Manage Auditing and Audit Reports
The ability to record and report the actions that users take in SharePoint is vital for establishing a strong monitoring plan for SharePoint. As an example of where this applies, consider that if the item is deleted and then purged by SharePoint after 30 days (which is the default) there would be no record of who had deleted the item once it is no longer in the recycle bin. Another example is monitoring who has viewed or opened a file but not modified it. In situations where it must be established whether a person had gained access to certain information, this record becomes invaluable. The SharePoint 2010 auditing feature allows administrators to capture user actions on sites, including the lists, libraries, and pages in the site. You can also generate reports on this information filtered by the type of action, the date range in which it occurred, and the user who performed it.
In Chapter 12, “Configuring Records Management,” we looked at one way of configuring auditing on content through setting up information management policies. That method is designed to allow record managers to define auditing on specific libraries and content types when they have either list management or site ownership permissions. From the point of view of establishing comprehensive auditing coverage, SharePoint also allows site collection administrators to enable auditing on an entire site collection.
Configuring Site Collection Auditing
Each organization will decide differently which items to audit. Bear in mind that the more you collect in the audit logs, the more space it will consume and the larger the log reports will be. Here are some general guidelines:
Standard Business Environment This would characterize a typical small to mid-sized business where a limited number of users have access to the network and little of the information is sensitive or subject to compliance regulations. This type of environment will most likely give many users read and edit rights to larger areas of content and there is little concern over who reads and edits documents they have rights to. The primary concern would be tracking misplaced or deleted data and monitoring security settings.
What to audit:
- Moving or copying items to another location in the site
- Deleting or restoring items
- Editing users and permissions
Enterprise Business Environment At times, large organizations face the problem of needing to recover the history of a document that has been moved and copied multiple times through its life cycle. If a file is moved from a library with versioning turned on to a library without versioning, then the history of changes to that document will be lost. The primary concern would be tracking the historical actions on a document and being able to report on activities that modify data.
What to audit:
- Editing items
- Checking out or checking in items
- Moving or copying items to another location in the site
- Deleting or restoring items
- Editing users and permissions
High-Security Environment Where the information in SharePoint is sensitive in nature—such as legal files, medical records, or intellectual property—it is advisable to audit all access to the content, including reading and viewing it. This may even apply to the search queries that users execute, since they may be part of a pattern of an employee seeking unauthorized information.
What to audit:
- Editing items
- Checking out or checking in items
- Moving or copying items to another location in the site
- Deleting or restoring items
- Searching site content
- Editing users and permissions
In some high-security environments, it may also be necessary to audit the following:
- Opening or downloading documents
- Viewing items in lists
- Viewing item properties
Auditing these activities will generate a high number of log entries and can use a large amount of database space. We recommend that you only enable this option after careful consideration and planning.
There are two additional settings not included in the environment categories just described:
- The ability to track editing content types and columns is used when an organization has implemented a highly structured metadata taxonomy that is used as part of a regulatory compliance requirement. Changes to the content types or columns may violate compliance, so these changes should be audited.
- Any changes made to the audit settings themselves are automatically logged and available through audit reports.
To configure auditing on an entire site collection:
1. Navigate to the home page at the root of a site collection for which you are the site collection administrator.
2. Select Site Actions, then Site Settings.
3. In the Site Collection Administration section, click Site Collection Audit Settings. The Configure Audit Settings page opens, shown partially in Figure 15.1.
Figure 15.1: Configure Audit Settings page
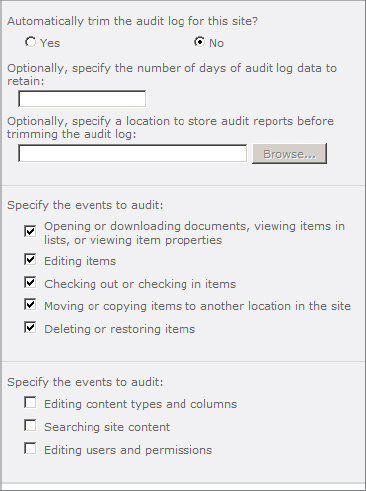
4. Optionally, set the log trimming settings. See the next section, “Managing Audit Log Growth and Size,” for details.
5. Choose the events to audit
6. Click OK.
Managing Audit Log Growth and Size
SharePoint stores all audit entries in the content database table AuditData. By default, SharePoint does not delete entries in this table and the table can grow significantly over time. This was a notable problem with SharePoint 2007 farms where many administrators found that the AuditData table became larger than any of the other tables that stored site content.
