Troubleshooting Security Issues
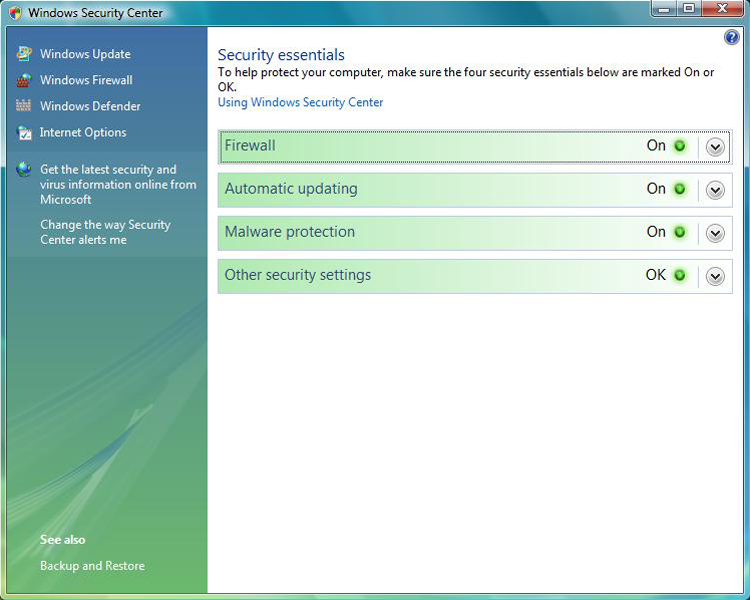
Many viruses will announce that your system is infected as soon as they gain access to it. They may take control of your system and flash annoying messages on your screen or destroy your hard disk. When this occurs, you’ll know that you’re a victim. Other viruses will cause your system to slow down, cause files to disappear from your computer, or take over your disk space. The Windows Security Center, shown in Figure 19-7, can show you what security measures are set on your system.
Figure 19-7: The Windows Security Center offers a quick glimpse of current protection settings.
You should look for some of the following symptoms when determining if a virus infection has occurred:
- The programs on your system start to load more slowly. This happens because the virus is spreading to other files in your system or is taking over system resources.
- Unusual files appear on your hard drive, or files start to disappear from your system. Many viruses delete key files in your system to render it inoperable.
- Program sizes change from the installed versions. This occurs because the virus is attaching itself to these programs on your disk.
- Your browser, word processing application, or other software begins to exhibit unusual operating characteristics. Screens or menus may change.
- The system mysteriously shuts itself down or starts itself up and a great deal of unanticipated disk activity occurs.
- You mysteriously lose access to a disk drive or other system resources. The virus has changed the settings on a device to make it unusable.
- Your system suddenly doesn’t reboot or gives unexpected error messages during startup.
- You notice an X in the system tray over the icon for your virus scanner, or the icon for the scanner disappears from the system tray altogether.
This list is by no means comprehensive. What is an absolute, however, is the fact that you should immediately quarantine the infected system. It is imperative that you do all you can to contain the virus and keep it from spreading to other systems within your network, or beyond. Many enterprises have a no-tolerance (zero tolerance) policy for infected systems and they are always flattened.
Common Symptoms
There are a number of common symptoms CompTIA expects you to know for the 220-802 exam when it comes to security issues. Many of these issues also appear in other CompTIA certification exams, namely Security+. Rest assured that for the 220-802 exam, you do not need to know the content as well as you would if you were preparing for the Security+ exam.
Pop-Ups
Pop-ups (also commonly known as popups) are both frustrating and chancy. When a user visits a website and another instance (either another tab or another browser window) is opened in the foreground, it is called a pop-up; if it opens in the background, it is called a pop-under. Both pop-ups and pop-unders are pages or sites that you did not specifically request and may only display ads or bring up applets that should be avoided.
Pop-up blockers are used to prevent both pop-ups and pop-unders from appearing. While older browsers did not incorporate an option to block pop-ups, most newer browsers, including the latest versions of Internet Explorer, now have that capability built in.
