Wireshark is an open source (GNU) tool used to capture and analyze network traffic. It is often used to troubleshoot Lync issues or to deep dive into the network traffic related to a specific feature. In addition to this, Wireshark adds to the standard debugging tools the capability to decrypt SSL/TLS traffic. It is really important for issues related to the Lync web services. We will see some hints related to installing and using it.
Wireshark is available for download at https://www.wireshark.org/. We will use the latest stable release, 1.12.0, on our Lync Front End (installed on Windows Server 2012 R2) by downloading the matching Windows installer (64 bit) Wireshark-win64-1.12.0.exe.
- Select Next on the first installation screen and the I Agree on the License Agreement screen.
- We have to select the components to install (the Wireshark 2 preview is not required), and select Next, as shown in the following screenshot:
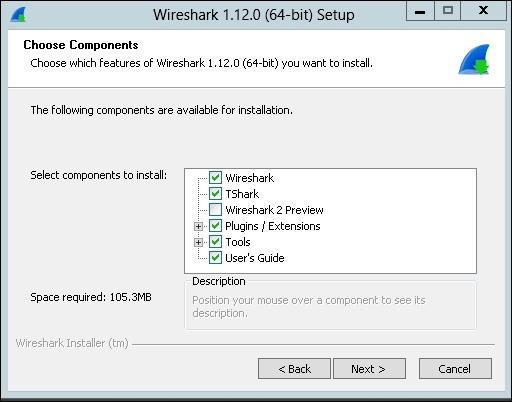
- In the Select Additional Tasks window, we are able to select the launch icons to create and the trace files associated to Wireshark. Click on Next, as shown in the following screenshot:
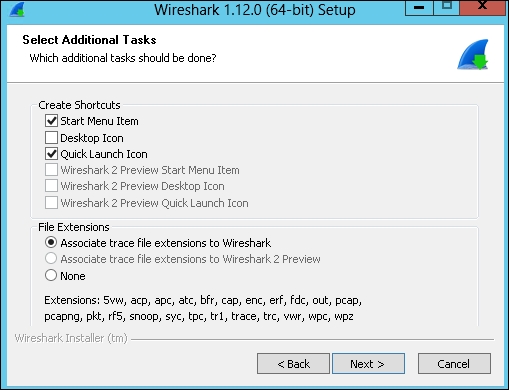
- Select an installation path and click on Next.
- Install WinPcap, as shown in the following screenshot. Without WinPcap, we cannot capture live network traffic but only open saved capture files.
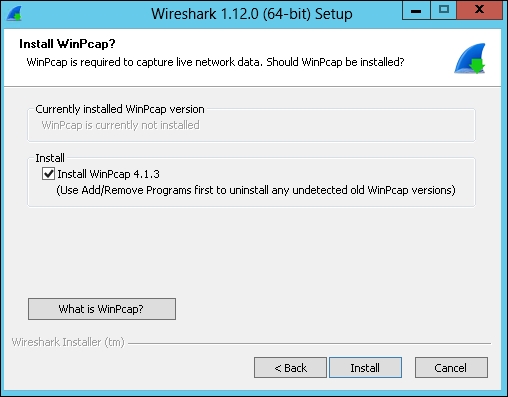
- The Wireshark and WinPcap installation will start. WinPcap will require additional confirmation regarding the installation path and startup mode.
- Launch Wireshark and select the interface for the capture, and then click on Capture Options, as shown in the following screenshot:
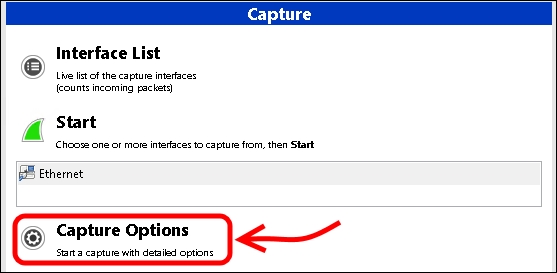
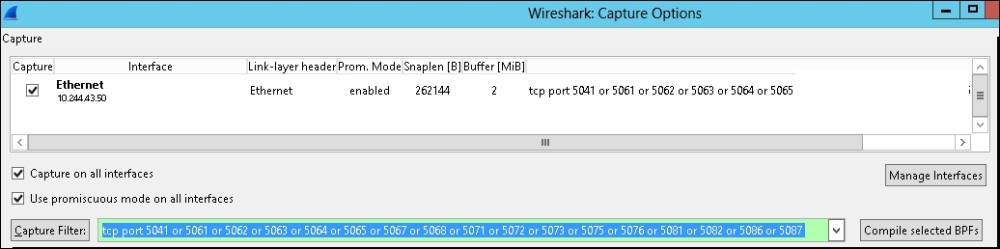
- An important decision that we have to take is whether we want to capture a large amount of network traffic and then filter it, or whether we prefer to filter traffic directly before displaying it in Wireshark. We have some predefined filters, and we are also able to define our custom selection. The default filters include IP, TCP only, and UDP only. To make use of additional filters, we will need to enter them using a specific syntax. For example, to filter all SIP-related traffic, we can use a string like
tcp port 5041 or tcp portrange 5061-5065 or tcp portrange 5067-5068 or tcp portrange 5071-5073 or tcp portrange 5075-5076 or tcp portrange 5081-5082 or tcp portrange 5086-5087.The following screenshot shows the Wireshark Capture Options screen:
- It is possible to save custom filters with a name inside Wireshark. We will see two different scenarios.
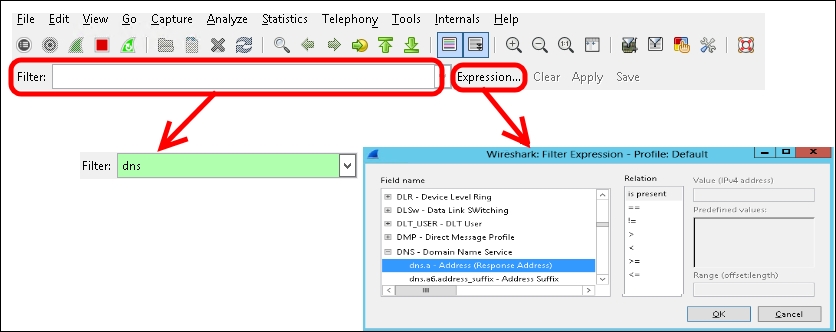
- Starting with a broad filter like IP, we have to apply a filter to see only the relevant results. The filter might be a simple one, like dns, or the network address of one of our servers, with a filter such as ip.addr == 192.168.1.10. We can also use the Expression… menu to select from many available options and to apply more complex filters, as shown in the following screenshot:
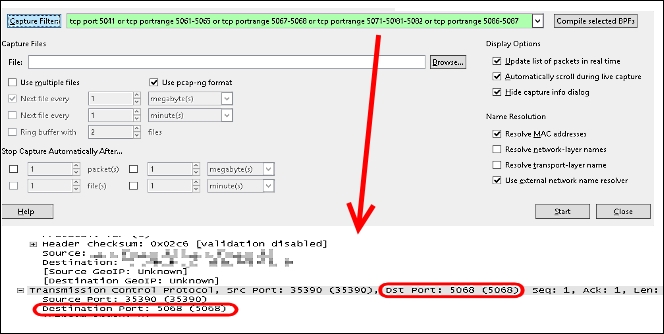
- Starting with a filter like the custom one that we have in the previous step, Wireshark will only show the network traffic that matches the filter, as shown in the following screenshot:
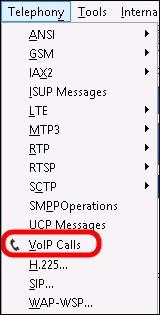
- If we are troubleshooting an Enterprise Voice issue, Wireshark has a Telephony dedicated menu, which includes a VoIP Calls option as shown in the following screenshot:
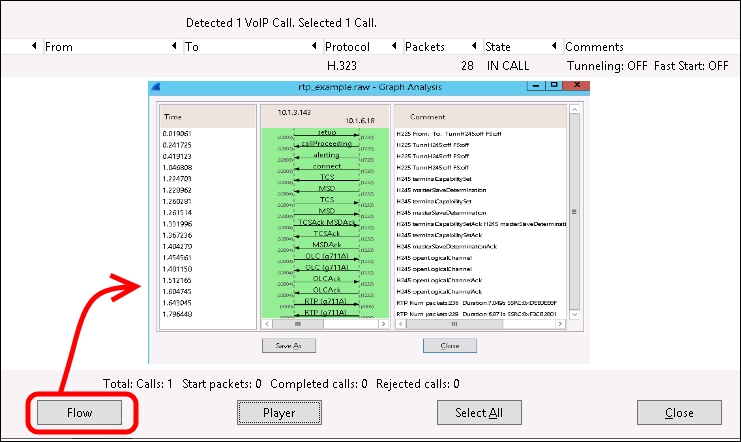
- The VoIP Calls screen contains two features, Flow and Player. The Flow feature is used to see the call flow as we did with the Snooper Flow Chart. This is shown in the following screenshot:
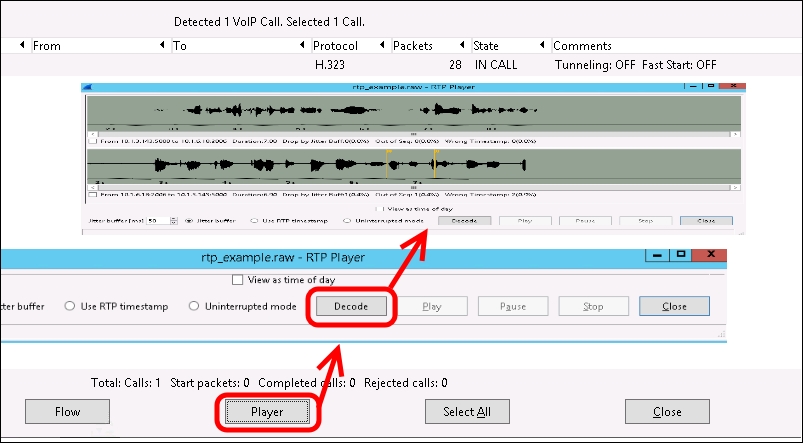
- The player will open a second window, enabling us to decode the call by using the Decode option and then, in a further window, to listen to it, as shown in the following screenshot:
To learn more about Wireshark hands-on, there is a useful page at http://wiki.wireshark.org/SampleCaptures, which contains a collection of samples that we can use to get some expertise with the tool.
James Cussen has developed an interesting addition for Wireshark, the Microsoft Lync Wireshark Plugin at http://www.mylynclab.com/2014/05/microsoft-lync-wireshark-plugin.html. This plugin is meant to help in capturing and decoding audio and video traffic that is entering and exiting from the Lync Edge. Some of the protocols involved are not completely standard and are not readable from Wireshark without some work that the plugin does for us.
Jonathan McKinney has outlined the process to make the Lync-encrypted traffic readable in Wireshark. The main point is to export the SSL certificate from Lync and import it inside the tool. We can read it in the Using Wireshark to Decrypt Lync Communications post at http://blog.lyncdialog.com/2013/11/using-wireshark-to-decrypt-lync.html.
- A good introduction to the use of Wireshark with Lync is the one written by Matt Landis, Getting Started With Lync and Wireshark: Tips & Quirks at http://windowspbx.blogspot.com/2013/11/getting-started-with-lync-and-wireshark.html.