To estimate the amount of data that you are likely to log, a good approach is to perform a baseline series of actions on the site to simulate a typical user during a period of the workday, then count the number of log entries that adds to the AuditData table. You can then multiply this baseline by the number of users who will be using SharePoint and the length of a typical workday to yield a rough estimation of the number of log entries per day. Log entries range from 1 KB to 4 KB in size, but 2 KB is used as a typical average size for estimation purposes.
Depending on your internal policies, it may not be necessary to keep all log entries. To minimize the growth in the content database, SharePoint 2010 allows you to periodically trim the audit log and, optionally, save copies of the entries before they are deleted. SharePoint is configured with a timer job named Audit Log Trimming, which is scheduled to run once per month by default. This schedule can be adjusted by the farm administrator if desired.
To configure audit log trimming:
1. Follow steps 1–3 in the previous section, “Configuring Site Collection Auditing” and refer to Figure 15.1.
2. Click the Yes option at the “Automatically trim the audit log for this site?” prompt.
3. Optionally, enter the number of days of log history to retain in the database when the timer job runs. By default, the site collection will be purged.
4. Optionally, specify a document library in which to store deleted log entries before trimming. To do so, click the Browse button and select the library you want to use.
5. Click OK.
NOTE If you store audit reports, they continue to take space in the content database. To reclaim the space, you must download the reports from the library and delete them from SharePoint.
Viewing Audit Reports
Site collection administrators can run a number of reports to display audit details in Excel 2010 format.
To view and run reports:
1. Navigate to the home page at the root of a site collection for which you are the site collection administrator.
2. Select Site Actions, then Site Settings.
3. In the Site Collection Administration section, click Audit Log Reports.
NOTE The Audit Log Reports link is enabled via a site collection feature. If you do not see the link, then click the Site Collection Features link and activate the Reporting feature.
On the View Auditing Reports page, the following reports are available:
Content Modifications Any changes made to items such as checking out, checking in, and editing.
Content Type And List Modifications Any changes to content types in the site collection.
Content Viewing Opening documents or viewing items and properties.
Deletion Any items or lists deleted or restored from the recycle bin.
Run A Custom Report Filtered report displaying data for a specific location, date range, user, or action type.
Expiration And Disposition Any automated deletion or processing of items by an information management policy.
Policy Modifications Any changes to information management policies.
Auditing Settings Any changes to auditing settings.
Security Settings Any changes to users, groups, permission levels, and permission assignments.
4. Click one of the report links; then in the Save Location box, browse for the document library that you want the report placed into when it is generated.
5. Click OK.
The report is generated as an XLSX file and placed in the designated library. The results page contains a link to open the report directly.
An example of a section of a Content Modifications report is shown in Figure 15.2.
Figure 15.2: Audit report details
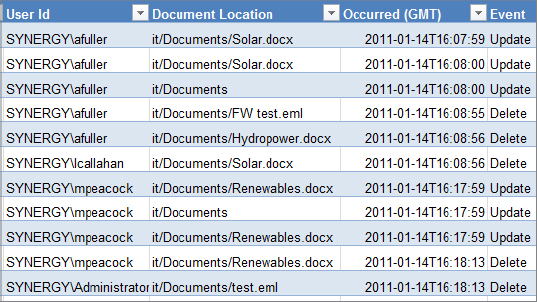
Each audit report contains the following information about user activities:
Site ID GUID of the site collection where the action occurred
Item ID GUID of the item
Item Type Values include Site Collection, Site, List, Document, and Item
User ID Authentication account that performed the action
Document Location Relative URL of the item or document within the site collection
Occurred (GMT) Date and time of the action in Greenwich Mean Time
Event Type of event, such as Edit or Delete
Custom Event Name Additional information about the action
Event Source Usually has a value of SharePoint
Event Data Details about the action, such as the version number of the document checked in
Audit reports contain a concise listing of information that provides the essential details in a relatively raw format. Some information is not provided in a readily usable form. For example, the site collection and item are identified through their GUID rather than their URL; the date and time are reported in GMT rather than the local time zone where the report is run; and the user account is represented as the login rather than the full name of the user. It is best to consider the audit reports generated by SharePoint as data exports rather than as presentable reports found in other areas of the application. Third-party add-ins are available from SharePoint market vendors that generate fully formatted reports.
