Common Prevention Methods
A great many of the security issues that plague networks today can be solved through the implementation of basic security elements. Some of those elements are physical (locked doors) and others digital (antivirus software), but all share in common the goal of keeping the problems out.
Four topic areas are key: physical security, digital security, user education, and the principle of least privilege. As you study for the exam, know what types of physical security elements you can add to an environment to secure it. Know, as well, what types of digital security you should implement to keep malware at bay. Understand that the first line of defense is the users. You need to educate them to understand why security is important, and you need to impose the principle of least privilege to prevent them from inadvertently causing harm.
Physical Security
Physical security is a grab bag of elements that can be added to an environment to aid in securing it. It ranges from key fobs to retinal scanners. In the following sections, we will examine the list of components in the order in which they are listed by CompTIA.
Lock Doors
One of the easiest ways to prevent those intent on creating problems from physically entering your environment is to lock your doors and keep them out. A key aspect of access control involves physical barriers. The objective of a physical barrier is to prevent access to computers and network systems. The most effective physical barrier implementations require that more than one physical barrier be crossed to gain access. This type of approach is called a multiple barrier system.
Ideally, your systems should have a minimum of three physical barriers. The first barrier is the external entrance to the building, referred to as a perimeter, which is protected by burglar alarms, external walls, fencing, surveillance, and so on. An access list should exist to specifically identify who can enter and can be verified by a guard or someone with authority. The second barrier is the entrance into the building, and it could rely upon such items as ID badges to gain access. The third barrier is the entrance to the computer room itself (and could require key fobs, or just keys to locks). Each of these entrances can be individually secured, monitored, and protected with alarm systems.

Although these three barriers won’t always stop intruders, they will potentially slow them down enough that law enforcement can respond before an intrusion is fully developed. Inside, a truly secure site should be dependent upon a physical security token for access to the actual network resources.
Tailgating
Tailgating refers to being so close to someone when they enter a building that you are able to come in right behind them without needing to use a key, a card, or any other security device. Many social engineering intruders needing physical access to a site will use this method of gaining entry. Educate users to beware of this and other social engineering ploys and prevent them from happening.

Securing Physical Documents/Passwords/Shredding
It is amazing the information that can be gleaned from physical documents even in the age when there is such a push to go paperless. Dumpster diving is a common problem that puts systems at risk. Companies normally generate a huge amount of paper, most of which eventually winds up in dumpsters or recycle bins. Dumpsters may contain information that is highly sensitive in nature (such as a password a user has written on a piece of paper because they haven’t memorized it yet). In high-security and government environments, sensitive papers should be either shredded or burned. Most businesses don’t do this. In addition, the advent of “green” companies has created an increase in the amount of recycled paper, which can often contain all kinds of juicy information about a company and its individual employees.
Biometrics
Biometric devices use physical characteristics to identify the user. Such devices are becoming more common in the business environment. Biometric systems include fingerprint/palm/hand scanners, retinal scanners, and soon, possibly, DNA scanners. To gain access to resources, you must pass a physical screening process. In the case of a hand scanner, this may include identifying fingerprints, scars, and markings on your hand. Retinal scanners compare your eye’s retinal pattern to a stored retinal pattern to verify your identity. DNA scanners will examine a unique portion of your DNA structure to verify that you are who you say you are.
With the passing of time, the definition of biometrics is expanding from simply identifying physical attributes about a person to being able to describe patterns in their behavior. Recent advances have been made in the ability to authenticate someone based on the key pattern they use when entering their password (how long they pause between each key, the amount of time each key is held down, and so forth). A company adopting biometric technologies needs to consider the controversy they may face (some authentication methods are considered more intrusive than others). The error rate also needs to be considered and an acceptance of the fact that errors can include both false positives and false negatives.
Badges
Badges can be any form of identification intended to differentiate the holder from everyone else. This can be as simple as a name badge or photo ID.
Smart cards are difficult to counterfeit, but they’re easy to steal. Once a thief has a smart card, they have all the access the card allows. To prevent this, many organizations don’t put any identifying marks on their smart cards, making it harder for someone to utilize them. A password or PIN is required to activate many modern smart cards, and encryption is employed to protect the card’s contents.
Key Fobs
Key fobs are named after the chains that used to hold pocket watches to clothes. They are security devices that you carry with you; they display a randomly generated code that you can then use for authentication. This code usually changes very quickly (every 60 seconds is probably the average), and you combine this code with your PIN for authentication. RSA is one of the most well-known vendors of these.
RFID Badges
A smart card is a type of badge or card that gives you access to resources, including buildings, parking lots, and computers. It contains information about your identity and access privileges. Each area or computer has a card scanner or a reader in which you insert your card. RFID (Radio Frequency Identification) is the wireless, no-contact technology used with these cards and their accompanying reader.
The reader is connected to the workstation and validates against the security system. This increases the security of the authentication process because you must be in physical possession of the smart card to use the resources. Of course, if the card is lost or stolen, the person who finds the card can access the resources it allows.
RSA Tokens
Physical tokens are anything that a user must have on them to access network resources and are often associated with devices that enable the user to generate a one-time password authenticating their identity. SecurID, from RSA, is one of the best-known examples of a physical token, and information on it can be found at www.rsa.com/node.aspx?id=1156.
Privacy Filters
Privacy filters are either film or glass add-ons that are placed over a monitor or laptop screen to prevent the data on the screen from being readable when viewed from the sides. Only the user sitting directly in front of the screen is able to read the data.
Retinal
As mentioned earlier, retinal scanners are one form of biometric devices that can be used to identify a user. As the name implies, matches are made based upon identification of the blood vessels in an individual’s retina. Though highly reliable, the equipment needed is still rather expensive.
Digital Security
Whereas the topic of physical security, from CompTIA’s standpoint, focuses on keeping individuals out, digital security focuses on keeping harmful data and malware out as well as on authorization and permissions. The areas of focus are antivirus software, firewalls, antispyware, user authentication/strong passwords, and directory permissions. Each of these are addressed in the sections that follow.
Antivirus Software
The primary method of preventing the propagation of malicious code involves the use of antivirus software. Antivirus software is an application that is installed on a system to protect it and to scan for viruses as well as worms and Trojan horses. Most viruses have characteristics that are common to families of virus. Antivirus software looks for these characteristics, or fingerprints, to identify and neutralize viruses before they impact you.
More than 200,000 known viruses, worms, bombs, and other malware have been defined. New ones are added all the time. Your antivirus software manufacturer will usually work very hard to keep the definition database files current. The definition database file contains the currently known viruses and countermeasures for a particular antivirus software product. You probably won’t receive a virus that hasn’t been seen by one of these companies. If you keep the virus definition database files in your software up-to-date, you probably won’t be overly vulnerable to attacks.

