoS attacks and their signatures.
Connect Wireshark to the network with port mirror to the port of the resource that you suspect is exposed to DoS/DDoS. Usually, it will be a server that becomes very slow, a communication line that becomes very loaded, or any other resource that stops functioning or becomes very slow.
- When a communication line becomes very slow, for example, a connection to the Internet, connect Wireshark with port mirror to this line.
- Try to locate where the traffic comes from.
- I've port mirrored the server, and this is what I got:
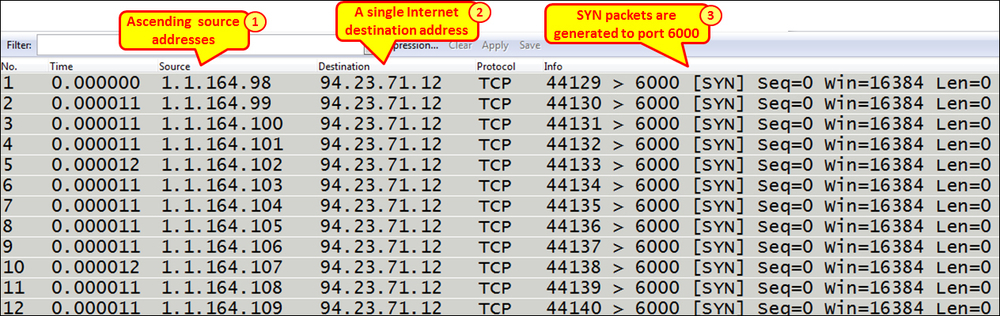
- We see source addresses in the ascending order, generating traffic to the Internet address 94.23.71.12.
- Since the source addresses are unknown, I've checked their MAC address. What I got was:
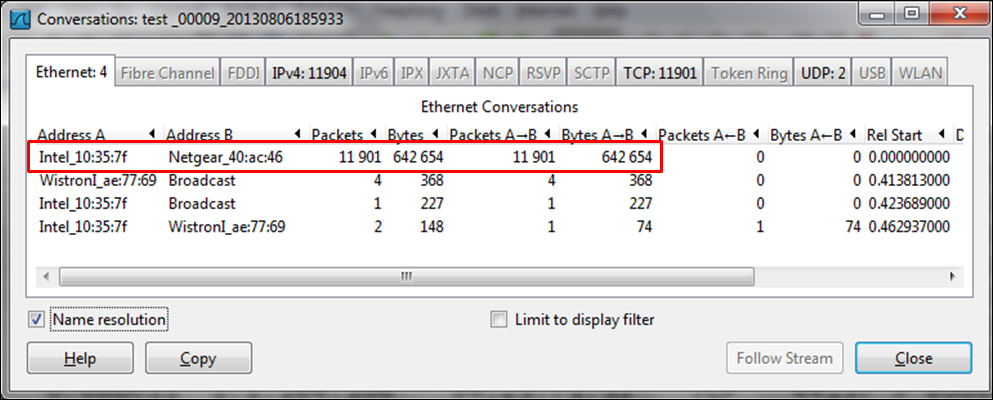
- The problem was that all source addresses came from a single MAC address; so I checked their MAC addresses, and all IP addresses came from a single MAC address, the MAC address of the server.
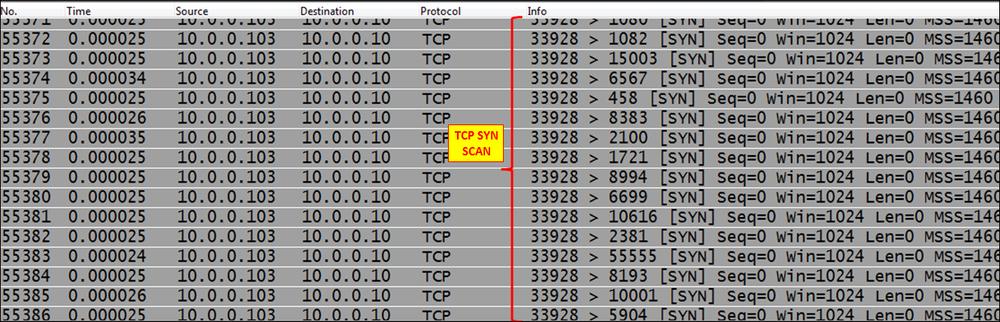
- Another example can be a simple SYN scan that comes from a single attacker, as seen in the next illustration. Look for SYN and watch the port numbers that they are scanning. You might see:
- No response
- Reset packet
- SYN-ACK response
- There can be various consequences to this type of attack:
- In case of no response or reset response, the attacked server is functioning well. In case the server answers with a SYN-ACK response, it might be a risk to the server.
- The risk is that if too many connections will be opened (SYN/SYN-ACK/ACK) or half opened (SYN/SYN-ACK), the server might get slow due to these connections.
- You can see a typical TCP SYN attack in the following illustration. A SYN attack becomes DoS/DDoS when it blocks a communication line or loads a server to the point that it stops functioning.
Denial of Service is an attack that denies the use of a network service. The way to do this is by causing the device under attack to allocate hardware resources (CPU, memory, and so on) to the attacker so that nothing is left for the users.
Denial of Service is when there is an attack on a network resource. Distributed DoS is when the attack is coming from multiple sources.
DoS/DDoS attacks are sometimes hard to discover since they can simulate a real situation. For example:
- Ping scans that can also come for management systems.
- HTTP GET requests that are the normal requests that are accepted by web servers.
- SNMP GET requests.
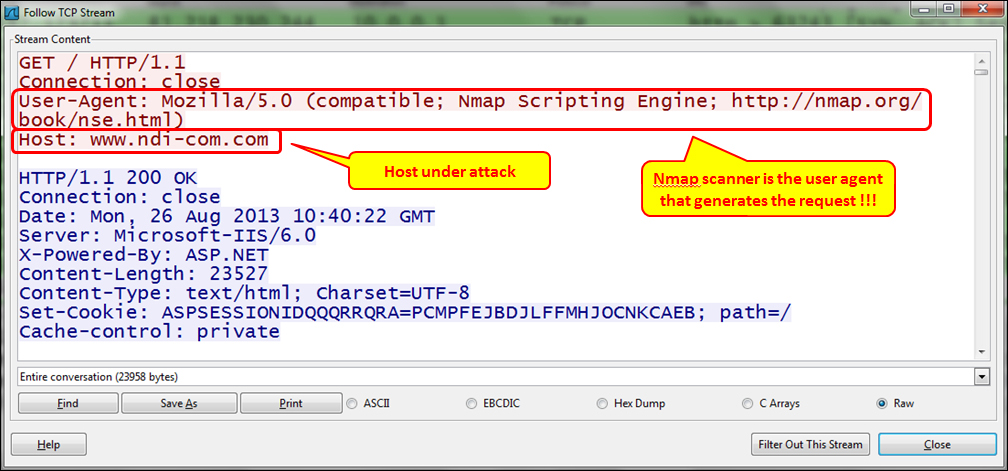
These and many others should be monitored for their quantity and sources in order to discover a problem. In the following screenshot, we see what we get when we follow a specific TCP stream.