Browser Redirection
Pharming is a form of redirection in which traffic intended for one host is sent to another. This can be accomplished on a small scale by changing entries in the hosts file, and on a large scale by changing entries in a DNS server (poisoning). In either case, when a user attempts to go to a site, they are redirected to another. For example, suppose Illegitimate Company ABC creates a site to look exactly like the one for Giant Bank XYZ. The pharming is done (using either redirect method) and users trying to reach Giant Bank XYZ are tricked to going to Illegitimate Company ABC’s site, which looks enough like what they are used to seeing that they give username and password data.
As soon as Giant Bank XYZ realizes that the traffic is being redirected, it will immediately move to stop it. But while Illegitimate Company ABC will be shut down, it was able to collect data for the length of time the redirection occurred, which could vary from minutes to days.
Security Alerts
Users have plenty of real viruses and other issues to worry about. Yet some people find it entertaining to issue phony threats disguised as security alerts to keep people on their toes. Some of the more popular hoaxes that have been passed around are the Good Time and the Irina viruses. Millions of users received emails about these two viruses, and the symptoms sounded awful.
Both of these warnings claimed that the viruses would do things that are impossible to accomplish with a virus. When you receive a virus warning, you can verify its authenticity by looking on the website of the antivirus software you use, or you can go to several public systems. One of the more helpful sites to visit to get the status of the latest viruses is the CERT organization (www.cert.org). CERT monitors and tracks viruses and provides regular reports on this site.
When you receive an email you suspect is a hoax, check the CERT site before forwarding the message to anyone else. The creator of the hoax wants to create widespread panic, and if you blindly forward the message to co-workers and acquaintances, you’re helping the creator accomplish this task. For example, any email that includes “forward to all your friends” is a candidate for hoax research. Disregarding the hoax allows it to die a quick death and keeps users focused on productive tasks. Any concept that spreads quickly through the Internet is referred to as a meme.

Slow Performance
Slow performance was addressed previously in this chapter in relation to operating system issues. Viruses, worms, and other malware can slow performance because they rob resources from the other applications and services forced to share.
Internet Connectivity Issues
If your computer is hooked up to a network (and more and more computers today are), you need to know when your computer is not functioning on the network properly and what to do about it. In most cases, the problem can be attributed to either a malfunctioning network interface card (NIC) or improperly installed network software. The biggest indicator in Windows that some component of the network software is nonfunctional is that you can’t log on to the network or access any network service. To fix this problem, you must first fix the underlying hardware problem (if one exists) and then properly install or configure the network software.
PC Locks Up
It is obvious when a system lockup occurs. The system simply stops responding to commands and stops processing completely. System lockups can occur when a computer is asked to process too many instructions at once with too little memory. Usually, the cure for a system lock-up is to reboot. If the lockups are persistent, it may be a hardware-related problem instead of a software problem.

Windows Update Failures
Failed updates for Windows—assuming they are not caused by connectivity issues—can often be traced to setting misconfigurations. These settings can also cause the operating system to report that an update needs to be installed when it has already been installed. The best solution is to find the error code being reported in Windows Update Troubleshooter, solve the problem, and download the update.
For information on addressing this problem with both Windows Update and Microsoft Office, see the knowledge base article at http://support.microsoft.com/kb/906602.

Rogue Antivirus
One of the more clever ways of spreading a virus is to disguise it so that it looks like an antivirus program. When it alerts the user to a fictitious problem, the user then begins interacting with the program and allowing the rogue program to do all sorts of damage. One of the more tricky things for miscreants to do is make the program look as if it came from a trusted source—such as Microsoft—and mimic the Windows Security Center interface enough to fool an unsuspecting user.
Microsoft offers a page on fake virus alerts that can be helpful in sharing with employees to help educate them of what to be aware of at the following location:
http://www.microsoft.com/security/pc-security/antivirus-rogue.aspx

Spam
While spam is not truly a virus or a hoax, it is one of the most annoying things an administrator can contend with. Spam is defined as any unwanted, unsolicited email, and not only can the sheer volume of it be irritating, it can often open the door to larger problems. For instance, some of the sites advertised in spam may be infected with viruses, worms, and other unwanted programs. If users begin to respond to spam by visiting those sites, then viruses and other problems will multiply in your system.
Just as you can, and must, install good antivirus software programs, you should also consider similar measures for spam. Filtering the messages out and preventing them from ever entering the network is the most effective method of dealing with the problem. Recently, the word spam has found its way into other forms of unwanted messaging beyond email, giving birth to the acronyms SPIM (spam over Instant Messaging) and SPIT (spam over Internet Telephony).