Firewalls
Firewalls are among the first lines of defense in a network. There are different types of firewalls, and they can be either stand-alone systems or included in devices such as routers or servers. You can find firewall solutions that are marketed as hardware only and others that are software only. Many firewalls, however, consist of add-in software that is available for servers or workstations.
The basic purpose of a firewall is to isolate one network from another. Firewalls are becoming available as appliances, meaning they’re installed as the primary device separating two networks. Appliances are freestanding devices that operate in a largely self-contained manner, requiring less maintenance and support than a server-based product.
Firewalls function as one or more of the following:
- Packet filter
- Proxy firewall
- Stateful inspection firewall

The firewall shown in Figure 17-1 effectively limits access from outside networks while allowing inside network users to access outside resources. The firewall in this illustration is also performing proxy functions.
Figure 17-1: A proxy firewall blocking network access from external networks
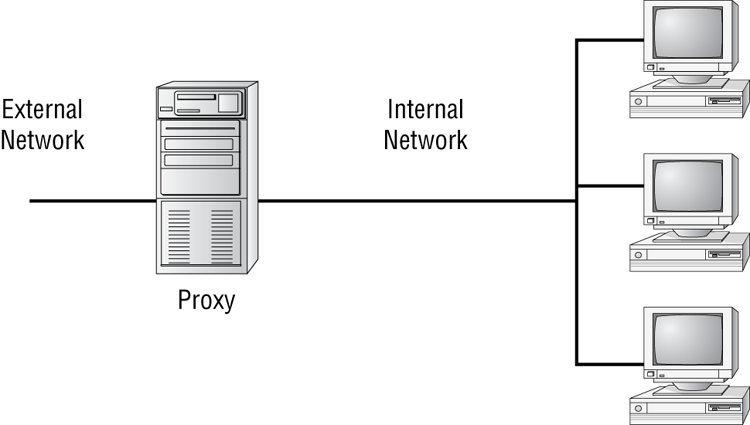

