We already covered custom alert actions in detail in Chapter 9, Advanced Dashboard Customization. In this section, you will learn what new features have been introduced in the Splunk 6.4 release.
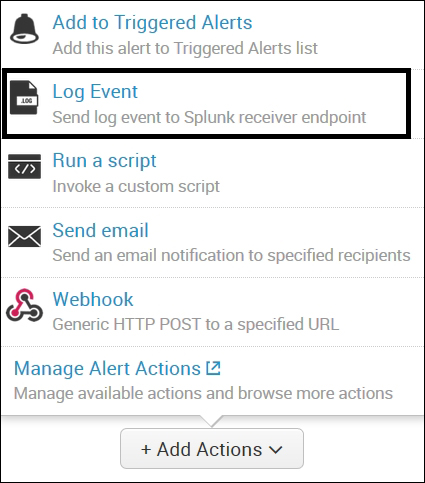
Splunk 6.4 has a new feature to choose from the action list of alert actions, that is, it sends log events to the Splunk receiver endpoint. In the following figure, the option marked in the rectangular box is the newly added feature in Splunk 6.4 under alert actions.
This option helps users to redirect the alert log data to Splunk again under the specified sourcetype or index. The alert that used to either trigger e-mails, webhook, or any other defined custom action can also be sent on Splunk for analysis in future. This feature can be helpful for auditing alert scenarios.
Let's understand the use of this Log Event feature in a custom alert. Suppose we have an alert defined to detect fraudulent transactions. Whenever such a transaction is detected, there is a support ticket lodged in JIRA and a custom script runs, which instructs the payment gateway to trigger another layer of authentication. Now, the alert data can be sent on Splunk under different sourcetypes, which can be used to determine and derive various insights relevant to the fraudulent transaction. This would enable us to restrict such activity in the future.
Thus, the Log Event option can be used in various scenarios as per the requirement under the custom alert action.
