Hyper-V Replica brings you all that you need to build your Infrastructure as a Service (IaaS) and also provides you with a Disaster Recovery environment for virtualized workloads.
With its simple configuration and a couple of clicks, you can start replicating your virtual machine to a different site with low cost and high reliability. However, the out-of-box experience using HTTP to replicate data does not provide encryption during the transfer to the other site.
This recipe will show you how to use an Enterprise Certification Authority (CA) to obtain a certificate to replicate the virtual machine data using HTTPS.
In order to request a digital certificate, you will need to have an Enterprise CA already installed and configured. Use the Server Manager to install Active Directory Certificate Services and then to configure an Enterprise CA in case you don't have one.
You can also use PowerShell to install Active Directory Certificate Services by running the following command:
Install-WindowsFeature -Name ADCS-Cert-Authority -IncludeAllSubFeature -IncludeManagementTools -Verbose
The following steps will show how to create a certificate template in the Enterprise CA, how to request and install a certificate to be used on Hyper-V Replica and how to enable Hyper-V Replica to use certificate-based authentication for replication.
- To create a certificate template to be used to issue certificates for Hyper-V, type
certsrv.mscfrom your CA server, to open the Certification Authority console. - Expand your local CA (make a note of the CA name, you will need it during step 16), right-click on Certificate Templates, and select Manage.
- In the Certificate Templates Console, right-click on the Computer template and select Duplicate Template, as shown in the following screenshot.
- In the Properties of New Template pane, go to the General tab and fill in the Template display name and the Template name fields. In the following screenshot,
Hyper-V Replica Templatewas added as the Template name and Publish certificate in Active Directory was selected.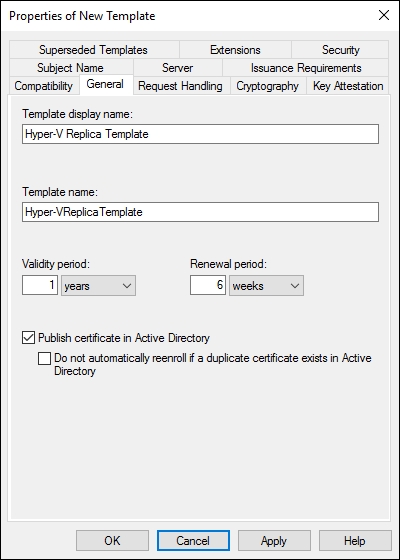
- Click on the Security tab, select the Authenticated Users group and allow the Enroll permission, as shown in the following screenshot:
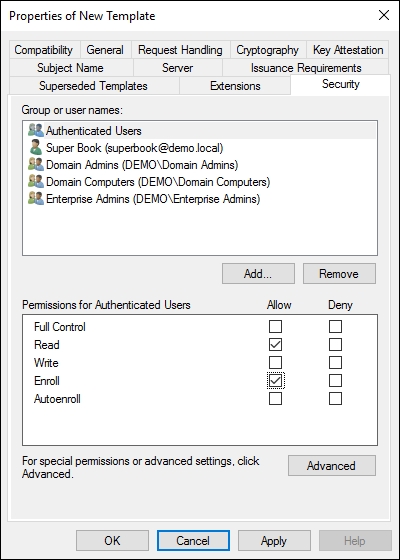
- Click on the Subject Name tab and select Build from this Active Directory information and under Subject name format, select DNS name as shown in the following screenshot to enable the DNS name to be added during the request in a later step. Click on OK to confirm the new certificate template creation and close the Certificate Templates Console window.

- Back in the Certification Authority console, right-click on Certificate Templates, navigate to New, and click on Certificate Template to Issue as shown in the following screenshot.
- In the Enable Certificate Templates window, select the new certificate template (Hyper-V Replica Template), and click on OK.
- From your remote management machine, open PowerShell ISE and use the following script as an example code to request your certificate. Replace the HVHost and DnsName values with your server's Fully Qualified Domain Name (FQDN).
- To automate the certificate creation process, in the following example, the Credential Security Service Provider (CredSSP) protocol was used to request a certificate from the local Enterprise CA using PowerShell Remoting. The long story short is that CredSSP allows us to delegate user credentials manually across the network. Obviously, this is a security-sensitive operation and should be implemented carefully.
# Run this script on a domain member machine # Enter your target Hyper-V Host (FQDN) $HVHost='HVHost01.demo.local','HVHost02.demo.local','HVHost03.demo.local' $Credentials=Get-Credential-Credential"DemoAdmin" Enable-PSRemoting-Force Enable-WSManCredSSP-RoleClient-DelegateComputer"*.demo.local"-Force restart-Servicewinrm Invoke-Command-computername$HVHost-ScriptBlock { Enable-PSRemoting-Force Enable-WSManCredSSP-RoleServer-Force Set-ItemWSMan:localhostClientTrustedHosts-value"*.demo.local"-Force restart-Servicewinrm } # Request a new certificate from each Hyper-V host that will be used as a member of Hyper-V Replica Invoke-Command-computername$HVHost-ScriptBlock { Get-Certificate-TemplateHyper-VReplicaTemplate-Urlldap:///CN=Ent-Root-CA-CertStoreLocationCert:LocalMachineMy-DnsNameHVHost01.Demo.Local-Verbose } -Credential$Credentials-AuthenticationCredssp # Reset the CredSSP environment to the way it was originally Disable-WSManCredSSP–RoleClient Invoke-Command–ComputerName$HVHost–ScriptBlock { Disable-WSManCredSSP–RoleServer } - After running above script, the certificate will be automatically created and installed on each Hyper-V host under Personal | Certificates as shown in the following screenshot. At the end of this script, we will reset the CredSSP environment to the way it originally was.
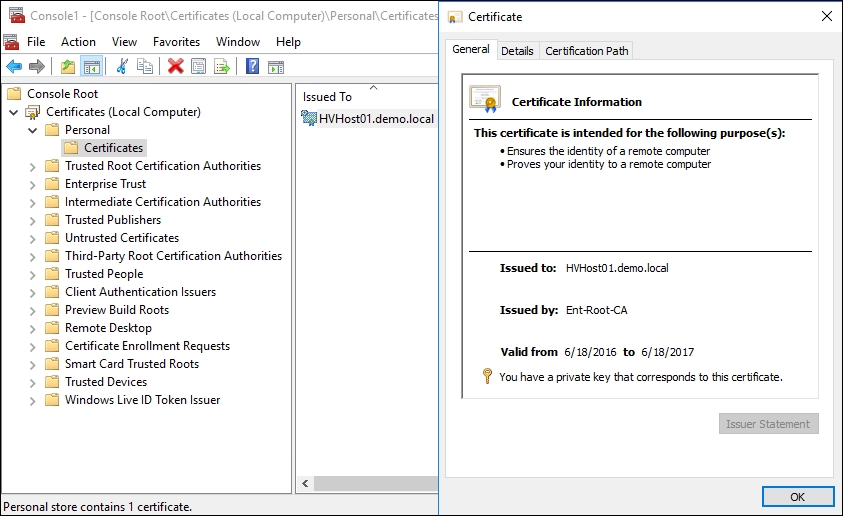
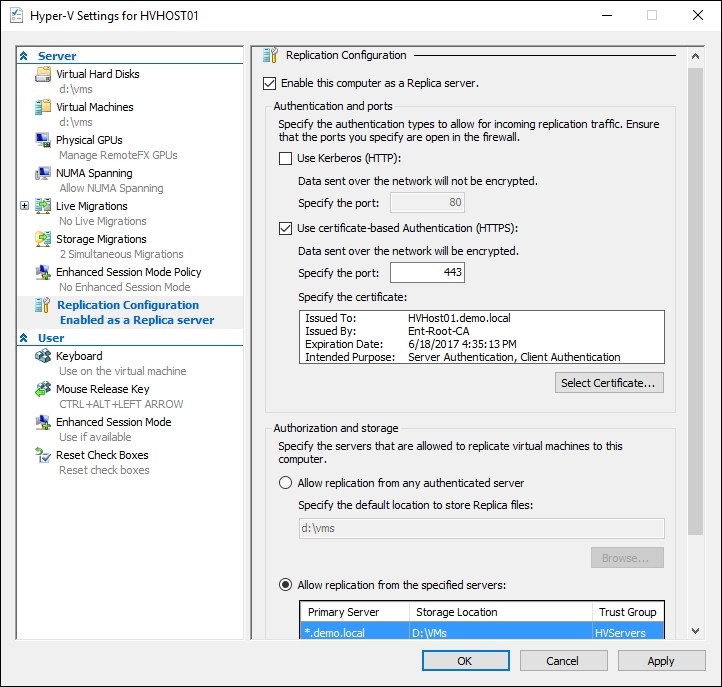
- Now with the certificate installed on each Hyper-V host, open the Hyper-V Manager, click on Hyper-V Settings on the pane on the right-hand side, and check the Enable this computer as a Replica server option.
- Check the Use certificate-based Authentication (HTTPS) option and click on Select Certificate.
- In the Windows Security window, confirm the imported certificate and click on OK, as shown in the next screenshot:
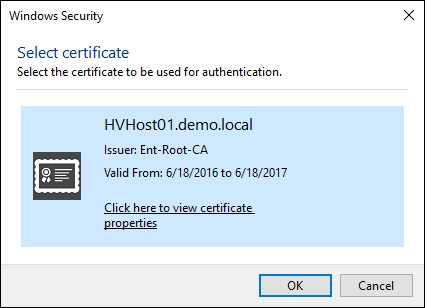
- Verify the certificate settings, as shown in the following screenshot and click on OK.
- Ensure the inbound TCP exception for port '443' is enabled in the firewall on every host that will be used as a member of the Hyper-V Replica. If you are using Windows Firewall, enable "Hyper-V Replica HTTPS Listener (TCP-In)" rule.
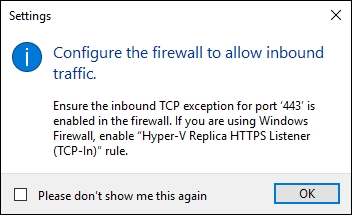
- To enable Hyper-V Replica in the local Windows Firewall, open PowerShell console and type the following command one very host:
Invoke-Command-computername$HVHost-ScriptBlock{Enable-Netfirewallrule-displayname"Hyper-V Replica HTTPS Listener (TCP-In)"} - Please make sure that you enabled Port 443 and installed the certificate on the other Hyper-V Servers otherwise the replication will fail. The example in this script will enable Windows Firewall and install the certificate on the three Hyper-V hosts simultaneously.
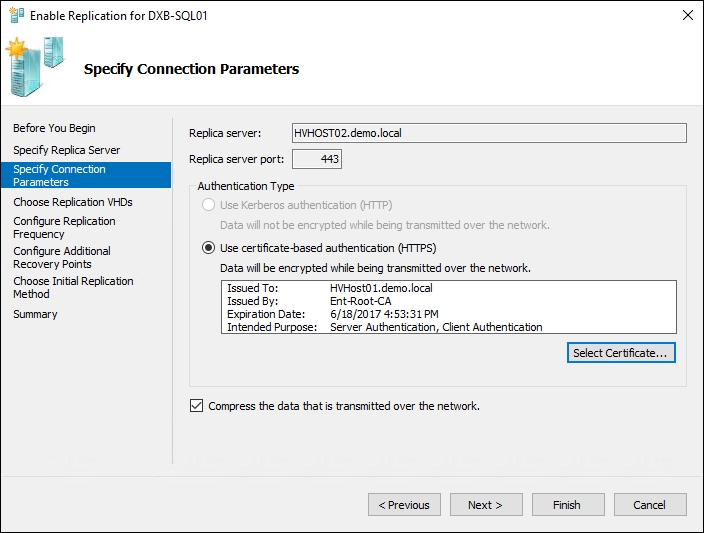
- When enabling the replica for a virtual machine, under Specify Connection Parameters, select Use certificate-based authentication (HTTPS), as shown in the next screenshot, click on Select Certificate and click OK.
In this recipe, a template was created with the necessary advanced options required for Hyper-V Replica configuration.
After template creation, we requested for a new certificate from the CA server that must be used to validate and authenticate each host.
When the certificate is issued and installed on all Hyper-V servers that will be used to configure Hyper-V Replica, you can enable it by using certificate-based authentication and replicate the virtual machines between them.
A digital certificate is one of the most common and safest methods used today by applications, websites, and many other solutions to provide communication authenticity and encryption.
Hyper-V Replica can use this technology to encrypt and protect replication data. In this recipe, an Enterprise CA was used as an example for internal certificate requests. Although Enterprise CAs are more common internally, you can also use standalone or even external CAs to create requests for your certificates.
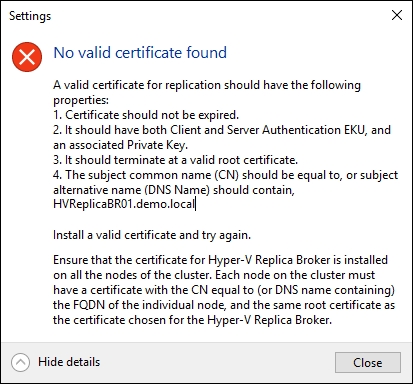
Now, for the Hyper-V cluster, the certificate needs to have the FQDN of the Replica Broker name in the Common Name field or in the Subject Alternative Name field as shown in the following screenshot:

The Replica Broker certificate must be exported with its private key and imported on all the cluster nodes.
In addition to the certificate for Hyper-V Replica Broker, each node of the cluster must also have a computer authentication certificate that can be validated to the same CA root certificate as the certificate for Hyper-V Replica Broker.
In summary, every Hyper-V host must have a computer certificate and the cluster nodes also must have the Replica Broker certificate. If only one of the two certificates are missing from one of the cluster nodes, you will get the following error.
By using an Enterprise CA, you have some benefits such as Active Directory integration, auto enrolment of certificates, and certificate templates.
