PowerShell Direct is a new feature that allows you to use PowerShell directly from a Windows 10 or Windows Server 2016 Hyper-V host and virtual-machine guest operating system (specifically, Windows 10 and Windows Server 2016) without having any network configuration or any type of network at all; you don't even need to have a virtual NIC attached to your virtual machine or configure WinRM. You can just use PowerShell directly on your virtual machine from your Hyper-V host operating system.
By leveraging the VMBus architecture of Hyper-V, we are literally bypassing all the requirements for networking, firewall, remote management, and access settings. It's a great feature.
PowerShell Direct requires an account to be a member of the Hyper-V Administrator group on the host side because, if you want to have access to your virtual machines in the first place, you need to be a Hyper-V admin; if you are able to run Get-VM on the host, you can use PowerShell Direct very simply. However, on the guest operating side, you can use any credentials that are available on the guest OS but, obviously, you will have the correct limitation for those credentials, so you can run as Administrator or as a standard user based on what you need to do.
PowerShell Direct does not require PowerShell Remoting in any way, shape, or form. You can even stop the WinRM service on the host and on the guest OS. PowerShell Direct will just work. Automation is key for businesses and IT professionals: the time you spend on building, deploying and managing your virtual machines is drastically reduced, and you can achieve more while you carry out other tasks as well.
These tasks will show you how to use the PowerShell Direct feature to manage your virtual machines remotely using PowerShell.
Open a PowerShell window as an administrator from the machine for which you want to use PowerShell Direct, and type the following:
Enter-PSSession –VMName VMName -Credential (Get-Credential) Invoke-Command –VMName VMName -Credential (Get-Credential) –ScriptBlock { Commands } $S = New-PSSession -VMName VMName -Credential (Get-Credential)
You can use either Enter-PSSession or Invoke-Command or New-PSSession but instead of specifying the computer name, you can specify the virtual machine using two parameters –VMName or –VMGuid or -VMId as shown in the following screenshot:
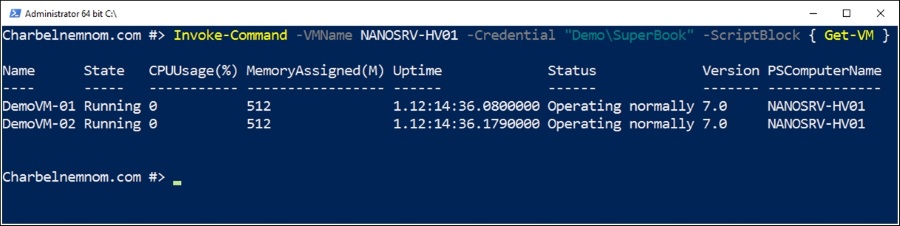
Just by using a single line of PowerShell, you can update, change, or configure the guest OS instantly.
The following example will set the time zone for all virtual machines on a particular Hyper-V host without any network connection:
Invoke-Command -VMName (Get-VM).Name -Credential ~Administrator -ScriptBlock {Tzutil /s "Romance Standard Time"}
It's as easy as imagining what scenario you would like to accomplish and you can get it done in couple of seconds.
The process to use a PowerShell Direct session in virtual machines involves the following:
- The virtual machine must be running locally on the host and booted
- You must be logged into the host computer as a Hyper-V administrator
- You must supply valid user credentials for the virtual machine
What about disabling PowerShell Direct on a virtual machine?
Well, the scenarios where you might want to disable PS Direct are if the administrator who manages the virtual machine is not the same who manages the fabric, or in a hosting environment where the tenant wants to block PowerShell Direct, but as I mentioned earlier in this section, you need to have guest credentials in order to use PowerShell Direct.
Please note that you can protect a virtual machine from PowerShell Direct by disabling the Hyper-V VM Session Service inside it.
The service that leverages PowerShell Direct is highlighted in yellow in the following screenshot:
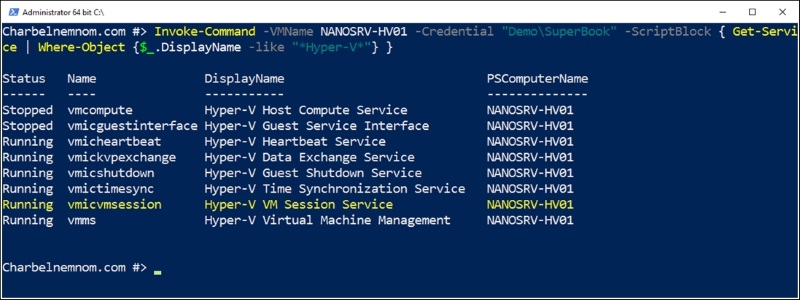
Please note that it is not enough to disable and stop the service inside the virtual machine because the service is set to Manual Trigger, so if you stop the service and try to use PowerShell Direct, the service will start again. After disabling and stopping the service, you need to restart the guest OS in order to disable PowerShell Direct completely.
By disabling and stopping the Hyper-V VM Session Service, no one can access the virtual machine using PowerShell Direct even if the user credentials are compromised.
What about shielded virtual machines? Please check Chapter 6, Security and Delegation of Control for more information. PowerShell Direct is disabled by default on shielded virtual machines.
Just Enough Administration (JEA) is a PowerShell security technology that allows you to configure different levels of access, by taking a role-based access-control (RBAC) approach, for any Hyper-V task that can be managed with the use of PowerShell and/or PowerShell Direct. The reason behind this new capability is to bring PowerShell Direct into cloud environments, because if you want to use PowerShell Direct, you need to have valid credentials both on the host and in the virtual machine, so in hosting environments, you cannot, for security reasons, give full access to the host to connect to the tenant virtual machine. So, instead of disabling PowerShell Direct as described in the previous section, Microsoft enabled JEA to support PowerShell Direct for Hyper-V, where a tenant can now choose to provide limited access to their service provider (host) using the JEA platform.
- The Delegation control in Hyper-V recipe in Chapter 6, Security and Delegation of Control.