Renamed System Files/Disappearing Files/Permission Changes/Access Denied
Creators of malware have a number of methods by which they can wreak havoc on a system. One of the simplest ways is to delete key system files. When this occurs, the user can no longer perform the operation associated with the file, such as print, save, and so on. Just as harmful as deleting a file is to rename it or change the permissions associated with it so the user can no longer access it or perform those operations.
Hijacked Email
One of the easiest ways to spread malware is to capture the email contacts of a user and send it as an attachment to all of those in their circle. The recipient is more likely to open the attachment because it seemingly comes from a trusted source.
Security Tools
Recovery Console, pre-installation environments, and Event Viewer were all discussed earlier in the chapter.
Antivirus Software
This type of preventive maintenance is absolutely critical these days if you have a connection to the Internet. A computer virus is a small, deviously ingenious program that replicates itself to other computers, generally causing those computers to behave abnormally. Generally speaking, a virus’s main function is to reproduce. A virus attaches itself to files on a hard disk and modifies those files. When the files are accessed by a program, the virus can infect the program with its own code. The program may then, in turn, replicate the virus code to other files and other programs. In this manner, a virus may infect an entire computer.
When an infected file is transferred to another computer (via disk or download), the process begins on the other computer. Because of the frequency of downloads from the Internet, viruses can run rampant if left unchecked. For this reason, antivirus programs were developed. They check files and programs for any program code that shouldn’t be there and either eradicate it or prevent the virus from replicating. An antivirus program is generally run in the background on a computer, and it examines all the file activity on that computer. When it detects a suspicious activity, it notifies the user of a potential problem and asks the user what to do about it. Some antivirus programs can also make intelligent decisions about what to do. The process of running an antivirus program on a computer is known as inoculating the computer against a virus.
There are two categories of viruses: benign and malicious. Benign viruses don’t do much besides replicate themselves and exist. They may cause the occasional problem, but it is usually an unintentional side effect. Malicious viruses, on the other hand, are designed to destroy things. Once a malicious virus (for example, the Michelangelo virus) infects your machine, you can usually kiss the contents of your hard drive goodbye.
To prevent virus-related problems, you can install one of any number of antivirus programs (Norton AntiVirus or McAfee VirusScan, for example). These programs will periodically scan your computer for viruses, monitor regular use of the computer, and note any suspicious activity that might indicate a virus. In addition, these programs have a database of known viruses and the symptoms each one causes.
Anti-Malware Software
There are many other forms of malware in addition to viruses. While a true antivirus program will scan for viruses, anti-malware programs are a superset of virus scanners and will look for more than just traditional viruses. One program included with Windows that falls into this category is Windows Defender, which is mainly a spyware detector (Microsoft Security Essentials is also available for Windows XP/Vista/7).
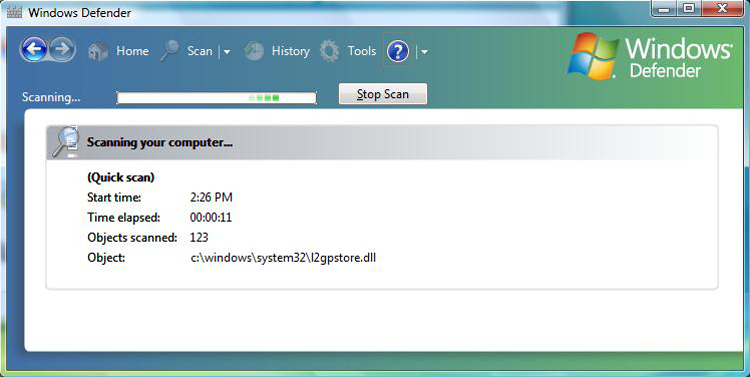
As with similar programs, for Windows Defender to function properly, you need to keep the definitions current and scan on a regular basis. In Exercise 19.3, you’ll run Windows Defender (shown in Figure 19-8) in Windows 7; Exercise 19.4 mirrors these actions using Windows XP.
Figure 19-8: Windows Defender can identify security threats.
Anti-Spyware Software
A subset of malware is spyware. Spyware differs from other malware in that it works—often actively—on behalf of a third party. Rather than self-replicating, like viruses and worms, spyware is spread to machines by users who inadvertently ask for it. The users often do not know they have asked for it but have acquired it by downloading other programs, visiting infected sites, and so on.
The spyware program monitors the user’s activity and responds by offering unsolicited pop-up advertisements (which fit into the category known as adware), gathers information about the user to pass on to marketers, or intercepts personal data such as credit card numbers. One thing separating spyware from most other malware is that it almost always exists to provide commercial gain. The operating systems from Microsoft are the ones most affected by spyware, and Microsoft has released Microsoft Security Essentials and Windows Defender to combat the problem. This spyware/adware interface works similar to most antivirus programs and uses a definition file that must be updated regularly to locate malware. You can also join the SpyNet community to help with isolating and reducing the problem. In Exercise 19.5, we’ll show you how to join the Microsoft SpyNet using Windows Defender.
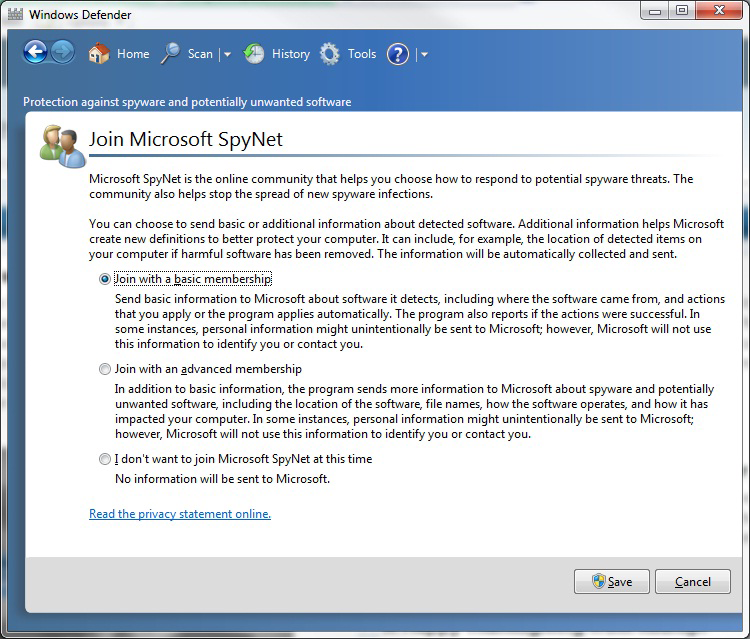
System Restore
There are times when bad things happen to good computers. No matter how hard you’ve tried to keep a system running flawlessly, your computer crashes. There are several ways to get your computer back up and running, but many of them (such as reinstalling the operating system) take a lot of time. A new feature called System Restore was introduced with Windows XP, and it allows you to create restore points to make recovery of the operating system easier.
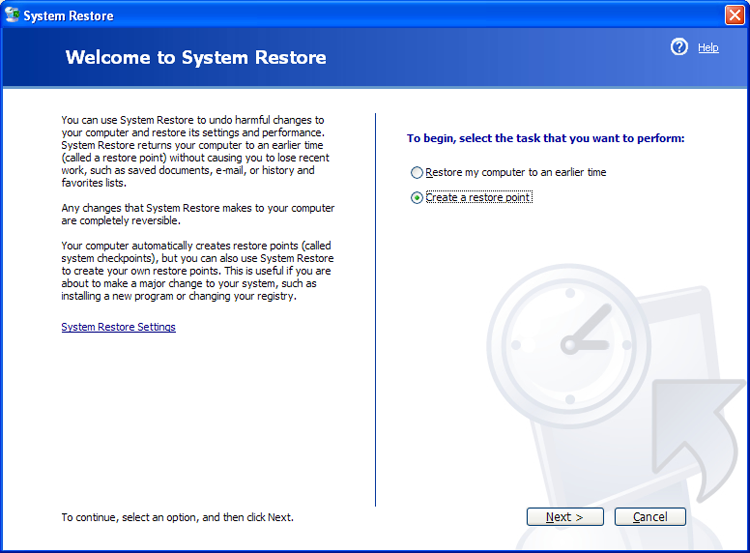
A restore point is a copy of your system configuration at a given point in time. It’s like a backup of your configuration but not necessarily your data. Restore points are created one of three ways. One, Windows creates them automatically by default. Two, you can manually create them yourself. Three, during the installation of some programs, a restore point is created before the installation (that way, if the install fails, you can “roll back” the system to a preinstallation configuration). Restore points are useful for when Windows fails to boot but the computer appears to be fine otherwise or if Windows doesn’t seem to be acting right and you think it was because of a recent configuration change.
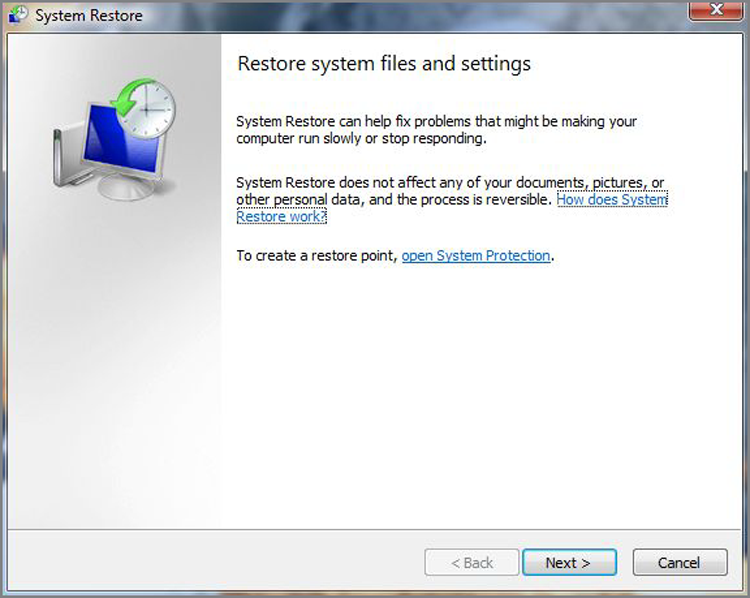
To open System Restore, click Start > All Programs > Accessories > System Tools > System Restore. It will open a screen like the one in Figure 19-9. By clicking Next, you can choose a restore point.
You’ll notice that checkpoints are included in the list of restore points along with backups that you have performed.
Creating a restore point manually is easy to do using the System Restore utility. In Exercise 19.6, we’ll walk through the process of creating a restore point in Windows Vista.
Figure 19-9: System Restore
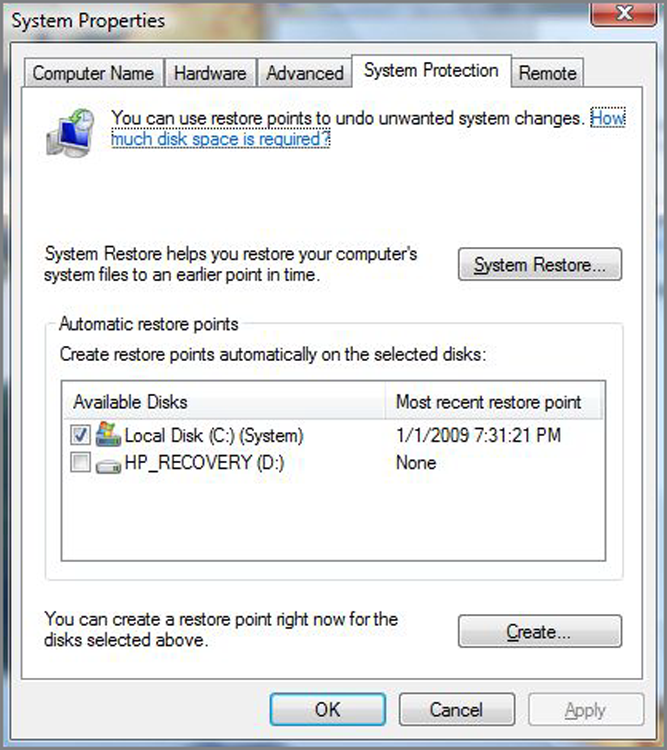
Exercise 19.7 shows you how to create restore points in Windows XP.
Best Practices of Malware Removal
Rounding out this chapter is a discussion of the best practices for malware removal. The best way to think of this is as a seven-item list of what CompTIA wants you to consider when approaching a possible malware infestation. The following discussion presents the information you need to know in just that fashion.
Together, these seven steps offer a best practices approach to confronting malware removal.