The following list includes discussions of three of the most common functions that firewalls perform:
Figure 17-2: A dual-homed firewall segregating two networks from each other
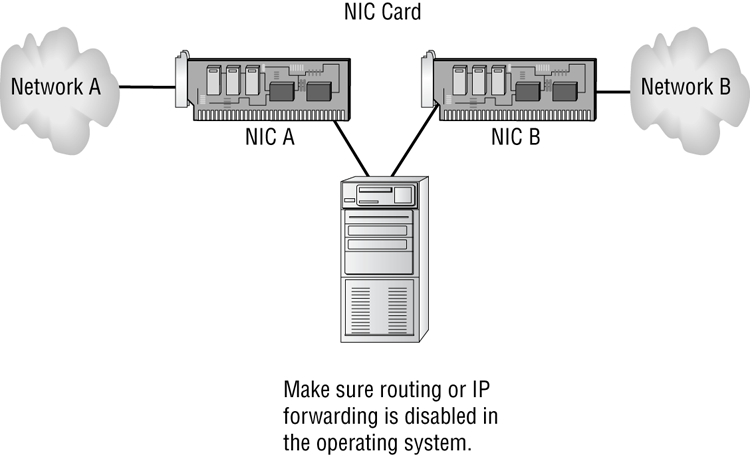
Antispyware
Just as antivirus software seeks out and stops viruses from entering and spreading, so too is the purpose of antispyware software. One thing separating spyware from most other malware is that it almost always exists to provide commercial gain. The operating systems from Microsoft are the ones most affected by spyware, and Microsoft has released Windows Defender and Security Essentials (as well as System Center Endpoint Protection for the enterprise) to combat the problem.
User Authentication/Strong Passwords
You can set up many different parameters and standards to force the people in your organization to conform. In establishing these parameters, it’s important that you consider the capabilities of the people who will be working with them. If you’re working in an environment where people aren’t computer savvy, you may spend a lot of time helping them remember and recover passwords. Many organizations have had to reevaluate their security guidelines after they’ve invested great time and expense to implement high-security systems.
Enforcing authentication security, especially when supporting users, can become a high-maintenance activity for network administrators. On one hand, you want people to be able to authenticate easily; on the other hand, you want to establish security that protects your company’s resources. In a Windows domain, password policies can be configured at the domain level using Group Policy objects. Variables you can configure include password complexity and length and the time between allowed changes to passwords. A good password includes both upper- and lowercase letters as well as numbers and symbols. Educate users to not use personal information that one could easily guess about them, such as their pet names, anniversaries, or birthdays.
Directory Permissions
There is not much users can do to improve or change the security of the directory services deployed. However, you can ensure that they don’t become a tool for an attacker bent on compromising your organization’s security:
- Ensure that the most secure form of authentication encryption is used and supported by both the client and the authentication servers.
- Use encrypted software and protocols whenever possible, even for internal communications.
- Require users to change their password according to the company’s password policy.
- Establish a minimum character limit for passwords. While many companies set the minimum at 8 characters, it is not uncommon to see this set at 16.
- Instruct user to never write their password down, or if they do, divide it up into several pieces and store each in a different secure location (such as a home safe, a gun cabinet, a chemical supply locker, or safety deposit box).
- Tell users to never share their password or logon session with another person; this includes friends, spouse, and children.
- Make sure users allow all approved updates and patches to be installed onto their client.
- Ensure that users copy all company data back to a central file server before disconnecting from a logon session.
- Users should back up any personal data onto verified removable media.
- Users should never walk away from a logged-on workstation without first locking it (requiring a password to continue the session).
- Require users to employ a password-protected screensaver.
- Don’t let users use auto-logon features.
- Tell users to be aware of who is around them (and may be watching them) when they log on and when they work with valuable data.
- Users should never leave a company notebook, cell phone, or PDA in a position where it can be stolen or compromised while they are away from the office. Cable locks should be used to keep notebooks securely in place whenever they are off site.
The protection of a directory service is based on the initial selection of network operating system and its deployment infrastructure. After these foundational decisions are made, you need to fully understand the technologies employed by your selected directory services system and learn how to make the most functional, yet secure, environment possible. This will usually require the addition of third-party security devices, applications, services, and solutions.
User Education
The most effective method of preventing viruses, spyware, and harm to data is education. Teach your users not to open suspicious files and to open only those files that they’re reasonably sure are virus free. They need to scan every disk, email, and document they receive before they open them. You should also have all workstations scheduled to be automatically scanned on a regular basis.
Principle of Least Privilege
The concept of least privilege is a simple one: When assigning permissions, give users only the permissions they need to do their work and no more. This is especially true with administrators. Users who need administrative-level permissions should be assigned two accounts: one for performing nonadministrative, day-to-day tasks and the other to be used only when performing administrative tasks that specifically require an administrative-level user account. Those users should be educated on how each of the accounts should be used.
The biggest benefit to following this policy is the reduction of risk. The biggest headache with following this policy is trying to deal with users who may not understand it. Managers, for example, may assert that they should have more permission that those who report to them, but giving those permissions to them also opens up all the possibilities for inadvertently deleting files, misconfiguring resources, and so on.
A least privilege policy should exist, and be enforced, throughout the enterprise. Users should have only the permissions and privileges needed to do their jobs and no more. The ISO standard 27002 (which updates 17799) sums it up well: “Privileges should be allocated to individuals on a need-to-use basis and on an event-by-event basis, i.e., the minimum requirement for their functional role when needed.” Adopting this as the policy for your organization is highly recommended.
