In 2013, the July cumulative update for Lync Server 2013 added two-factor authentication for the Lync 2013 client. As we mentioned in the introduction, the feature is available for Lync Online users, while on-premises deployment requires you to add a third-party solution. Two-factor authentication is based on the "something you know, something you have" principle, meaning that knowing a user's password without having an additional security item (a smart card) will not give access to Lync. An additional method could be based on "something you have" (a trusted device). We will see how to configure Office 365 (Lync Online) support for Multi-Factor Authentication (MFA). Office 365 MFA is a scaled-down version of Azure Multi-Factor Authentication service available to support both Azure and on-premises deployments. We will talk about it in the There's more… section.
- Log on to the Office 365 portal and go to Users and Groups | Active users and select Set Up to the right of Set Multi-factor Authentication Requirements, as we can see in the next screenshot:
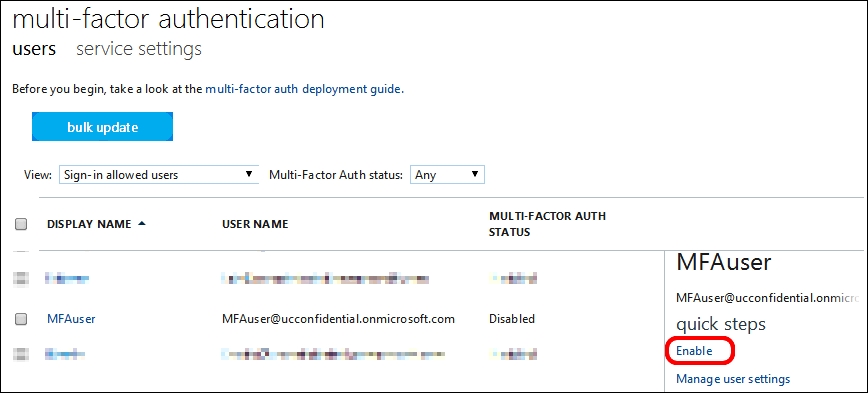
- Select the user that will use the Multi-Factor Authentication and select Enable.
- We will receive an About enabling multi-factor auth screen that requires a confirmation. Select the Enable Multi-Factor Auth button, as shown in the following screenshot:
- Select Close in the Updates Successful screen.
- The Manage User Settings option enables us to force the user settings related to MFA with the Require selected users to provide contact methods again and Delete all existing app passwords generated by the selected users features.
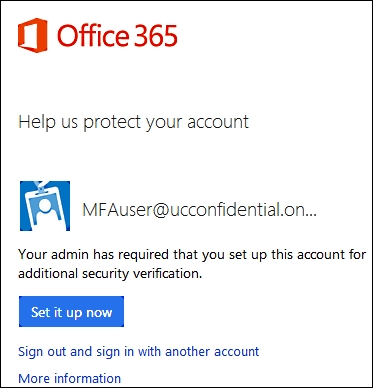
- The next time the user tries to log on to Office 365, they will receive a request to set up this account for additional security verification, as we can see in the following screenshot:
- There are three available options shown in the following screenshot: Mobile phone, Office phone, and Mobile app. Each one of them requires additional parameters (like a mobile number) to work.

- The device will be verified with a call or a text message.
- The next time the user logs on to the Office 365 portal, after the account and password screen, there will be an additional verification based on the selected additional security method.
Azure Multi-Factor Authentication (MFA) is an interesting service, and it is important to say that it can be deployed also in an on-premises environment. Azure MFA includes options for one-time passwords (generated with the MFA app), phone calls, and text messages. Now, we need to perform the following steps:
- We will need to access the Azure Portal (as explained in the Managing Windows Azure Directory for Lync Online recipe).
- From the directory management portal, we have to launch Enable multi-factor authentication, as we can see in the following screenshot:
- The lower bar will show a completed operation notification, like the one shown in the following screenshot:
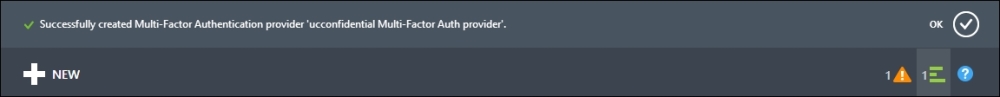
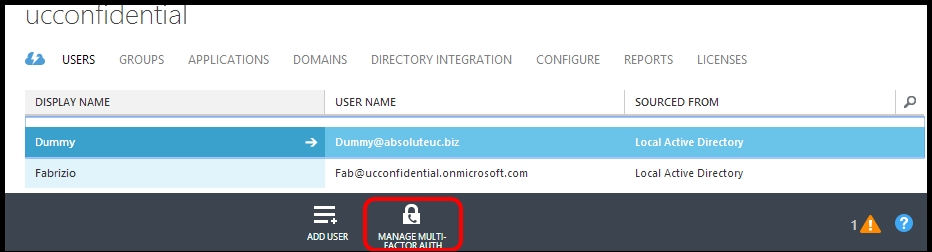
- In the lower part of the USERS tab, we have the MANAGE MULTI-FACTOR AUTH icon:
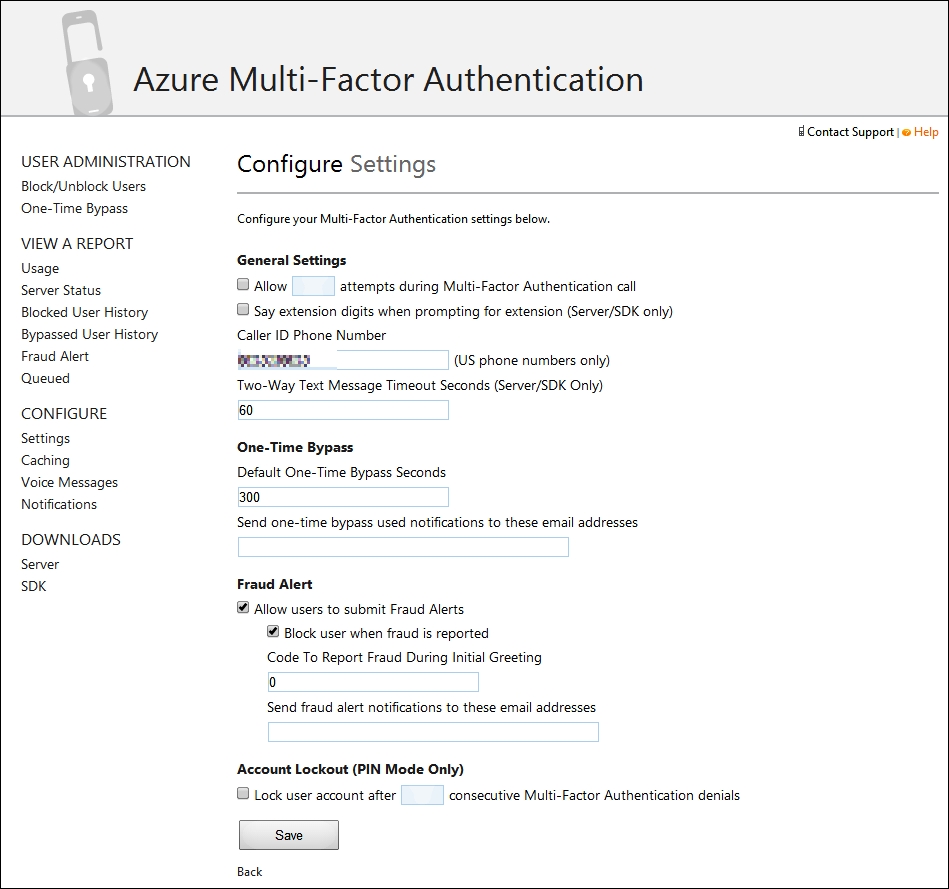
- As soon as the Multi-Factor Authentication provider for the selected domain is created, we are able to configure the settings for MFA. As we can see in the following screenshot, the feature is richer than the one we saw in Office 365:
Note
Azure has two MFA usage models Per Authentication and Per Enabled User, and both of them have an associated cost. The costs are explained in the Active Directory pricing details page (http://bit.ly/1fspdhz).
