Common Security Threats
In the following sections, we discuss a number of very important topics that fall into the realm of two broad categories: social engineering and malware. We’ll look at these topics as well as some of the reasons your network is vulnerable. The discussion is far from inclusive because new variants of malware and social engineering attacks are being created by miscreants on a regular basis. We will cover, however, everything CompTIA expects you to know for the exam.
Social Engineering
Social engineering is a process in which an attacker attempts to acquire information about your network and system by social means, such as talking to people in the organization. A social engineering attack may occur over the phone, by email, or in person. The intent is to acquire access information, such as user IDs and passwords. When the attempt is made through email or instant messaging, this is known as phishing (discussed later), and it’s often made to look as if a message is coming from sites where users are likely to have accounts (eBay and PayPal are popular).
These are relatively low-tech attacks and are more akin to con jobs. Take the following example: Your help desk gets a call at 4:00 a.m. from someone purporting to be the vice president of your company. They tells the help desk personnel that they are out of town to attend a meeting, their computer just failed, and they are sitting in a FedEx office trying to get a file from their desktop computer back at the office. They can’t seem to remember their password and user ID. They tell the help desk representative that they need access to the information right away or the company could lose millions of dollars. Your help desk rep knows how important this meeting is and gives the user ID and password over the phone. At this point, the attacker has just successfully socially engineered an ID and password that can be used for an attack.
Another common approach is initiated by a phone call or email from someone who pretends to be your software vendor, telling you that they have a critical fix that must be installed on your computer system. It may state that if this patch isn’t installed right away, your system will crash and you’ll lose all your data. For some reason, you’ve changed your maintenance account password and they can’t log on. Your system operator gives the password to the person. You’ve been hit again.
In Exercise 17.1, you’ll test your users to determine the likelihood of a social engineering attack. The steps are suggestions for tests; you may need to modify them slightly to be appropriate at your workplace. Before proceeding, make certain your manager knows that you’re conducting such a test and approves of it.
Malware
We’ve all been battling malicious, invasive software since we bought our first computers. This software can go by any number of names—virus, malware, and so on—but if you aren’t aware of its presence, these uninvited intruders may damage the data on your hard disk, destroy your operating system, and possibly spread to other systems.
Make certain your systems, and the data within them, are kept as secure as possible by using antivirus and antispyware programs. Doing so prevents others from changing the data, destroying it, or inadvertently harming it.
Rootkits
Rootkits have become the software exploitation program du jour. Rootkits are software programs that have the ability to hide certain things from the operating system; they do so by obtaining (and retaining) administrative-level access. With a rootkit, there may be a number of processes running on a system that don’t show up in Task Manager, or connections that don’t appear in a Netstat display may be established or available—the rootkit masks the presence of these items. It does this by manipulating function calls to the operating system and filtering out information that would normally appear.
Unfortunately, many rootkits are written to get around antivirus and antispyware programs that aren’t kept up-to-date. The best defense you have is to monitor what your system is doing and catch the rootkit in the process of installation.
Phishing
Phishing is a form of social engineering in which you simply ask someone for a piece of information that you are missing by making it look as if it is a legitimate request. An email might look as if it is from a bank and contain some basic information, such as the user’s name. These types of messages often state that there is a problem with the person’s account or access privileges. They will be told to click a link to correct the problem. After they click the link—which goes to a site other than the bank’s—they are asked for their username, password, account information, and so on. The person instigating the phishing can then use this information to access the legitimate account.

The only preventive measure in dealing with social engineering attacks is to educate your users and staff to never give out passwords and user IDs over the phone or via email or to anyone who isn’t positively verified as being who they say they are.
When you combine phishing with Voice over IP (VoIP), it becomes known as vishing and is just an elevated form of social engineering. While crank calls have been in existence since the invention of the telephone, the rise in VoIP now makes it possible for someone to call you from almost anywhere in the world, without the worry of tracing/caller ID/and other features of the land line, and pretend to be someone they are not in order to get data from you.
Two other forms of phishing to be aware of are spear phishing and whaling, and they are very similar in nature. With spear phishing, the attacker uses information that the target would be less likely to question because it appears to be coming from a trusted source. Suppose, for example, you receive a message that appears to be from your spouse and it says to click here to see that video of your children from last Christmas. Because it appears far more likely to be a legitimate message, it cuts through your standard defenses like a spear, and the likelihood that you would click the link is higher. Generating the attack requires much more work on the part of the attacker and often involves using information from contact lists, friend lists from social media sites, and so on.
Whaling is nothing more than phishing, or spear phishing, for so-called “big” users, thus the reference to the ocean’s largest creatures. Instead of sending out a To Whom It May Concern message to thousands of users, the whaler identifies one person from whom they can gain all the data they want—usually a manager or business owner—and targets the phishing campaign at them.
Shoulder Surfing
One form of social engineering is known as shoulder surfing and involves nothing more than watching someone when they enter their sensitive data. They can see you entering a password, typing in a credit card number, or entering any other pertinent information. The best defense against this type of attack is simply to survey your environment before entering personal data.
Spyware
Spyware differs from other malware in that it works—often actively—on behalf of a third party. Rather than self-replicating, like viruses and worms, spyware is spread to machines by users who inadvertently ask for it. The users often don’t know they have asked for it, but have done so by downloading other programs, visiting infected sites, and so on. In a replay attack, an expired certificate is being used repeatedly to gain logon privileges.
The spyware program monitors the user’s activity and responds by offering unsolicited pop-up advertisements (sometimes known as adware), gathers information about the user to pass on to marketers, or intercepts personal data such as credit card numbers.
Viruses
Viruses can be classified as polymorphic, stealth, retrovirus, multipartite, armored, companion, phage, and macro viruses. Each type of virus has a different attack strategy and different consequences.
The following sections will introduce the symptoms of a virus infection, explain how a virus works, and describe the types of viruses you can expect to encounter and how they generally behave. We’ll also discuss how a virus is transmitted through a network and look at a few hoaxes.
Symptoms of a Virus/Malware Infection
Many viruses will announce that you’re infected as soon as they gain access to your system. They may take control of your system and flash annoying messages on your screen or destroy your hard disk. When this occurs, you’ll know that you’re a victim. Other viruses will cause your system to slow down, cause files to disappear from your computer, or take over your disk space.
You should look for some of the following symptoms when determining if a virus infection has occurred:
- The programs on your system start to load more slowly. This happens because the virus is spreading to other files in your system or is taking over system resources.
- Unusual files appear on your hard drive, or files start to disappear from your system. Many viruses delete key files in your system to render it inoperable.
- Program sizes change from the installed versions. This occurs because the virus is attaching itself to these programs on your disk.
- Your browser, word-processing application, or other software begins to exhibit unusual operating characteristics. Screens or menus may change.
- The system mysteriously shuts itself down or starts itself up and does a great deal of unanticipated disk activity.
- You mysteriously lose access to a disk drive or other system resources. The virus has changed the settings on a device to make it unusable.
- Your system suddenly doesn’t reboot or gives unexpected error messages during startup.
This list is by no means comprehensive. What is an absolute, however, is the fact that you should immediately quarantine the infected system. It is imperative that you do all you can to contain the virus and keep it from spreading to other systems within your network, or beyond.
How Viruses Work
A virus, in most cases, tries to accomplish one of two things: render your system inoperable or spread to other systems. Many viruses will spread to other systems given the chance and then render your system unusable. This is common with many of the newer viruses.
If your system is infected, the virus may try to attach itself to every file in your system and spread each time you send a file or document to other users. Figure 17-3 shows a virus spreading from an infected system either through a network or by removable media. When you give removable media to another user or put it into another system, you then infect that system with the virus.
Figure 17-3: Virus spreading from an infected system using the network or removable media

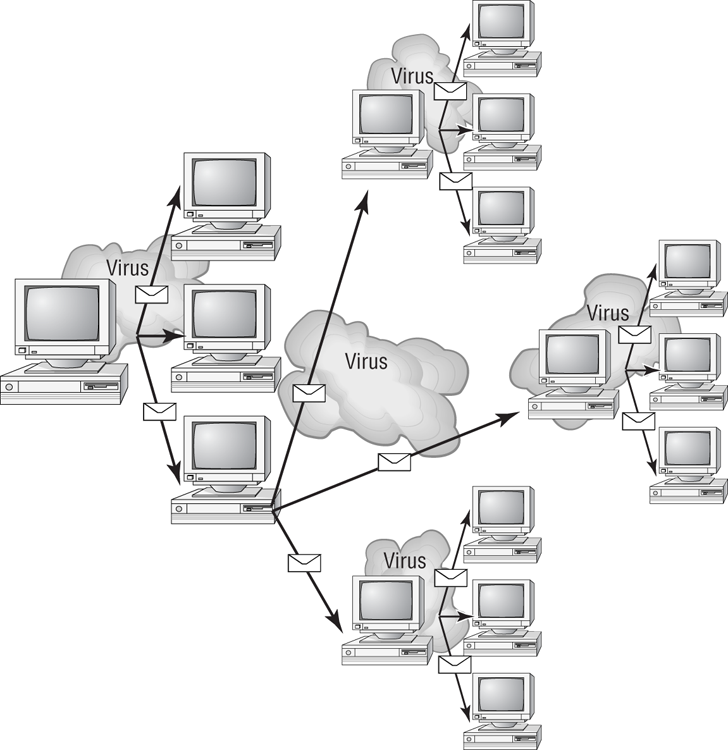
Many viruses today are spread using email. The infected system attaches a file to any email that you send to another user. The recipient opens this file, thinking it’s something you legitimately sent them. When they open the file, the virus infects the target system. The virus might then attach itself to all the emails the newly infected system sends, which in turn infects computers of the recipients of the emails. Figure 17-4 shows how a virus can spread from a single user to literally thousands of users in a very short time using email.
Types of Viruses
Viruses take many different forms. The following list briefly introduces these forms and explain how they work.
Figure 17-4: An email virus spreading geometrically to other users
These are the most common types of viruses, but this isn’t a comprehensive list:
Figure 17-5: A multipartite virus commencing an attack on a system
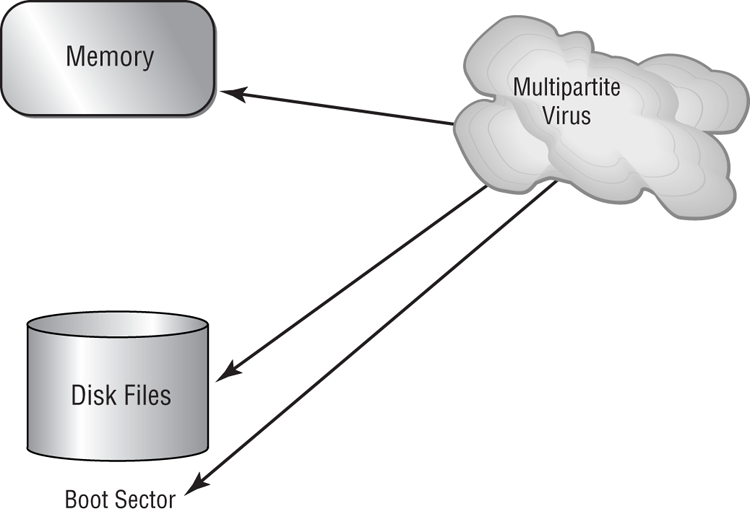
Figure 17-6: The polymorphic virus changing its characteristics
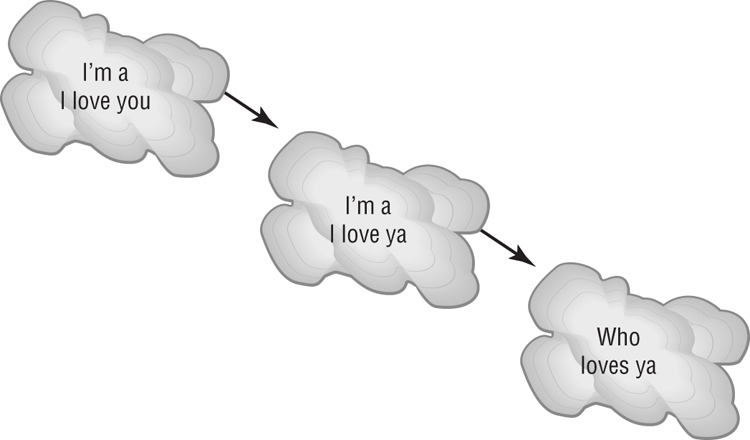
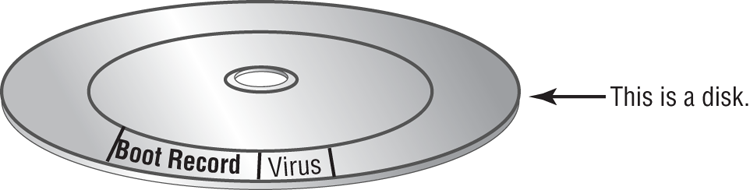
Figure 17-7: A stealth virus hiding in a disk boot sector
Virus Transmission in a Network
Upon infection, some viruses destroy the target system immediately. The saving grace is that the infection can be detected and corrected. Some viruses won’t destroy or otherwise tamper with a system; they use the victim system as a carrier. The victim system then infects servers, file shares, and other resources with the virus. The carrier then infects the target system again. Until the carrier is identified and cleaned, the virus continues to harass systems in this network and spread.
Worms
A worm is different from a virus in that it can reproduce itself, it’s self-contained, and it doesn’t need a host application to be transported. Many of the so-called viruses that have made the news were actually worms. However, it’s possible for a worm to contain or deliver a virus to a target system.
By their nature and origin, worms are supposed to propagate, and they use whatever services they’re capable of to do that. Early worms filled up memory and bred inside the RAM of the target computer. Worms can use TCP/IP, email, Internet services, or any number of possibilities to reach their target.
Trojans
Trojan horses are programs that enter a system or network under the guise of another program. A Trojan horse may be included as an attachment or as part of an installation program. The Trojan horse can create a back door or replace a valid program during installation. It then accomplishes its mission under the guise of another program. Trojan horses can be used to compromise the security of your system, and they can exist on a system for years before they’re detected.
The best preventive measure for Trojan horses is to not allow them entry into your system. Immediately before and after you install a new software program or operating system, back it up! If you suspect a Trojan horse, you can reinstall the original programs, which should delete the Trojan horse. A port scan may also reveal a Trojan horse on your system. If an application opens a TCP or UDP port that isn’t supported in your network, you can track it down and determine which port is being used.
