In this chapter, we will cover the following topics:
- Introduction
- Configuring passive authentication for Lync
- Enabling two-factor authentication
- Adding the app password for mobile clients
- Authenticating with online services using DirSync
- Managing Windows Azure Directory for Lync Online
- Configuring server-to-server authentication
- Troubleshooting with client authentication logging
Lync Server identity validation mechanisms are able to manage different kinds of personas, including authentication for a device, server, and user. The previously mentioned identities can require access to Lync in an on-premises datacenter, in a public Cloud, or in a hybrid Cloud scenario. The shift from Lync deployments that span over a corporate network to more complex setups required identity verification instruments to be adequate. Windows 2012, Windows 2012 R2, Azure, and Office 365 support a number of solutions (such as DirSync and identity federation) that add flexibility to our design.
Lync Server 2013 is able to accept both Cloud identities (stored in the Cloud) and federated identities (stored and managed on-premises). Talking about Lync Server 2013 on-premises, we have support for the following different user authentication protocols:
- Kerberos v5 and NT LAN Manager (NTLM) are reserved for users with Active Directory credentials (Kerberos for users on the internal network and NTLM when the Lync users connect from an external network).
- While an older version of Lync for mobile supported only NTLM for authentication, today's mobile apps/clients use a more secure approach. The initial authentication can be NTLM or passive and the authentication process the client obtains a Lync client certificate from the Lync Certificate Provisioning Service on the Front End server. The certificate on the client will be used for reauthentication, reducing the exposure of Active Directory credentials.
- Anonymous users (with no Active Directory credentials) authenticate via the Digest protocol. Microsoft has also added support for passive authentication in Lync 2013.
- Kerberos is available to external users as well if they connect through a VPN. Using a VPN, however, has some limitations, including a high overhead that could impact audio and video quality.
- Passive authentication (added with Microsoft Lync 2013 for Mobile release 5.2) uses form-based authentication built on Active Directory Federation Services (AD FS). Passive authentication is really interesting from a security point of view because the password is no longer entered on the mobile client. The user signs in by typing only their Lync address and then gets redirected to AD FS for authentication.
Adding services from the Cloud (Azure and Office) 365, we are able to add security and authentication options:
- Same Sign On and Single Sign On, based on DirSync and AD FS. Both the scenarios allow us to insert our on-premises domain account information once and also use it in the cloud.
- Two-factor authentication (like smart cards) adds a layer of security. It is available only for Lync Online users but can be implemented for on-premises using third-party integration (for example, see this post Lync Passive Authentication with two-factor authentication – Part II at http://techmikal.com/2014/02/27/lync-passive-authentication-with-two-factor-authentication-part-ii/).
- App passwords and an additional security option for Office 365 are used to replace the account password.
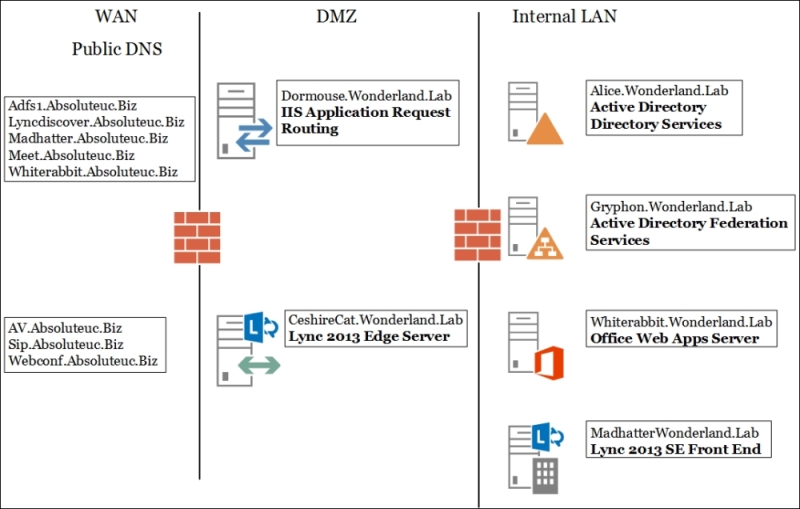
We will see passive authentication, Same Sign-On and Single Sign-On, two factors authentication, and app passwords in specific paragraphs of this chapter. Before we start with the various recipes, we should take a look at the following schema that outlines the lab environment we have used: