In the previous example, the TDSS rootkit DLL performed a check to see if it is running under spoolsv.exe. We modified the bytes in the program so that the DLL can run under notepad.exe instead of spoolsv.exe. What if you wanted to reverse the logic so that DLL can run under any process (other than spoolsv.exe)? To do that, we can change the jnz instruction to jz by selecting Edit | Patch program | Assemble, as shown in the following screenshot. This will reverse the logic and cause the program to return from the function without exhibiting any behavior when the DLL is running under spoolsv.exe. Whereas when the DLL is running under any other process, it exhibits malicious behavior. After changing the instructions, when you click on OK, the instruction is assembled but the dialog remains open, prompting you to assemble another instruction at the next address. If you do not have any more instructions to assemble, you can click the Cancel button. To make the changes to the original file, select Edit | Patch program | Apply patches to input file and follow the steps mentioned previously:
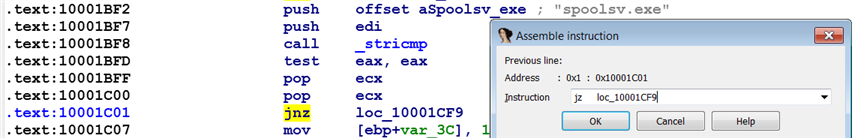
When you are patching an instruction, care needs to be taken to make sure that the instruction alignment is correct; otherwise, the patched program may exhibit unexpected behavior. If the new instruction is shorter than the instruction you are replacing, then nop instructions can be inserted to keep the alignment intact. If you are assembling a new instruction that is longer than the one that is being replaced, IDA will overwrite the bytes of the subsequent instructions, which may not be the behavior you want:
