Roles are the permissions given to users within a project. Roles can also be scoped to a particular domain, making it possible to restrict permissions for particular users to a domain and project. If you used Ansible to install your OpenStack environment, it should already contain some default roles, such as admin and _member_. Here we will configure one role, a cloud_admin role that allows for administration of our example bookstore domain environment and a user role for the default domain that is given to ordinary users who will be using the cloud environment.
Ensure that you are logged on to a correctly configured OpenStack client and can access the OpenStack environment as a user with admin privileges.
Refer to Chapter 2, The OpenStack Client, for details of setting up your environment to use OpenStack command-line client.
To create the required roles in our OpenStack environment, perform the following steps:
- Creation of the
cloud_adminrole is done as follows:openstack role create --domain bookstore cloud_admin:
- To configure the
userrole for thedefaultdomain, execute the following command:openstack role create user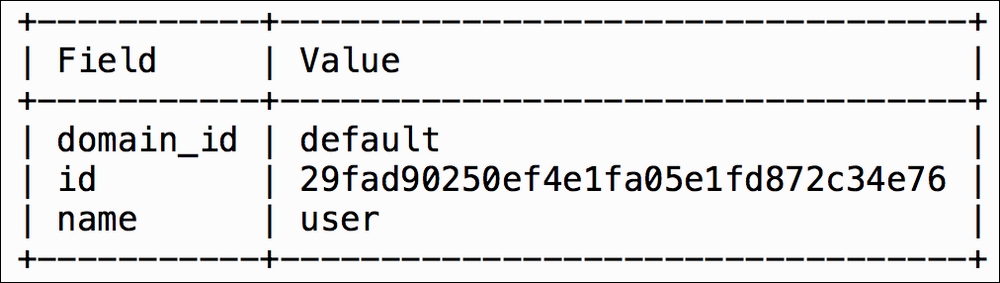
This command created a new role called
user. Since we didn't specify a domain, it was created under thedefaultdomain. - View roles associated with the
bookstoredomain:openstack role list --domain bookstore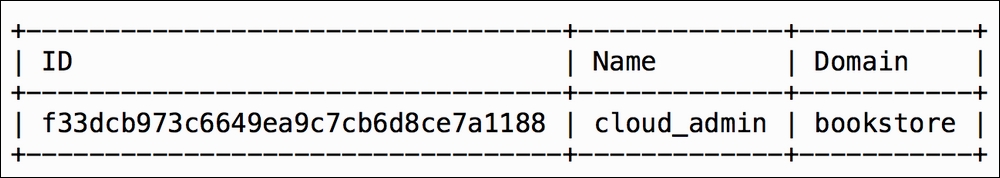
- List roles associated with the current admin user:
openstack role list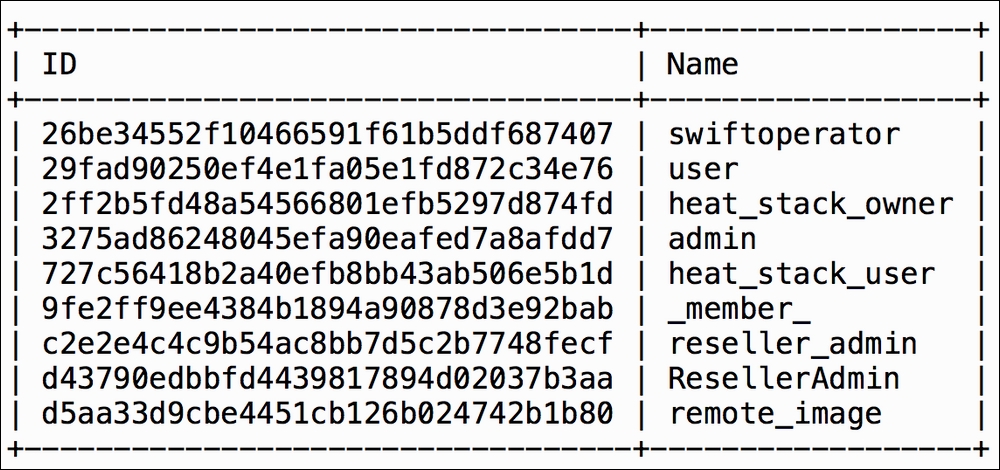
Creation of roles is simply achieved using the OpenStack client, specifying the role create option with the following syntax:
openstack role create --domain <domain_name> <role_name>
The domain_name attribute is optional, if you omit it, a role for the default domain will be created.
For the role_name attribute, the admin and _member_ roles names cannot be used again. The admin role is set by default in OpenStack code starting with the Pike release, and in releases before Pike in the /etc/keystone/policy.json file, as having administrative rights:
{
"admin_required": "role:admin or is_admin:1",
}The _member_ role is also configured by default in the dashboard when a nonadmin user is created through the web interface.
On creation of the role, the ID associated with the role is returned, and we can use it when assigning roles to users. To see a list of roles and the associated IDs in our environment, we can issue the following command:
openstack role list --domain <domain_name>
